What is Microsoft 365 Audit Logging?

To combat cybersecurity threats, one of the prime features of any security strategy should be to have visibility over the entire environment. By being aware of your vulnerabilities, you can smartly map out countermeasures to cover your security gaps.
As an IT administrator, how do you get this visibility over your Microsoft 365 environment? What are the things you need to be looking out for and where could you see those?
In this blog post, let’s explore audit logging and its role in your Microsoft 365 (M365) security.
What is audit logging?
Microsoft collects your system activity logs to ensure you have a record of everything that’s happening in your Microsoft 365 environment. Every update, access, event, or system change is recorded in these logs, and this is where the original audit record is irreversible to ensure the security and authenticity of said logs.
These audit records can then be kept either for 90 days or indefinitely depending on your Microsoft 365 license.
According to Microsoft, audit logging has two main benefits:
- Security: Helps identify internal policy violations or misuse of systems or information, and helps serve as an asset for legal battles. When tied to a monitoring tool, audit logs can also help detect security violations or breaches before they happen.
- Compliance: Keeping audit logs can be used as documentary proof of your compliance with the regulations your organization is under.
Audit Logging in Office 365
Microsoft personnel have their own audit logs to record, retain, and protect to keep the Microsoft cloud and systems secure.
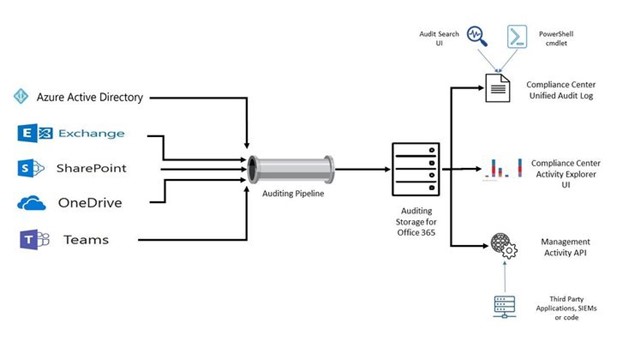
As your organization’s IT administrator, what you’re responsible for is keeping your own Office 365 security and compliance. You can utilize the audit logs of your Office 365 environment to track user and administrative activity in the following Microsoft services:
- Azure AD
- Dynamics 365
- Exchange Online
- Microsoft 365 Defender
- Power Platform
- SharePoint
- Stream
- OneDrive
- Teams
- Yammer
And because many of Microsoft’s platforms are integrated, other activities are also included in the audit log, such as:
How to Access Audit Logs in Office 365
So, how do you access and manage your audit logs to control security in SharePoint or keep Microsoft Teams secure?
See below for the three main access points where you can get a record of your Microsoft services audit logs:
1. Microsoft Purview Compliance Center:
Microsoft Purview was previously called the Unified Audit Log and is the main location where all your audit records can be found. If you want to utilize audit logs for your SharePoint site security, Microsoft Teams security, or even for Office 365 Groups security, Microsoft Purview is the place to be.
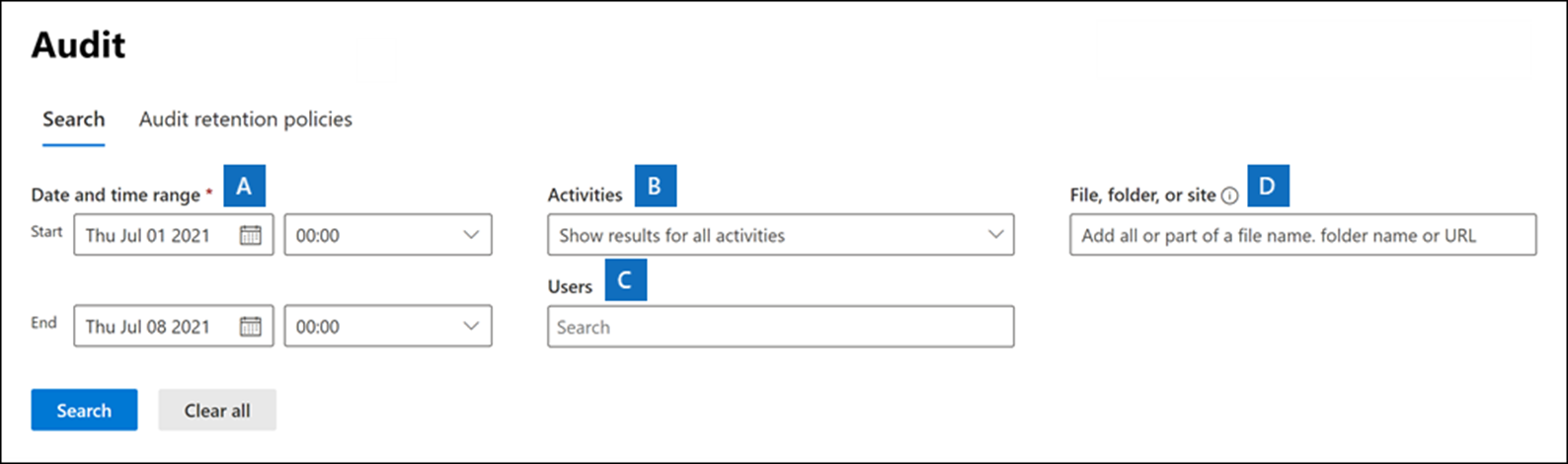
An audit search tool is available in the purview compliance portal, allowing you to zoom in on specific users or groups or for specific periods.
2. Office 365 Management API:
Fewer content types are made available if you leverage the Office 365 management API, but they still help by retaining your audit records for more than the standard 90-day period.
From your exported file using the O365 management API, you can then import the data into your SIEM solution for more seamless activity tracking and monitoring.

3. Microsoft 365 Activity Explorer:
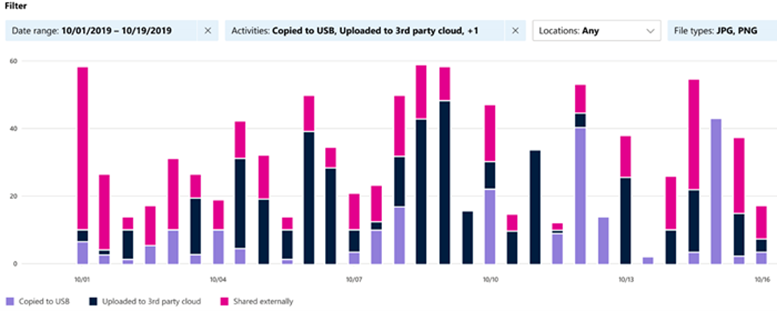
Activity Explorer serves as a tool to better track how effective your policies are by monitoring and keeping audits of your tagged and labeled content.
For example, if you tag a file as highly confidential, activities (printed, read, modified, etc.) around that content are captured and recorded in an audit track that can be accessed in the Activity Explorer.
Strengthen Office 365 Security with Backup and Insights
Microsoft’s audit logging capability is a helpful tool to establish the foundation of your security strategy.
However, visibility without monitoring, data analysis, and backup tools cannot help you to be proactive in detecting attacks before they happen and with your recovery after it does.
What solutions should you integrate it with?
You can tie audit logs to Microsoft’s native monitoring tools, but you must be prepared for some limitations.
Mailbox auditing for Office 365 email security, for example, puts a limitation on audit searches if you don’t have the proper license and unless you turn the capability on for each of your users. That sounds tedious and confusing!
To reap the benefits of Microsoft 365 audit logs without the burdensome and time-consuming processes, you can instead integrate third-party tools that help strengthen your security in Office 365, such as:
- Policies and Insights (PI) is built on top of Microsoft Information Protection and leverages Microsoft Data Loss Prevention policies and tags to help alert your team of any oversharing practices, allowing you to secure sensitive content before it can be improperly overshared.
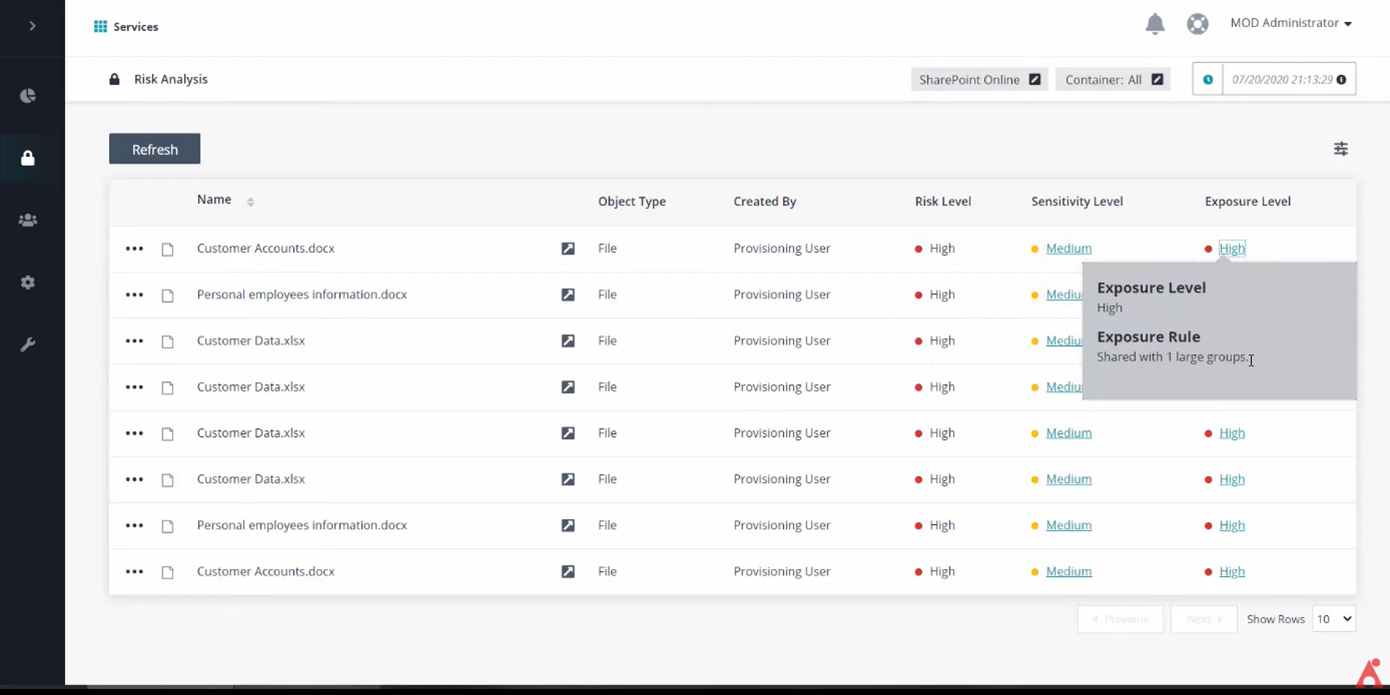
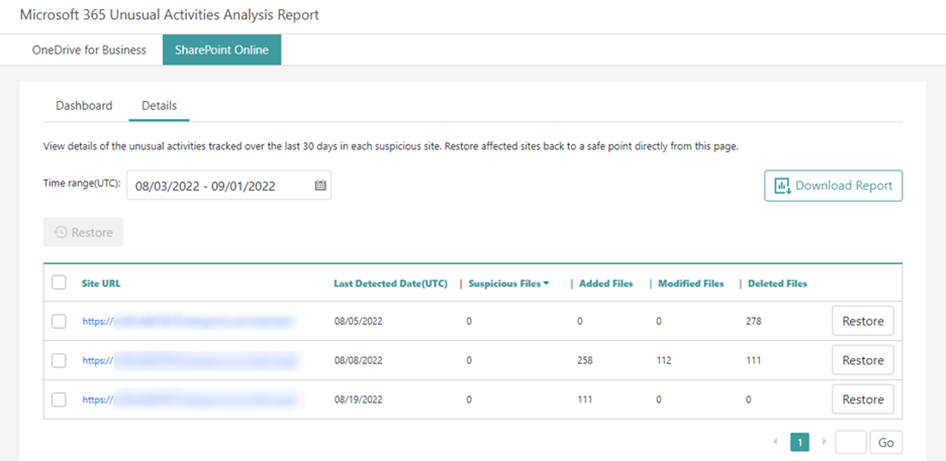
- Cloud Backup can help retain your audit logs indefinitely (for compliance or standard security practices), detect unusual activities, as well as help you quickly bounce back during a downtime or attack scenario with backup and recovery capabilities.
Need more expert insights into Microsoft 365 security best practices? Check out AvePoint’s Data Protection solution and learn all the things you need to know to keep your Microsoft environment and systems secure.
Subscribe to our blog for weekly Microsoft 365 security insights.
Sherian Batallones is a Content Marketing Specialist at AvePoint, covering AvePoint and Microsoft solutions, including SaaS management, governance, backup, and data management. She believes organizations can scale their cloud management, collaboration, and security by finding the right digital transformation technology and partner.



