Miss the original External Sharing in Microsoft Teams webinar? Watch it on-demand here.
For most organizations, external sharing is necessary for collaboration. Office 365 provides very granular controls for getting it set up, but these controls are spread across different admin centers. This can cause admins to be apprehensive about implementing external sharing. Fortunately, we can help simplify this.
External sharing is like an onion. There are controls at a very high level that affect everything bellow. But as you get closer to individual Groups, Teams, and sites, there’s more granular control that you may not even be aware of yet.
When used correctly, sharing externally can be just as easy as sharing internally. When used incorrectly, however, it can cause a nightmare of sensitive data loss and oversharing. To avoid this scenario, we’ll go over the reality, the myths, and the risks of external sharing as well as how to configure external sharing and guest access for Microsoft Teams.

Table of Contents
Expectation vs. Reality
When it comes to enabling external sharing, there are a few pervasive fears:
- It opens the door for oversharing.
- Users might mishandle sensitive information.
- Resistance from the security team.
- Once an external user is in, how do you get them out?
However, the reality of this situation is that you are already sharing externally. But how?
Understanding Guest Access
Chances are your users will need to collaborate externally at some point or another. If you don’t have an established system for external sharing, you leave it up to your users to decide when and how this will take place. While you might not see the risk now, once data leaves your system, you no longer have control of where it ends up. Once external users have your data, do you really know what they’ll do with it?
Have questions around external sharing in Teams? This post is pretty helpful: Click To TweetWhere to Configure Guest Access and External Sharing
It’s important to know where and how to configure these in Azure AD, Microsoft Teams, SharePoint Online, and OneDrive for Business. Note that you may come across the term “external access” in your Teams Admin Center interface. There’s a subtle but critical terminology difference between external access versus guest access:
- External access (federation) gives access permission to an entire domain which will only give the participant access to one-on-one federated chat; they will have no access to the inviting organization’s Teams or Team resources.
- Guest access gives access permission to an individual who can then access resources such as channel discussions and files.
Since we want to establish external sharing in this case, our concern is enabling guest access.
Azure AD
As an Office 365 admin, you should have a link to the Azure Active Directory portal right from your admin center. Here, you can see your guest users, create new guest users, and manage your B2B guest user permissions settings.
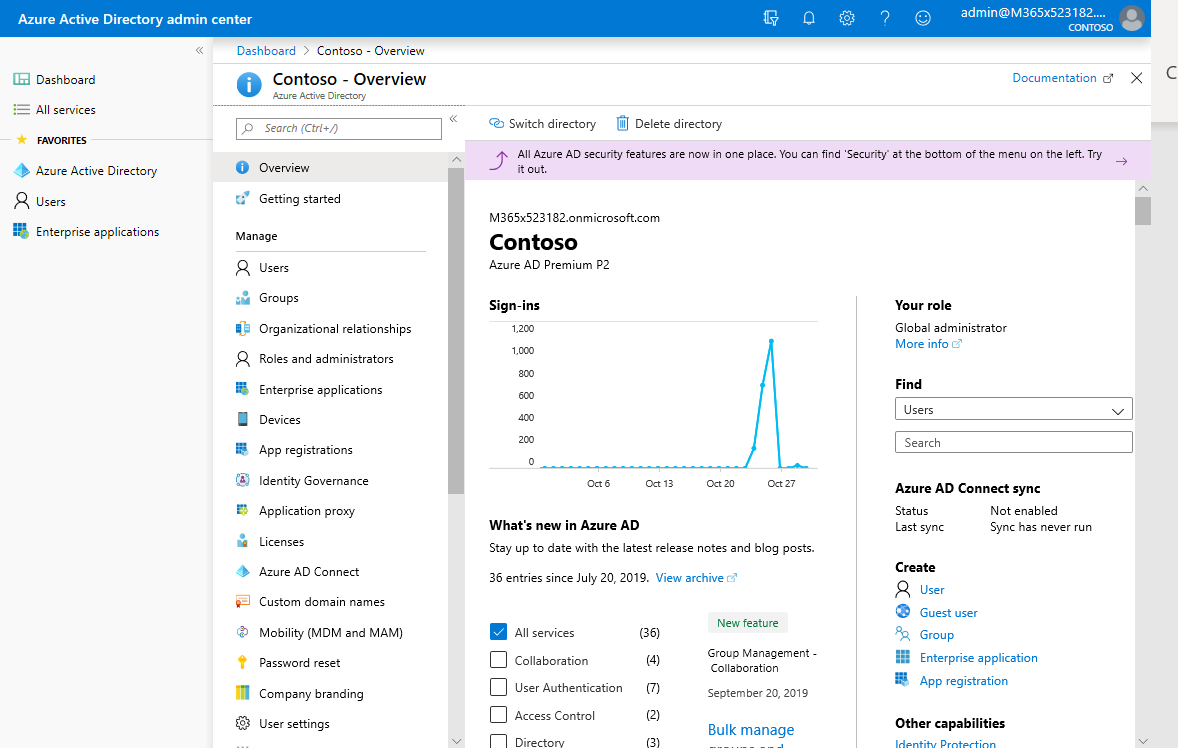
In your organizational relationships (aka B2B) settings you can take those controls even further. Do you want guest users to be able to browse the directory? Do you want to allow members or owners to invite guests? You can also find controls to enable a one-time email passcode for guests and collaboration restrictions on domains.
Microsoft 365 Admin Center
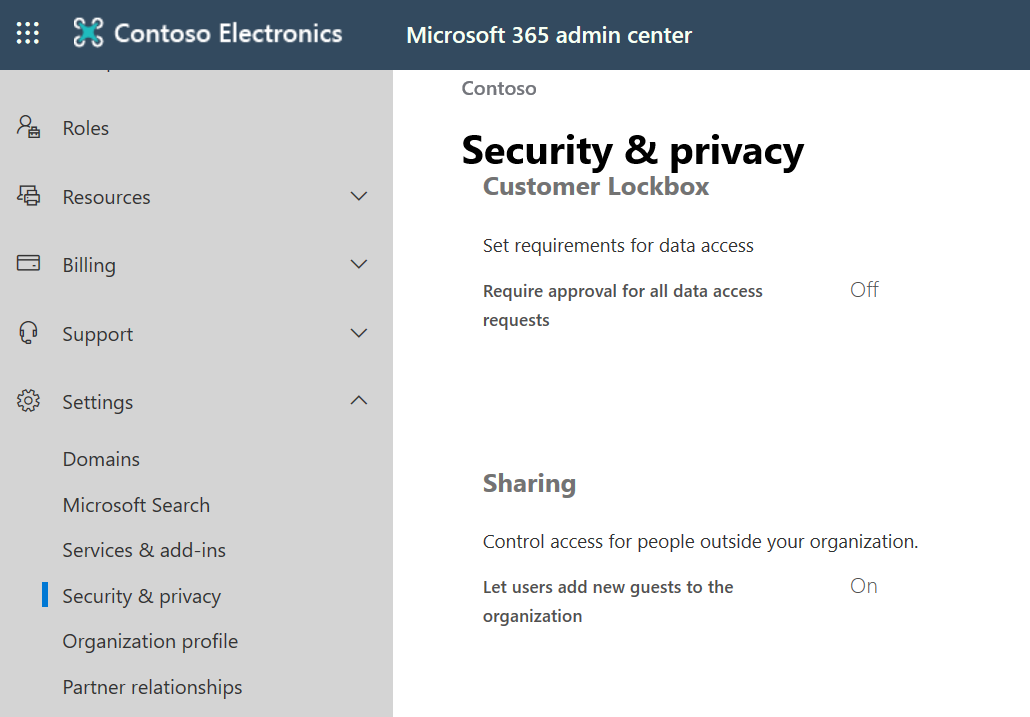
If you want external sharing in Microsoft Teams, the first step is to turn on external sharing for Office 365.
You can turn on your sharing settings by going to Microsoft 365 admin center → Settings → Security and privacy. With this turned on, you will also need to turn on sharing at the Office 365 Groups level.
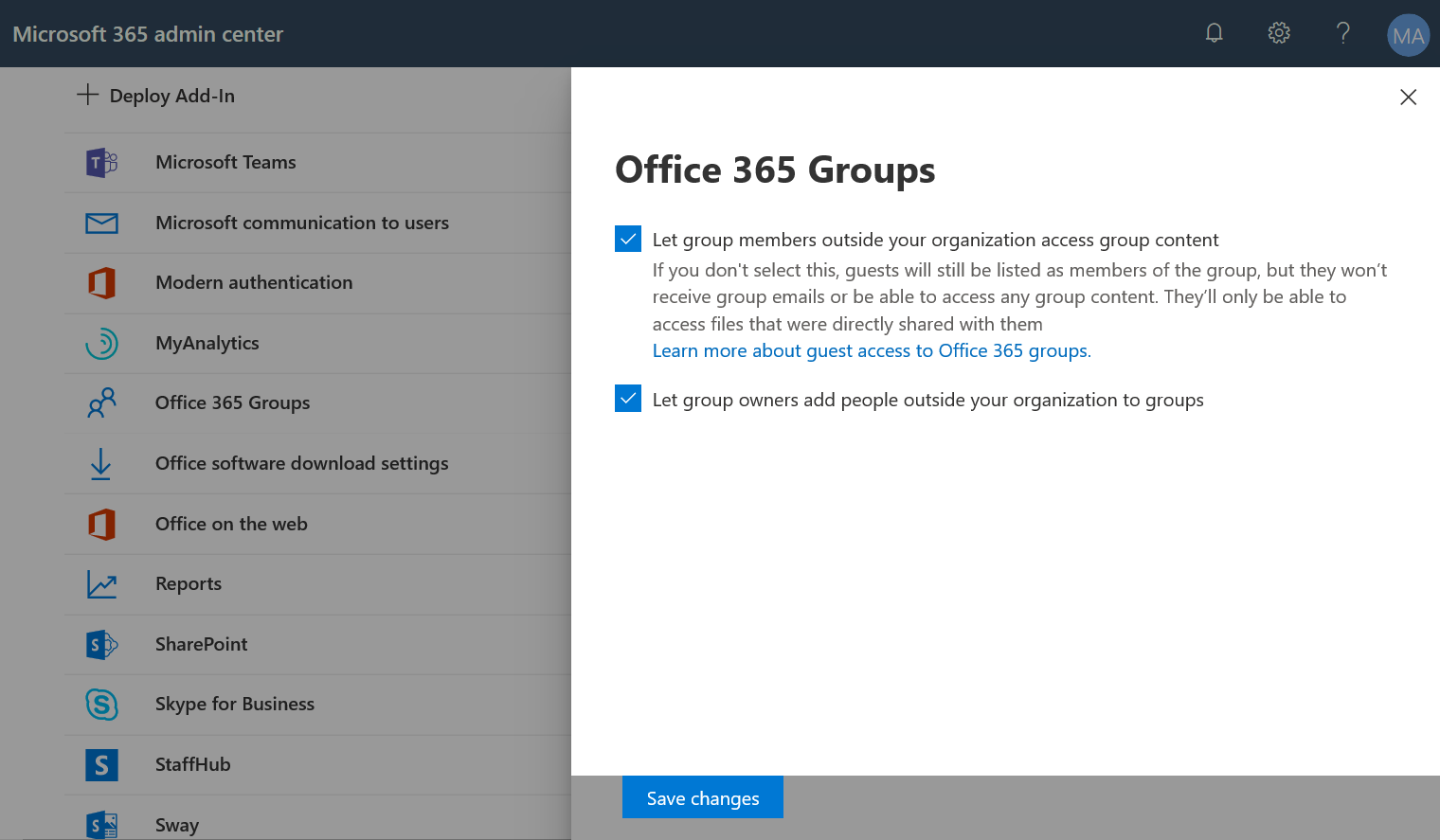
Go to Office 365 Groups settings → Services and Add-ins. Once here, you’ll have two options. Should you allow guests into Groups? Are owners allowed to add those guests?
If you select the first option but do not select the second, you’ll have to rely on your operations or AD team to add all of the guest users to both the directory and the individual Groups. This would require a lot of manual work but serves as a more secure option if you aren’t comfortable with Group owners adding guest users.
Microsoft Teams
Finally, there’s the Microsoft Teams admin center. Once in, go to Org-wide settings → Guest access → Allow guest access in Teams. Once this is turned on, you can further adjust how guests use the service (e.g. Can they delete messages? Use gifs?). Allow a couple of hours for the settings to take effect.
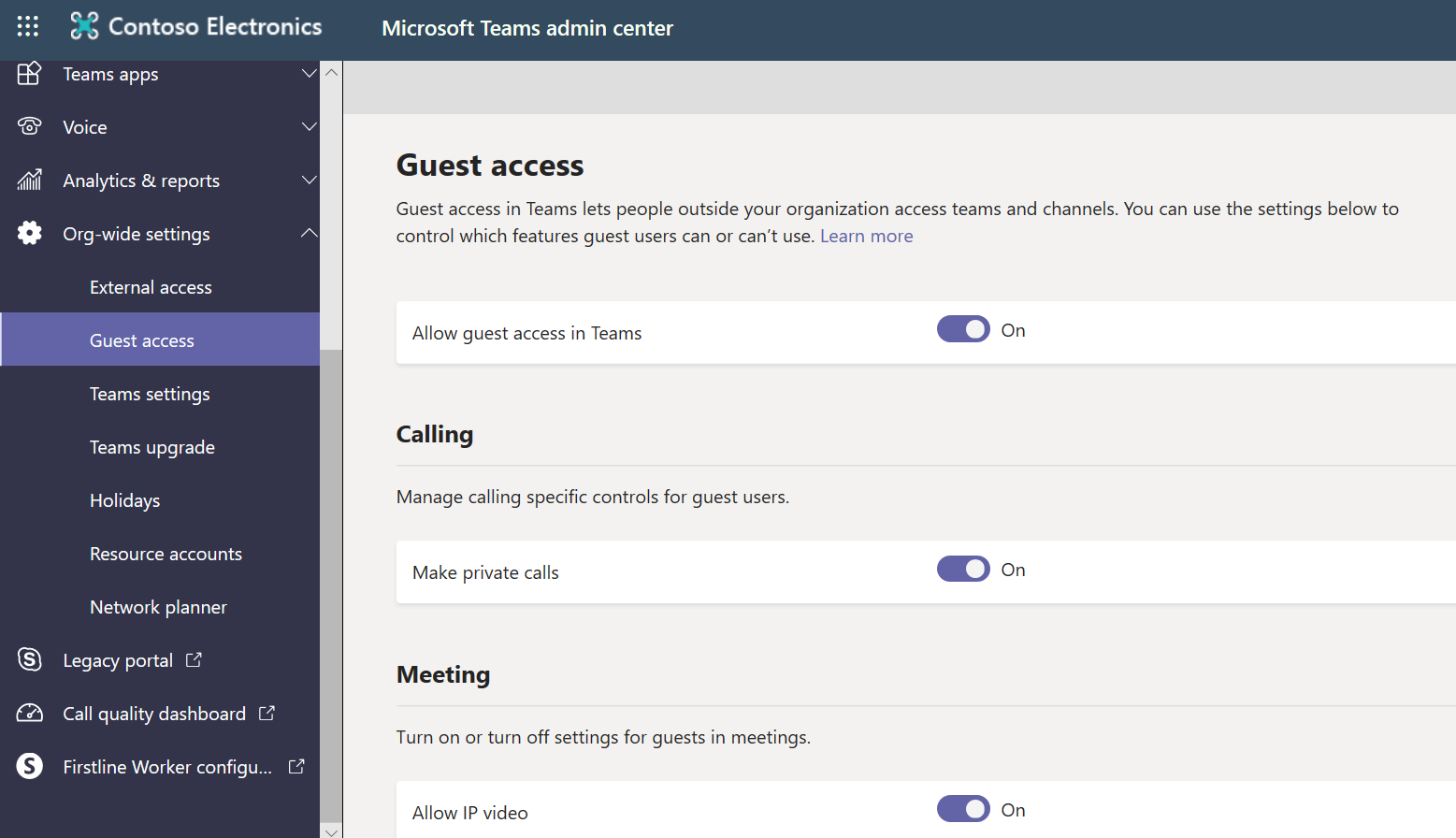
Now that you have guest access turned on in Microsoft Teams, every Team will be able to allow guest users. What kind of guest users and any other controls have already been set in the Azure Active Directory admin center.
If you want more granular guest access control for Teams, you can use PowerShell or other applications to make this happen through the backend.
SharePoint Online and OneDrive for Business
One thing to note here is that SharePoint has been allowing external access way before Azure B2B existed, and this classic model of external sharing still exists in SharePoint. This model has many of the same settings as AAD, but it runs independently from it. You can force more centralization if needed by tying sharing to existing users in the directory.
If you want SharePoint to follow your external sharing settings in Azure B2B:
- Go to the Microsoft 365 admin center → Settings → Services & Add-ins → SharePoint
- Set “Users can share with” to “Existing guests only”
This forces SharePoint to only accept users in the directory and therefore follow all your Azure B2B rules.
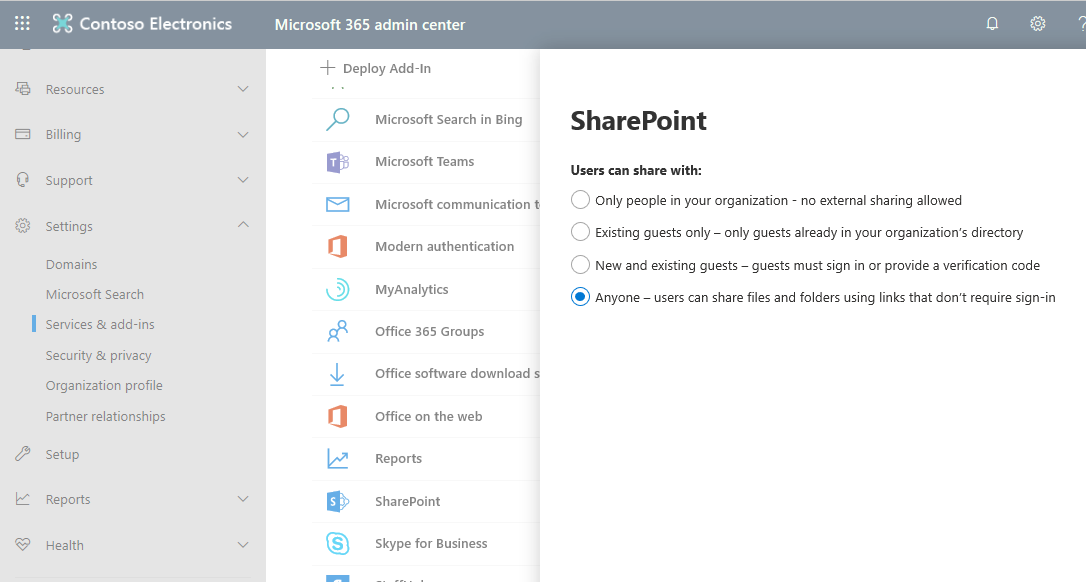
If you want SharePoint to run independently from Azure B2B and have its own external sharing list:
- Go to the Microsoft 365 admin center → Settings → Services & Add-ins → SharePoint
- Set “Users can share with” to “Anyone”
This allows anyone, even anonymous users, to use SharePoint. Settings made by an Office 365 global admin in the Microsoft 365 admin center defines the “most permissive” external sharing settings for SharePoint and OneDrive for Business that will be available for SharePoint admins to leverage. For even more granular control you can also go to each individual site and determine guest access settings.
Are These Management Controls Enough?
A common scenario for external sharing is that you’ll want to collaborate with multiple departments that each have different external sharing requirements and restrictions. While this can be set up through the user interface, the hoops and hurdles for this will likely be an absolute headache for your IT team.
One viable solution is AvePoint’s Cloud Governance system. We’ve integrated external sharing and guest access across our cloud governance application which automates the provisioning and lifecycle management of all Office 365 workspaces. With this, you won’t have to teach your admins how to dive through the complex permission interfaces.
For a step-by-step guide and thorough overview of how to secure external sharing and guest users in Microsoft Teams, check out our webinar. And if you’re interested in backing up the data in your Teams, read our introductory article “How to Back up Microsoft Teams.”

