When to Upgrade From E3 to E5 for Stronger Microsoft 365 Data Protection


Concerned about potential data leaks? Watch our on-demand webinar “Preventing Data Leaks in Microsoft Teams (and Other Collaboration Systems)” for expert advice.
Read the other posts in our Securing Collaboration series below:
- How to Get ISO 27001-Ready
- Oversharing Challenges in Microsoft 365
- How to Find Sensitive Content in Office 365
- Sensitive Info Identifiers in Office 365
- 5 Risk Management Challenges in Office 365
- Top 5 Microsoft 365 Security and Compliance Center Features and Tricks
- How to Build a Strong Permissions Management Strategy
- Office 365 Governance in an Always Online World
Microsoft 365 comes with a plethora of great tools for ensuring data security and compliance for organizations large and small. Beyond basic access permissions, many if not all of these security features are available via the Microsoft 365 Security and Compliance admin center. Data retention, legal holds, DLP, and access controls are the main tools available to organizations to secure their Microsoft 365 platforms, but each of these has features that make them much more powerful than the offerings of most other collaboration platforms.
That having been said, different licenses enable different sets of features for each of the main tools of Microsoft 365.
Beyond comparing the features of each tool from the licensing guides and service descriptions, it can be hard to understand the limitations of an E3 vs. an E5 when it comes to security and compliance, let alone truly understand when you really may need to upgrade to E5 license for your organization.

Let’s take a look at what you get with an E3 vs an E5
When we look at the offerings of Microsoft 365, there are a plethora of security features. DLP reports allow you to keep track of which files have certain kinds of sensitive information. Data retention options allow you to automatically apply retention labels and to manage the lifecycle and retention of the content you store in Microsoft 365. The Records Management Center allows for even more granular control of the disposition of information across Microsoft 365. For security and access controls, sensitivity labels provide a great deal of control over who can take which kinds of actions on documents and workspaces.
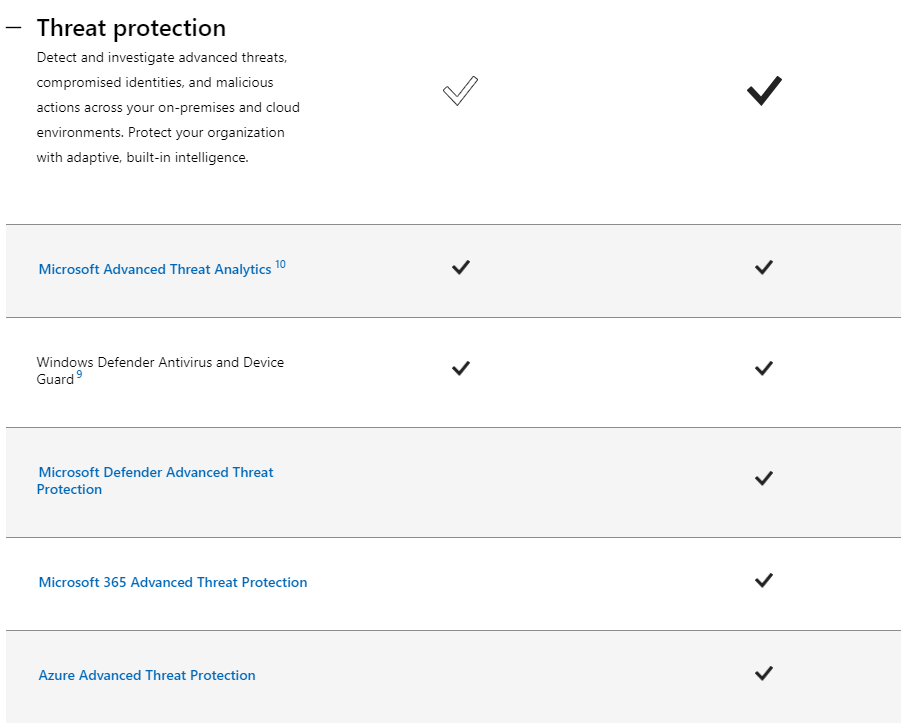
When you upgrade to an E5 license, it becomes possible to automatically apply retention and sensitivity labels based on policies that define criteria. An E5 also enables Advanced Threat Protection to help protect the entire tenant from phishing and malware schemes. In addition, E5 licenses also enable labeling and security protections that extend some of the features of sensitivity labels outside the Microsoft 365 tenant via App Security and features of Azure Information Protection (AIP P2 may be required to fully take advantage of certain features on other platforms).
There are more disposition and action options available in the Records Management options in addition to Advanced eDiscovery that are only accessible with an E5. Lastly, additional tools that help control who can collaborate with whom in the tenant are brought to the table (Information Barriers, Supervision Policies) when an upgrade to an E5 is made.
So, when should I look at an E5 vs. E3 license for my organization?
Organizations with strict security requirements that have large numbers of workers dealing with secure or governed information are the perfect candidate for an E5 license. The E5 features in the security and compliance center help Security and IT teams scale the security and data retention controls of Microsoft 365 with automated tools that are enabled via dynamic controls. In addition, the robust capabilities of Advanced threat Protection and advanced eDiscovery bring a lot of value to any Microsoft 365 tenant.
Each of these capabilities typically requires label definitions and policies to be applied to Microsoft 365, and they work across most of the common applications that house documents and other files across the platform.
Unsure when you should upgrade from E3 to E5? This post is might helpful: Click To TweetThis can still be a lot to keep track of and maintain, especially if you’re having to coordinate workloads across IT/security teams.
With so many security features and tenant-wide controls, it’s vital that security and IT teams maintain an understanding of how their own policies and features are affecting the collaboration of their users. In addition, it’s important that the teams understand exactly how the policies and tools they have set up affect each other and what part each plays when it comes to data governance in Microsoft 365.
Even with an E5 license, it can be difficult to keep track of who has access to which documents and where sensitive information exists across the platform. With all the available policies and features, maintaining an understanding of where and how security policies have been applied can be tricky, especially as your environment expands over time and the collaboration needs of your teams grow.

A proactive approach to managing Microsoft 365 exposure to secure content can save your teams tons of time
AvePoint’s Policies and Insights (or PI) solution makes it easy to take a more proactive approach to securing sensitive information, and can automatically prioritize your content based on which documents with sensitive information have the most exposure. PI can also surface which users in your environment may be creating risk by accessing sensitive documents.
PI makes it easy to enable external sharing for the workspaces and users that need it while also offering handy restrictions. Need to figure out who has access to what? No problem. Need to understand your sharing links and which workspaces can be accessed by external users? That’s a cinch!
Policies and Insights makes understanding your organizational security a breeze and brings proactive controls that apply corrective actions across Microsoft 365 in ways that scale with your organization as it grows. You can learn more (and request a demo) here.
For more on data protection in Microsoft 365 be sure to subscribe to our blog.

Hunter Willis has been in web development, SEO and Social Media marketing for over a decade, and entered the SharePoint space in 2016. Throughout his career he has developed internal collaboration sites, provided technical and strategic advice, and managed solutions for small to large organizations. In addition, Hunter has served as a strategy consultant for many companies and non-profits in the Richmond area.


