In today’s business environment, data is everywhere – structured or unstructured, at rest or in motion – it flows throughout information gateways, websites, and web applications, is shared through instant messaging and collaboration systems like Microsoft SharePoint, and “sleeps” in data repositories, databases, and file shares. Understanding what and where this data is and properly classifying it will allow you to set the appropriate levels of protection in place.
In order to ensure it’s successful on all levels, a compliance program must include three important pillars:
- People
- Policies
- Technical Enforcement
With the latest release of AvePoint’s award winning Data Loss Prevention and Governance, Risk, and Compliance management platform Compliance Guardian Service Pack (SP) 3, organizations can address data within the context of the source and system from which it originates. With support for both structured and unstructured data, instant messaging tools, databases, and social collaboration platforms in your enterprise, you can now shed light on potential sources of risk.
People and Policies
With users around the globe throughout a wide range of industries including public sector, financial services, healthcare, energy, media and entertainment, and retail, Compliance Guardian SP 3 extends data discovery and Data Loss Prevention across the enterprise. Regardless of the system around which an organization is designing the compliance program, it is important to understand who within the organization is using it, why they are using it, as well as what kinds of privacy and information security requirements it is subject to by law, statute, or internal policy.
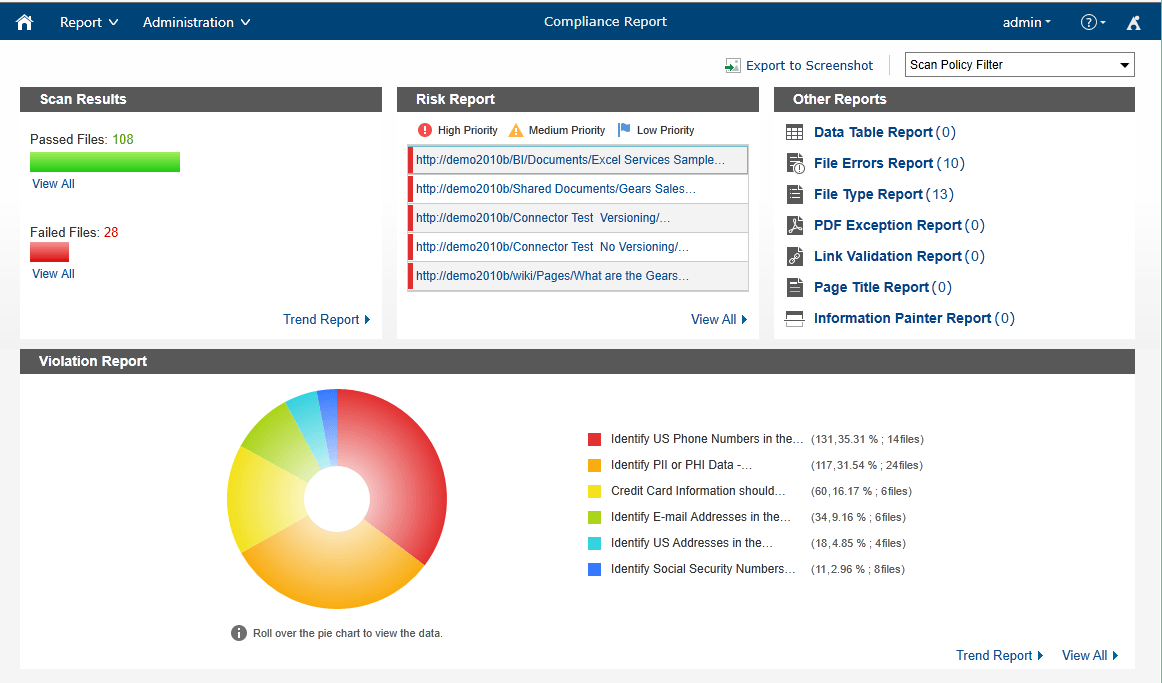
Compliance Guardian can assist with this discovery process, and the its audit reports provide actionable information that assists with drafting and implementing an appropriate data governance and compliance policy that not only reflects the priorities of the business, but also implements practices, procedures, and protection. Compliance Guardian can assist with every step of this process, allowing you to ensure compliance with your policies.
Technical Enforcement
Once your polices have been drafted, Compliance Guardian provides technical enforcement in the following ways:
- Find the dark data where it lives – all across your enterprise and where you’re storing information. This covers critical need for data discovery.
- Drive enterprise classification and taxonomy across systems. Enterprise data classification not only improves data protection, but also enhances search and appropriate information sharing between and across business users, vendors, and customers within larger organizations. Compliance Guardian brings this kind of power and simplicity to the world of data protection and classification, with user-assisted tagging and automated classification.
- Scan content based on out-of-the-box or customized compliance check files mapping to a wide range of requirements and legislation for privacy, information assurance, operational security, sensitive security information, and accessibility.
- Tag sensitive data with an embedded metatag within the document to indicate the sensitivity level of that content.
- Block, quarantine, redact, encrypt, protect, and move sensitive content to a secure location to ensure appropriate access.
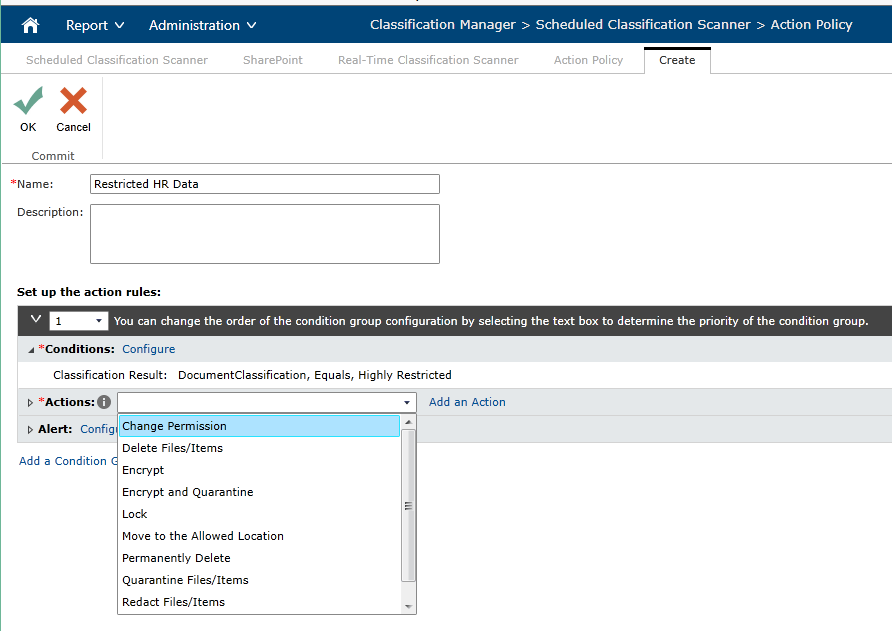
Compliance Guardian empowers you to resolve, report, and improve on incident tracking and incident management across your organization. The ability not only to conduct a detailed forensic analysis into data privacy, information security, and accessibility issues across your organization, but also to assign and expect accountability for incident resolution is a key factor in improving compliance over time. Compliance Guardian’s data-aware security policies provide an opportunity for organizations to build a more layered approach to security, prioritizing where efforts (and costs) should be spent, and building multiple lines of defense.
Want to see what Compliance Guardian can do for you? Visit our product page to learn more and sign up for a free personalized demo today.

