Read our other Microsoft Ignite recaps below:
- Satya Nadella’s Keynote: Business Trends & The Metaverse
- What You Need to Know About Privacy Management for Microsoft 365
- How to Protect Sensitive Microsoft 365 Data With Data Loss Prevention
- 4 New Microsoft 365 Hybrid Work Features on the Horizon
More than 250 million users rely on Microsoft Teams to provide a robust platform for collaboration with their workplace colleagues.
But achieving the same connection with people outside of an organization requires administrators to configure their own Teams policies and provisioning that, if applied too broadly, could expose sensitive data to guests or create Teams sprawl in order to keep outside audiences siloed.
Those concerns could soon be a thing of the past.
The creation of Microsoft Teams Connect (aka “shared channels”) is intended to help organizations enable seamless, secure collaboration outside their digital walls.
What are Shared Channels in Microsoft Teams?
In some ways, shared channels are similar to private channels in that shared channels also provide an exclusive space only for approved members.
However, shared channels allow external users to more easily participate (as well as internal users who now can be invited without first having to join the top-level Team that hosts the channel).
“Businesses are operating in vibrant environments where the connection with partners, vendors, and customers is a critical component of business success,” Arun Das, a principal program manager for Microsoft Teams, said last week. “They tell us that when the external collaboration is optimized, it can improve visibility, accountability, and trust.”
Here’s what we learned during the Ignite session on shared channels — currently in private preview and set for public preview early next year — and what the announcement means for Microsoft Teams users.
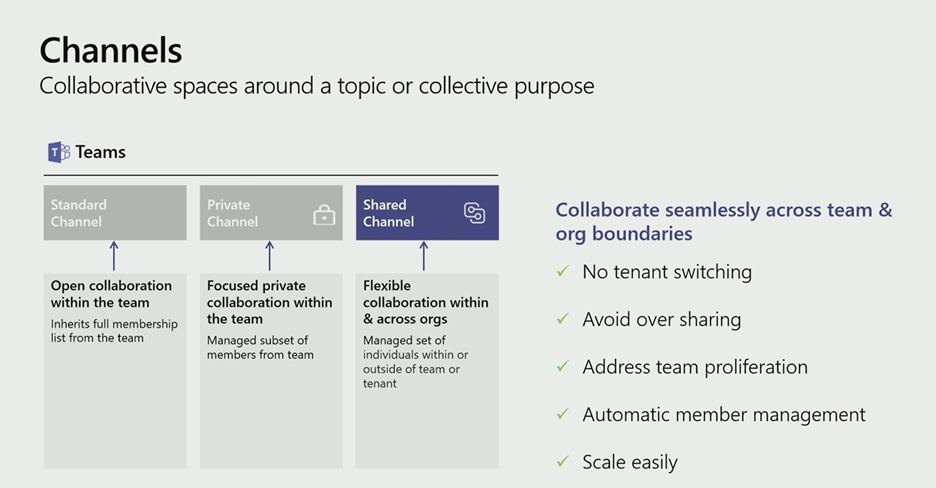
1. Shared Channels Are Designed to Be Secure
When it arrives, the shared channel function won’t automatically be turned “on,” but it will offer granular control to best suit an organization’s needs.
For cross-tenant shared channels, administrators on both sides must configure cross-tenant access policy tenant posting, and the shared channel will have to set up inbound access specifying who from the external tenant is allowed to participate. (Similarly, you’ll need to set up outbound access specifying who from your own tenant can participate in the external shared channel.)
GET OUR NEWSLETTER: Subscribe here for weekly content from AvePoint
A shared channel will not inherit a Team’s membership, but it will adopt the existing settings. So, when a shared channel is shared with another tenant, the host’s standard policies will apply. Similarly, when a shared channel is shared with another Team, the sensitivity label of the host Team will apply.
2. Inviting a User to Shared Channels in Teams Is Easy
Administrators may choose to invite an individual or an entire Team to collaborate in a shared channel. These people can either be from your own organization or from an external party with Azure Active Directory.
Once external users are added to a shared channel, they can view and access the channel right from their Teams account — there’s no need to switch tenants or sign in with a different account. This is great for continuity and efficiency.
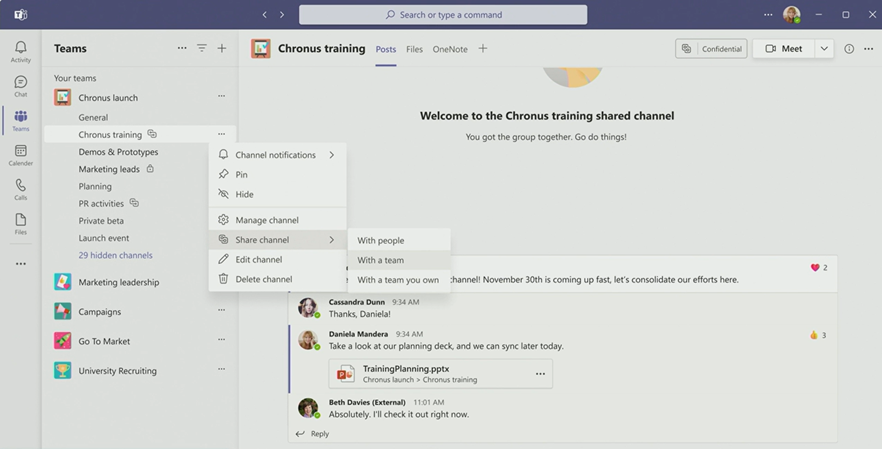
No matter which side you’re on, identifying a shared channel is simple: An icon will appear next to the name of that channel, giving participants on all sides a clear indication that a cross-tenant audience is collaborating in this space. To that end, outside users will also have “(External)” appear next to their name.
3. External Users Can Only Access the Shared Channel (And Nothing Else)
Under the current design of Microsoft Teams, any user invited to a channel also gains access to all other non-private channels within that Team by default. That, of course, isn’t ideal.
Thankfully, this will no longer have to be the case. With shared channels, an invited user (whether internal or external) can only access and communicate within that specific channel.
Not only does this deliver a secure experience, but it also drives efficiency by cutting out the sprawl and complexity that can occur when trying to safeguard data shared externally by creating new Teams.
To ensure data stays within its intended boundaries, a shared channel can’t ever be converted to a public or private channel.
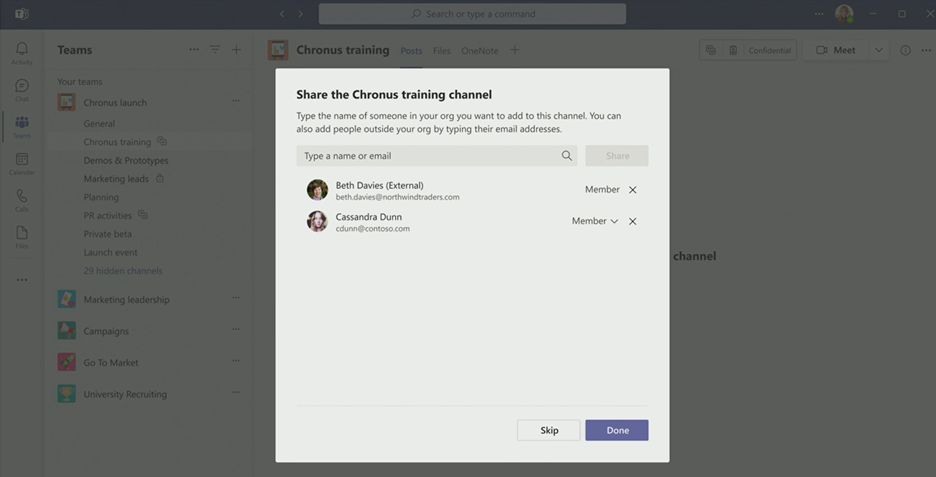
4. Sharing and Meeting Capabilities Are Limited for External Users
When it launches, shared channels will support the full suite of app capabilities, tabs, connectors, boards, messages, extensions, and line of business apps associated with the channel. Approved users from outside the host tenant will be able to leverage these functions.
But external users can’t do everything. Sharing, for example, is restricted; these users can only share files from the shared channel with other existing channel members. This is to ensure sensitive data doesn’t accidentally leak out.
And while shared channels are meant to foster deeper collaboration, external users can only join (and not prompt) a “Meet Now” request or an already scheduled meeting.
5. Membership Management Is Highly Automated
The shared channels function is designed to take some of the legwork out of managing membership. A shared channel owner can promote any direct member of the channel from their own organization to be an owner. But if a channel was to become ownerless, the system will automatically promote one from within.
READ MORE: Private Channels in Microsoft Teams: Fact vs. Fiction
Channel owners may choose to share the channel with other Teams, and any subsequent membership changes that those Team owners make will also take effect in the shared channel.
In other words, as members join and leave the Team, they’ll gain or lose access to the shared channel without anyone having to manually manage channel membership).
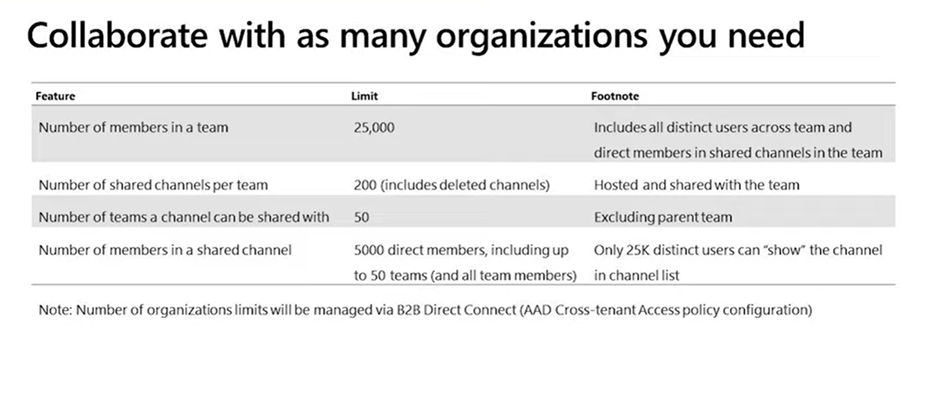
6. They Can Accommodate Big Groups and Many External Tenants
The shared channels function is envisioned to be a “boundary-less” experience, so the announcement that a Team can have up to 200 shared channels (in addition to the 200 standard and 30 private channels) is no surprise.
Attendance and reach can also go far: A shared channel can handle 5,000 direct members, and it may be shared with 50 Teams. If membership exceeds 25,000, only the first 25,000 members will be able to add the channel to their channel list.
And when it comes to external organizations, the sky’s the limit. A shared channel can be shared with as many organizations that can be specified in the Azure AD cross-tenant access policy, according to the Ignite announcement.

