3 Must-Use Microsoft Teams Security Features

It’s been almost a year since most organizations shifted their workforce to a work-from-home setup. While so many of us were gathering in meeting rooms not too long ago, most of the meetings today are being done online or via some sort of hybrid method.
However, this change may put the security of organizations at risk and lead to confidential information being leaked. It’s now harder for the administrators to monitor every move done by users to ensure that no company information will be shared externally. In this blog post, we’ll go over a few handy features that’ll help keep your Microsoft Teams tenant is secure.
Security in Microsoft Teams
To start, it’s important to understand that as a consumer of Microsoft 365 products, you own and control your data; thus, the responsibility to keep it secured is in your hands. Microsoft Teams is built on a Microsoft 365 enterprise-grade cloud that leverages advanced security and compliance capabilities.

Microsoft uses Team-wide and organization-wide two-factor authentication, single sign-on through Active Directory, and the encryption of data in transit and at rest for Teams. All files being shared in Teams will be stored in SharePoint with SharePoint encryption, so if you want to check and search for an item shared in Teams you can find all files residing right there. Aside from these security features, you can dive even deeper into security settings in Microsoft 365 (changes to these settings will apply to Microsoft Teams as well). Let’s dive into three features in particular:
1. Safe Attachments
This is a feature designed to enhance user security by detecting and checking malicious attachments in Microsoft Teams. Global administrators can create policies for these suspected malicious attachments to prevent them from being spread, clicked, or opened by any user. This safety feature is also available in SharePoint and OneDrive. How does this work?
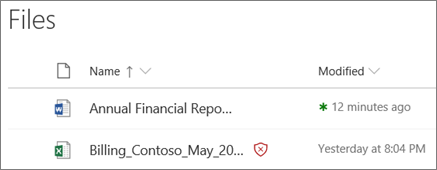
When the Safe Attachment feature is enabled and a suspected malicious file is identified, the file will then be locked using direct integration with file stores as seen in the screenshot above showing a malicious file. The blocked file will still be listed in the library, but it cannot be opened, moved, or even shared. You can download the file afterward or delete it permanently.
2. Sensitivity Labels for Compliance
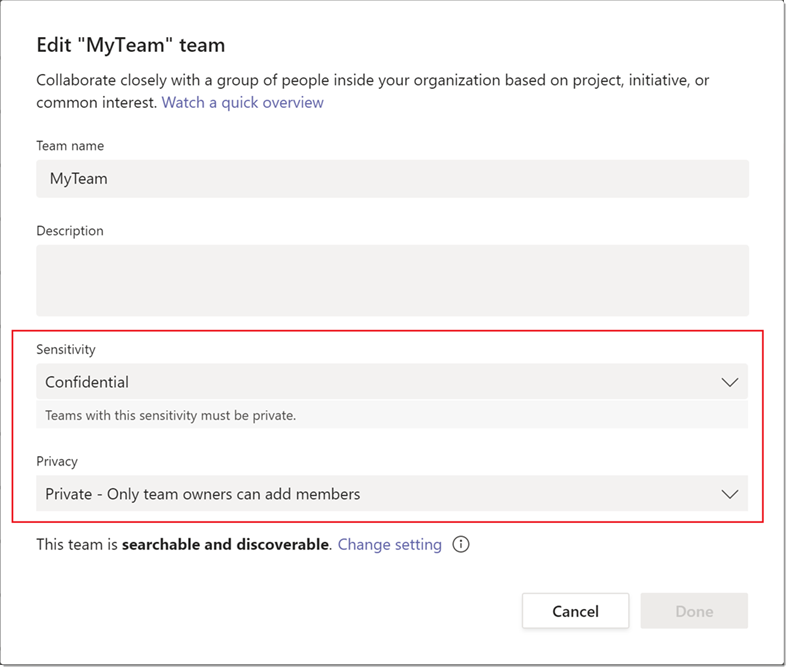
Sensitivity labels allow Microsoft Teams administrators to regulate access to sensitive content created during collaboration in Teams. Once these labels have been configured in the Microsoft Compliance Center with their corresponding policies, these can then be applied to Teams in the organization. Another benefit of sensitivity labels is that they provide powerful infrastructure support to secure sensitive data and ensure compliance with your internal policies or regulations in the organization.
3. Audit Logs
Aside from the settings above that you can configure to make sure that your Teams are secured, you can also check audit logs to investigate activities within your Microsoft 365 environment. Here are some of the activities written in the logs for your checking:
- Teams created
- Teams deleted
- Added channels
- Settings that have been changed
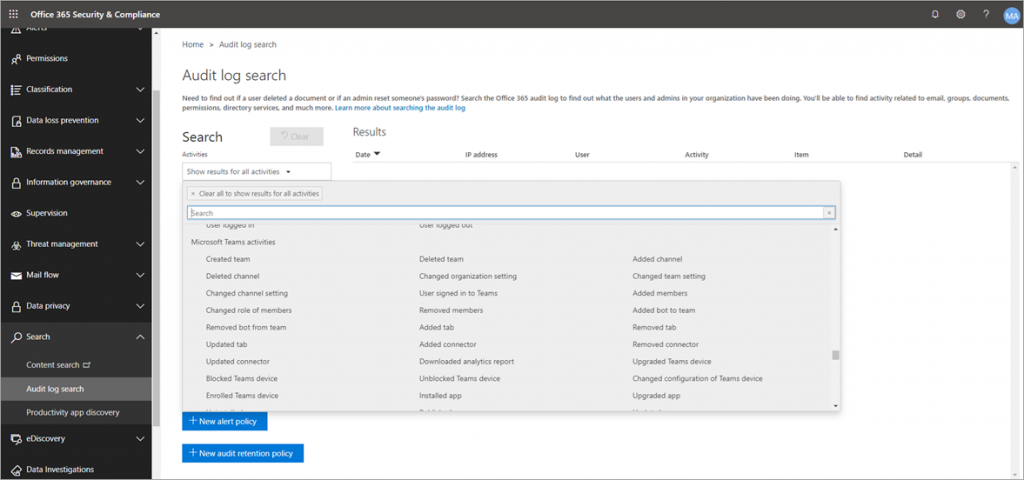
To have these logs available, make sure to turn on auditing in the Security and Compliance Center.
With the sudden shift in the workforce towards at-home work environments, it’s especially important to make sure that all of your organization’s data is secured and compliant. If the right precautions are taken, however, security should not be an issue for Microsoft Teams administrators, especially if the aforementioned features are utilized.
For more Microsoft Teams management tips, do not forget to subscribe to our blog!
Adrian is currently a member of AvePoint's project management team. In his previous role as a Content Marketing specialist at AvePoint, Adrian covered the latest trends and topics on what’s new in technology, SaaS Management & Governance, SaaS Backup and Data Management.



