In today’s tech world, Microsoft 365 collaboration is the backbone of good business. This collaboration isn’t limited to internal coworkers; whether partners, vendors, contractors, customers, or any other external user, most enterprises and organizations need a way to work with external colleagues.
Fortunately, Microsoft offers multiple capabilities to enable external collaboration in your Microsoft 365 (M365) tenant. To ensure your security while taking advantage of these capabilities, you need to understand the nuances of each feature and how to safely enable and use them.
In this blog post, we’ll review four external collaboration options in M365 and when to use each.
1. External Sharing
What it is: External sharing allows your users to share content with users outside your organization. With this feature, your users can share individual files or entire libraries or sites.
When to use it: If you’re working on one-off projects and don’t anticipate further communication needs such as chats or meetings.

How to enable it: External sharing is enabled in your tenant by default. Admins can turn it on or off in the admin center under service settings > sites and documents sharing.
Keep in mind: Content can be shared via anonymous guest links or via a link requiring a sign-on. The sensitivity of the content will determine which is appropriate. M365 also provides many additional security and compliance features to protect your information while collaborating. Read more.
2. External Access
What it is: External access allows users of external domains to find, contact, and set up meetings with your team, and vice versa.
When to use it: If you are frequently communicating with external organizations, through chat or meetings, but do not want to grant them access to your content or tenant.
How to enable it: External access is enabled in your tenant for all domains by default. You can add or block domains in the Teams admin center under users > external access. Note: if you allow a specific external domain, all others will be blocked; if you block an external domain, all others will be allowed.
Keep in mind: External access is controlled at the domain level, not the individual user level. You can restrict external access by allowing or blocking specific domains, or by turning off external access.

3. Guest Access
What it is: Guest access grants outsiders access to your tenant through a Team or Group with nearly all the same capabilities as internal users, such as the ability to chat, call, meet, and collaborate on files. Note: guest users do not have all the same capabilities; read Microsoft’s comparison.
When to use it: If you have a consultant, vendor, partner, or other outsiders that you work with regularly and who needs access to many facets of your tenant, such as teams, documents in channels, chats, applications, and meetings.
How to enable it: Guest access is enabled by default in M365 and controlled at the individual user level. Admins must add net new guest users in their Azure portal, but once a user is in your Azure AD, admins can assign them to workspaces or Team or Group Owners can invite guests to their workspaces.
Keep in mind: Guest access must be carefully provisioned and configured, as you are granting an external user access to your tenant, from Teams channels to files in your SharePoint. Confirm your governance policies are enforced, that you are not vulnerable to oversharing, and your sensitive information is protected with solutions like AvePoint’s Policies and Insights.
4. Shared Channels
What it is: Shared channels are similar to private channels in that they provide an exclusive space for only approved members, but they offer more by allowing external users to easily participate, streamlining collaboration. External users do not need guest access or to be a member of the top-level Team to be added to a shared channel.
When to use it: If you are working on a large project, program, or event that involves multiple external users who will only need full access to the channel, but not other aspects of your tenant (which would require a guest account).
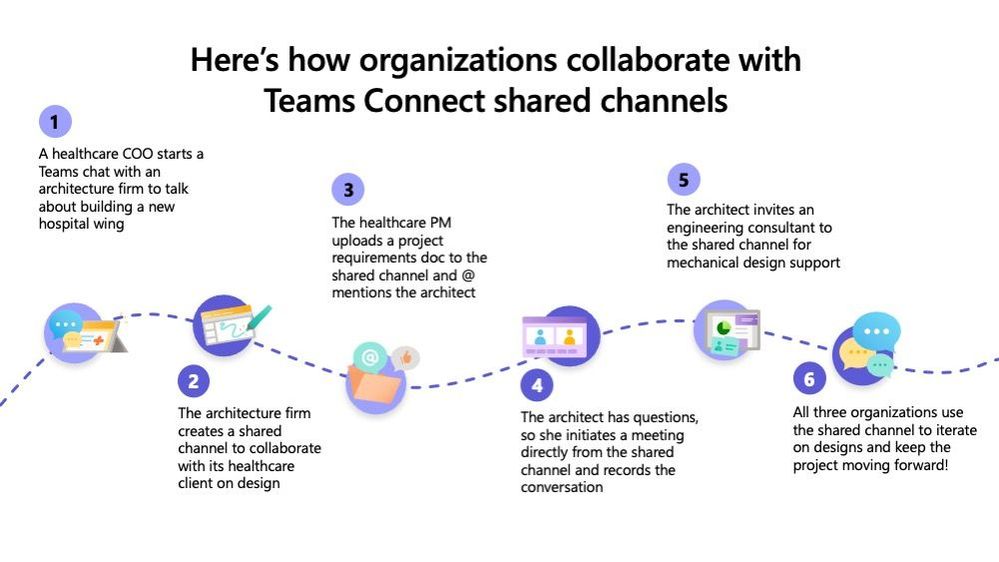
How to enable it: Shared channels must be enabled by configuring organizational relationships in Azure AD. Admins can turn them on separately for outbound and inbound.
Keep in mind: Shared channels streamline collaboration, offering member benefits without extensive provisioning, but they still must be used responsibly. Read more.
Conclusion
The reality is modern organizations don’t do everything alone; they rely on networks of outsiders to perform and execute various work tasks. While Microsoft offers a variety of capabilities to enable external collaboration, it’s important to understand the needs of these external users before you enable a capability to ensure you are not oversharing information, over privileging external users, or creating other security risks.
Once you decide which external collaboration features you will allow, set guidelines and rules for your users to follow and update your governance policies to protect your workspaces and mitigate any risks of external collaboration.
For a step-by-step guide on how to configure specific settings to meet your organization’s needs and external collaboration best practices, read our free eBook External Sharing and Guest User Access in Microsoft 365 and Teams.

