4 External Sharing Scenarios to Consider in Microsoft 365

This is an excerpt from our Microsoft 365 External Sharing ebook. See the others below:
- 3 Policy Considerations for Microsoft 365 Guest Access
- A Quick Look at Configuring Guest Access in Azure AD
There are many controls to explore when configuring Microsoft 365 to support secure access from outsiders. And each organization has its own requirements for outsider access. This section will outline some of the major decision points across four general-purpose scenarios for how an organization can set this up with standard licensing.
For the tailored control scenario below, we have chosen a simple configuration with four different workspace templates.
Workspace Templates
Sensitive Internal
The Sensitive Internal workspace would likely be used by departments within the organization that routinely handle sensitive information, such as the finance department.
Sensitive External
The Sensitive External workspace would likely be used in limited scenarios and heavily monitored. For example, the legal department might have required some external collaboration on sensitive files with external counsel–a limited number of regular external collaborators who have been signed to an NDA.
Non-Sensitive External
The Non-Sensitive External workspace could be used for departments that do not regularly handle sensitive information (such as marketing) but have vendors like public relations agencies that serve as external collaborators. Rather than limit guests, this template restricts sensitive information.
Non-Sensitive Internal
The Non-Sensitive Internal workspace could serve as the de-facto or most used workspace for everyday work and collaboration within the organization.

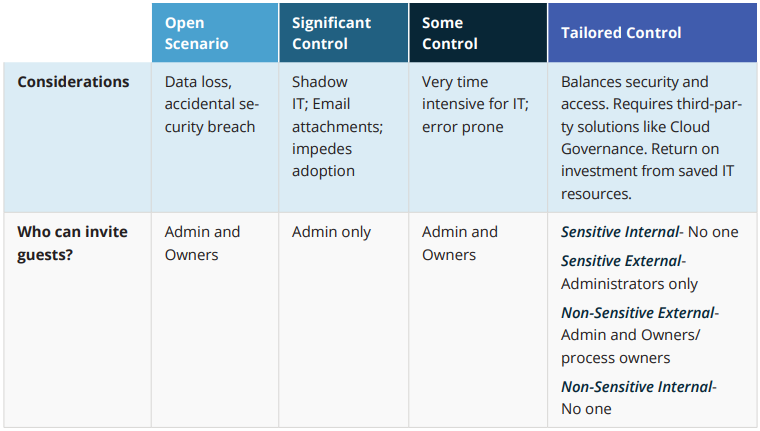
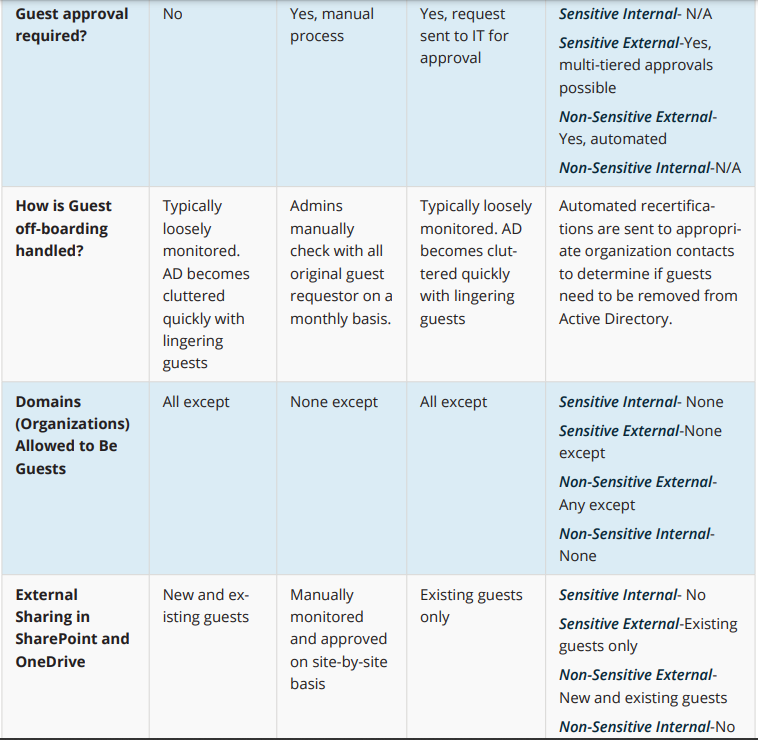
Four Scenarios for Sharing with Outsiders
1. Open Scenario
For organizations that don’t deal with sensitive or regulated content and speed of collaboration is key.
2. Significant Control
For organizations dealing with very sensitive content on a regular basis. External sharing only happens with guests and very few guests are admitted and only by admins.
3. Some Control
For organizations trying to balance the need for external sharing and information security.
4. Tailored Control
For organizations where a “one size fits all” tenant-wide approach isn’t ideal. Different types of workspace templates can be created with trailed controls and provisioned automatically based on information provided by the user. For example:
- Sensitive Internal
- Sensitive External
- Non-Sensitive External
- Non-Sensitive Internal
Note: Third-party solutions are also being deployed to prevent sensitive data from being uploaded to non-sensitive workspaces.
For more insights into external sharing across departments and more, be sure to download the full ebook here!
Keep up with the latest Microsoft 365 external sharing developments by subscribing to our blog.
As the former Content Marketing Specialist for AvePoint, Brent led the strategy and direction of all AvePoint's blog properties.



