The Ultimate Guide to Microsoft Teams and Groups Management

More than at any other time, Microsoft 365 has been incredibly helpful for team collaboration, online meetings, file sharing, video conferencing, and much more. That said, it’s been tough for some administrators to monitor and govern collaboration in Microsoft Teams and the Groups that support them since more are being created each day. In this blog post, let’s see how you can effectively govern your Teams without hassle and provide a more secure workspace for users.
To better understand the importance of efficiently managing Teams and Groups, it’s a must to know what this management can do. Two terms that you will likely see in this post are governance and operational governance, so it’s essential that we clearly define what these mean from the outset. Operational governance can be defined as “the process of developing, implementing, and enforcing policies for how IT applications are enabling business success, particularly in guiding user behavior and mitigating risk.” It is having a set of policies with corresponding services ready for your users to use.
When we talk about operational governance, we are also discussing the primary workspace in Microsoft 365: Microsoft 365 Groups. Groups in Office 365 are described by Microsoft as “choosing a set of people that you wish to collaborate with and easily setting up a collection of resources for those people to share. Resources such as a shared Outlook inbox, calendar, or document library for collaborating on files.”
These groups can then be used to manage memberships in many Microsoft tools such as Outlook, OneDrive, OneNote, Yammer, Microsoft Teams, and many more. Microsoft 365 Groups collect the identity of users who need to work together and then create a group identity in Azure Active Directory. With this, you no longer need to create a Team for a specific department in Microsoft Teams, add each person in the department to it as a member, and then repeat the same process for a group in SharePoint. An Office 365 Group and Group identity (which is stored in Azure Active Directory) can be utilized and deployed to different tools and solutions.
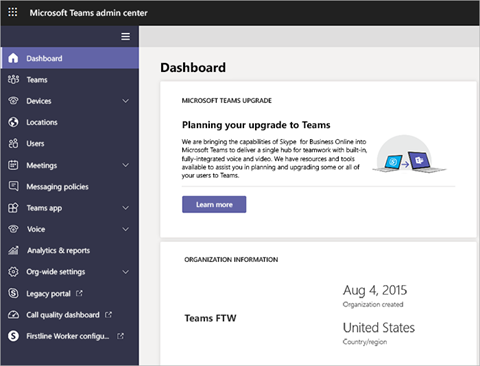
There are also major settings you can configure for your Teams via the Microsoft Teams admin center; however, they are still mostly done by controlling the Groups. Above is the interface of the admin center where most major settings can be tweaked. Notice that most of these are also available at the Team level.
- Guest User Access – This allows people in your organization to work and collaborate with people outside your organization. In the admin center, you can define and manage who you can give access to your organization’s Teams and channels.
- Control Apps, Bots, and Connectors – Microsoft Teams comes with built-in apps such as Planner, Lists, Tasks, Approvals, and more, and you can take control of these apps and connectors. You can manage which apps will be available to users, what they can add, and if the users can customize their own.
- Add classification to your Teams – In the admin center you can label your Teams based on their classification. You can classify your Teams whether they are Internal, External, Confidential, and Highly Confidential. This also strengthens the security and privacy of the Team. Sensitivity labels as such can add additional control over your Teams and make them easier for you to govern and manage. You can read more in this blog post.
Aside from these settings, the Microsoft Teams admin center also allows you to control social features such as GIFs and emojis, manage connections to external storage, and much more that’s available both organization-wide and down to the Team level.
What are the Common Governance Challenges in Office 365?
As we’ve explored, the structure for Teams and Microsoft 365 Groups has the potential to create many governance challenges in Microsoft 365. In every Microsoft Team or Microsoft 365 Group, there are two types of memberships – the owner and the member. The person who created the Group will automatically be the owner. The Group owner has the power to perform and do many things to the created Group such as adding and deleting members, granting minimal permissions to users, providing access to external users, determining whether the Group is private or public, and even deleting the whole Group and everything inside it.
The Group owner alone will need to spend tons of time customizing and managing a created Group and providing specific access to users as needed. Imagine how cumbersome it is for both the Owner and the administrator of the whole organization to make sure all the tasks performed by the Group owner are aligned with organizational policies.
There are multiple ways (more than 20 actually) to create a Group in Office 365, and none of these provide a standard Group structure; they all depend on where they were created. Here are some of the most common ways that Office 365 Groups are being created:
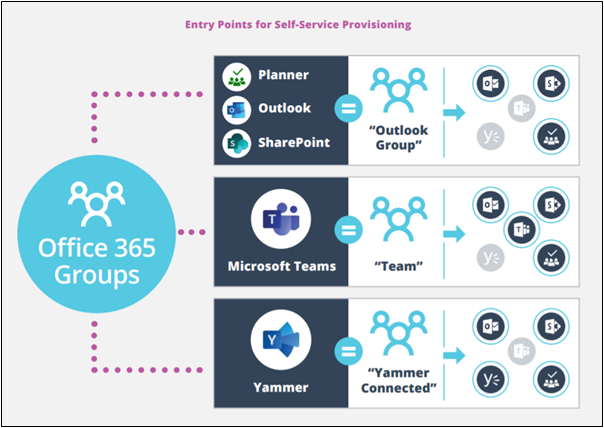
We can see that Groups can be created from different Office 365 solutions. Now, consider that some of your users create new Groups in Teams and others create new Groups in SharePoint and, say, Planner, and that they easily do this without the supervision of the administrator since provisioning has not been restricted for any sets of users.
This might seem like a non-issue upfront, but it will potentially be a large problem, especially when no governance is enforced; these self-provisioning practices will exponentially increase an organization’s consumption of Office 365 and eventually lead to sprawl. No organization wants this to happen, and administrators will have a serious problem governing hundreds and thousands of newly-created Groups or Teams each day.
More Specific Governance Challenges in Office 365
Aside from the scenarios and issues above, let’s dig deeper into why governance is so critical. If you’re an administrator of SharePoint, OneDrive, Microsoft Teams, and other Office 365 solutions and you’re not quite sure if governance is what your organization needs or just don’t know how it can make a big difference, the following issues might help you determine how governance can rectify some of your day-to-day administering struggles.
Provisioning
- Group Sprawl – As mentioned above, users can independently create new Teams and Groups, which can lead to sprawl without moderated control from admins. This can also create an abundance of unnecessary items, making it hard for users to keep track of and find the content they are looking for.
- Consistent Naming Convention – Also brought up above are multiple non-standardized ways to create Groups and Teams, resulting in ununiform Group names which make them harder to manage. It’s possible to accomplish this with PowerShell via prefixes or suffixes for the group name, but these policies are tenant-wide. The issue can still be felt by multi-division organizations since different departments prefer and require different naming conventions.
- Public or Private – Another provisioning issue is determining whether the Group is a public or private one. Making a clear distinction between the two could mitigate potential data security incidents. Public Groups and Teams are open for all and can be seen by everyone in your tenant, which makes the confidential information and documents inside at risk. Making the Group private could prevent this from happening.
- External Access – Another issue to consider is sharing access to external users. This should not be decided by the Group owner alone as it should abide by the organization’s policies depending on the nature of the content and processes involved.
 Management
Management
Via PowerShell it’s possible to control who can provision Groups, but managing them after they are created is a different discussion. Here are some management issues you must look out for:
- Recertifications – Part of managing Groups in Office 365 is auditing then recertifying permissions in place. It’s ensuring that the right users have the right authority and permissions in the Group. This might be a little tricky when managing tons of Groups from different departments of users. It’s also important to understand the Shadow Users (non-member/owner users) who have access to content in a Group or Team via direct sharing.
- Correcting Non-Compliant Actions – During the audit of Teams and Groups, there are instances where the wrong permissions have been granted to a user. This will pose a huge problem for the admins as they need to constantly communicate with end users to confirm that the correct permissions are in place and will also need to make changes and corrections to out-of-policy permissions or settings.
- Reporting – There are times when certain teams in the organization such as the security team will ask the admins for reports for internal auditing purposes. Reports like activity audits will show if users are compliant with policies and will help the team ensure all content is secured and safe. It could take tons of hours to manually generate these reports from thousands of Groups when you can instead automate report generation.
End of Lifecycle
- Content Expiration Settings – There will come a time when certain Groups and Teams will no longer be needed and are ready to be retired. However, what will happen to the important files and data inside? You should have a plan for when to keep items and when to delete them.
- Expiration Oversight and Reporting – When managing your data lifecycle, having an overview of what data is slated to be deleted or archived is critical. It may be important to review the items through reports before deleting or archiving them or even allowing the users methods to ensure that they no longer need the content in an active form in some scenarios.
- Preventing Improper or Accidental Deletion By Owner – We learned earlier that the owner of a Group can actually delete the entire Group. Once this happens the Group is held in a soft delete state for 30 days but is then permanently deleted itself. What if that happens at your organization? What are your plans for retrieving all the deleted important data inside of it?

If any of these issues are happening in your organization (or if there aren’t any proper plans for if these potential problems do occur), then you might need to think of a better Office 365 governance strategy.
Right-Sizing Your Level of Governance
There should be a balance between providing your users with unrestricted access to Office 365 and ensuring that organizational policies are being met and followed. It’s vital to have the correct level of governance based on various criteria, and from that you can enforce the right governance for your organization. Here are some signs and symptoms of an under-governed system:
- Users struggle to find information or items due to similar naming conventions
- IT tickets, emails to stakeholders, and questions all slow production.
- Business processes vary from department to department.
- Inconsistent training.
- Shadow IT emerges.
- Ad-hoc and informal processes.
- The IT Team is constantly putting out fires.
- Slow adoption
Take a look at the diagram below showing examples of ungoverned, light, and fully governed Office 365 tenants.
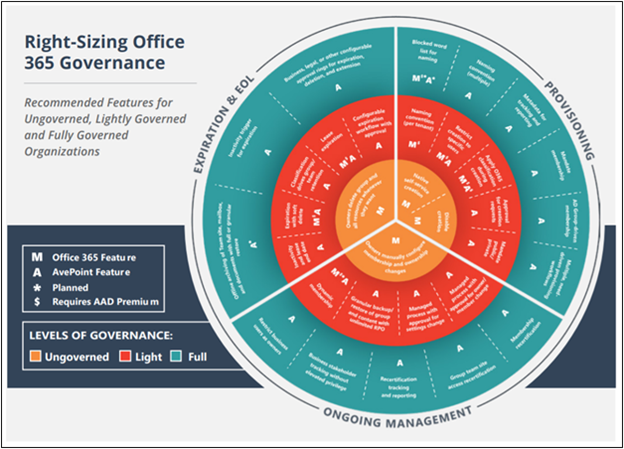
Though Office 365 includes a lot of policies and native governance features, we often hear from our customers that these are too blanketed for the entire organization and that it’s very difficult to tailor them to meet the needs of their users. This is where AvePoint’s Cloud Governance solution comes into play.
Cloud Governance offers an automated and fully managed provisioning process for your Office 365 tenant, empowering you to choose which settings and options to give to your users through requests that can be approved in a configurable approval process. With the My Hub app for Microsoft Teams, it’s also incredibly easy for users to access their content and workspaces as well as the services they need all from one secure location.
This governance solution also allows you to ensure policy enforcement without the need for repetitive processes. It comes with over 20 service types that you can use to automate everything such as Microsoft Teams compliance and security, SharePoint governance, Microsoft 365 management, and Microsoft 365 retention and policies. It can handle your day-to-day tasks without consuming more time from admins.
Additionally, AvePoint’s Cloud Governance can automate generating a “renewal task” to re-certify user access, permissions, and roles. To address the end of lifecycle issues above, admins can apply lifecycle policies to the Sites, Groups, and Teams to ensure the important stuff is kept and the rest is disposed of appropriately. De-provisioning is even available for idle or unneeded workspaces based on user inactivity or timeframe.
Hungry for even more Microsoft Teams tips? Subscribe to the blog!
Adrian is currently a member of AvePoint's project management team. In his previous role as a Content Marketing specialist at AvePoint, Adrian covered the latest trends and topics on what’s new in technology, SaaS Management & Governance, SaaS Backup and Data Management.



