How to Set Up Multi-Factor Authentication (MFA) in Microsoft 365

As cybersecurity threats continue to be prevalent, IT leaders have been forced to level up security measures to better protect their organizations from various risks.
It’s becoming even more relevant as business leaders perceive cybersecurity-related risks as business risks, according to a Gartner survey.
While there are multiple layers of protection to deploy, it’s best to start with your frontline security—identity management—as it’s not only one of the top security risks Gartner has seen in the past year, but it helps provide a good defense against possible attacks.
With that, let’s go over how you can better protect your Microsoft environment by enabling one of the most popular identity security methods: Multi-Factor Authentication.
What is Multi-Factor Authentication (MFA)?
To sign in to a device or online service, we commonly use usernames and passwords as a way to authenticate our identity and have access to our accounts.
But passwords have now become vulnerable and easily compromised. To help alleviate identity-related risks, an additional layer of security in the form of an additional verification method is now being used by many services today. This is typically called two-step verification or Multi-Factor Authentication (MFA).
Basically, enabling Multi-Factor Authentication in your organization means you require your users to provide more than one way to verify their identity before they’re given appropriate access to your services or environment.

Types of MFA
What makes multi-factor authentication a strong security measure is the fact that your authentication factors must consist of a combination of two factors that are not easily duplicated.
The three most common factors are:
- Something you know – Passwords or memorized PINs
- Something you have – A smartphone or a secure USB key
- Something you are – A fingerprint or facial recognition
A combination of two factors makes it harder for attackers to hack an account because if a password or a pin is compromised, a smartphone code or a fingerprint (which are harder to steal) would still be needed to complete the sign-in.
Multi-Factor Authentication in Microsoft 365
Microsoft 365 supports MFA for user accounts using:
- A verification code sent as a text message to the user’s phone
- A phone call
- The Microsoft Authenticator smartphone app
There are three ways to enable MFA in Microsoft 365:
1. Security Defaults
With security defaults, preconfigured security settings managed by Microsoft are provided to your organization to help protect your organization from identity-related attacks. Part of these settings includes automatically enabling MFA for all your admin and user accounts.
To turn on security defaults:
- Log in to the Microsoft 365 Admin Center with security administrator, Conditional Access administrator, or Global admin credentials.
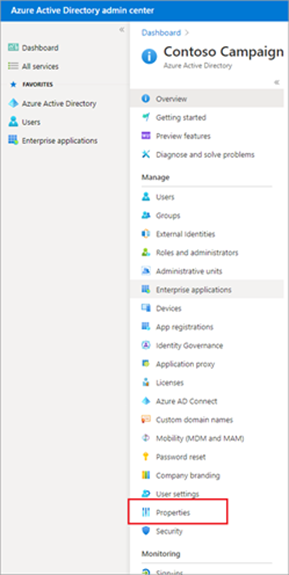
- Go to the Azure Active Directory portal under Admin centers.
- Once on the Azure AD page, choose Manage from the left menu of the dashboard and select Properties. On that page, you’ll see Manage Security defaults on the bottom part of the page.
- If you see Yes selected in the Enable security defaults (found on the right side of the pane), no further action is required. If not, select Yes to enable security defaults.
2. Conditional Access
With Conditional Access policies, granular or specific policies can be created for organizations with more complex security requirements. These policies determine whether or not access will be granted to users depending on the specified conditions under which sign-ins are evaluated.
This makes it easier for admins as you can assign MFA requirements based on group membership rather than configuring MFA for individual user accounts.
To enable MFA with Conditional Access policies, we first need to create a conditional access policy and add that to your specified groups:
- With Global administrator credentials, sign in to the Azure Portal and choose Azure Active Directory.
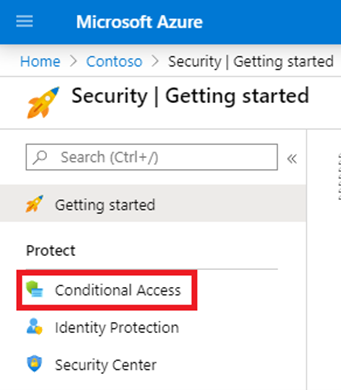
- Next, on the left side of the menu, choose Security > Conditional Access > +New policy. Create a name for your policy.
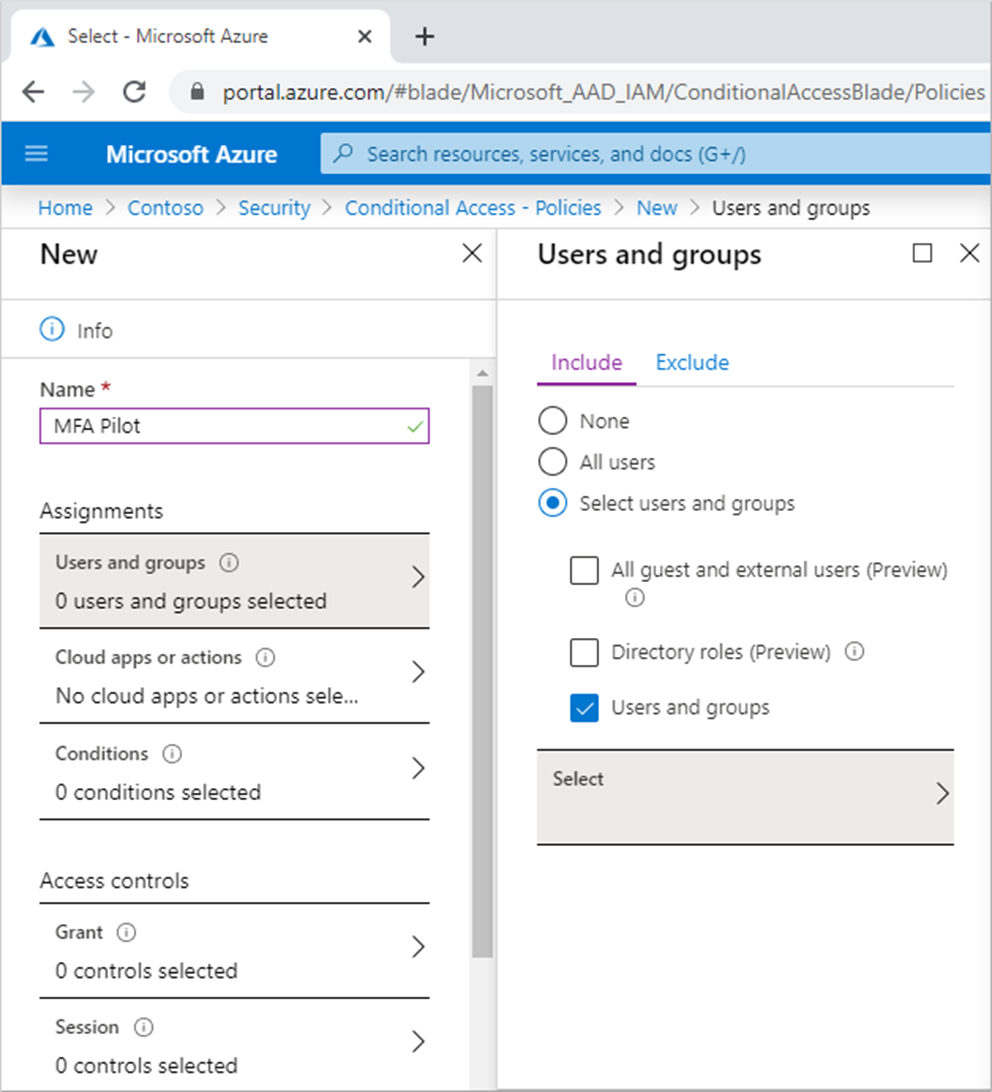
- Go to Assignments > Users and groups, then choose the Select users and groups radio button.
- Tick the box for Users and groups and click Select to see available Azure AD users and groups.
- Choose your Azure AD group and select Done to apply your new policy.
Next, we need to configure the conditions for multi-factor authentication when a user signs into the Azure portal to define which cloud apps and actions will trigger your new policy:
- In Cloud apps or actions, you can choose to apply your policy to All apps or Select apps (if you want to exclude certain apps from the policy).
In this case, since we’re configuring MFA for Azure sign-ins, choose Select apps, select Microsoft Azure Management > Select > Done.
- Under Access controls, choose Grant > select Grant access radio button.
- Check the box for Require multi-factor authentication > Select.
- Toggle Enable policy to On then select Create to apply the Conditional Access policy.
3. Legacy Per-User MFA
While Microsoft strongly recommends only using security defaults or conditional access policies, you can still enable per-user MFA.
Do note, though, that this would be more inconvenient both for you as an admin (as you’ll have to configure every single user’s settings) and for your users (as they have to perform MFA every time they sign in unless it’s from a trusted IP address or the feature remember MFA on trusted devices is on).
There are three states to know if a user is registered for Azure AD Multi-Factor Authentication or not:
- Disabled: All users start in this state. This means they are not yet registered for MFA.
- Enabled: Users are enrolled in MFA, but the user must register to the MFA methods for the MFA to be enabled. If they don’t register, legacy authentication wherein passwords are still used remains an option for sign-ins.
- Enforced: Users are enrolled in MFA and have already completed the registration. MFA is required when they sign in.
To change the status for a user:
- Log in to the Azure Portal with Global administrator credentials.
- In the Azure Active Directory, go to Users > All Users.
- Click Multi-Factor Authentication.
- Find the user you want to enable MFA for (you can change the view from the top to Users) and check the box beside the name(s).
- On the right-side pane, under Quick Steps, choose Enable or Disable, then confirm your selection in the pop-up window that opens.
Admins may move the users between states such as moving from Enabled to Enforced or from Enforced to Disabled. However, changing a user’s state directly to Enforced is not encouraged unless the user has already registered.
Important Reminders
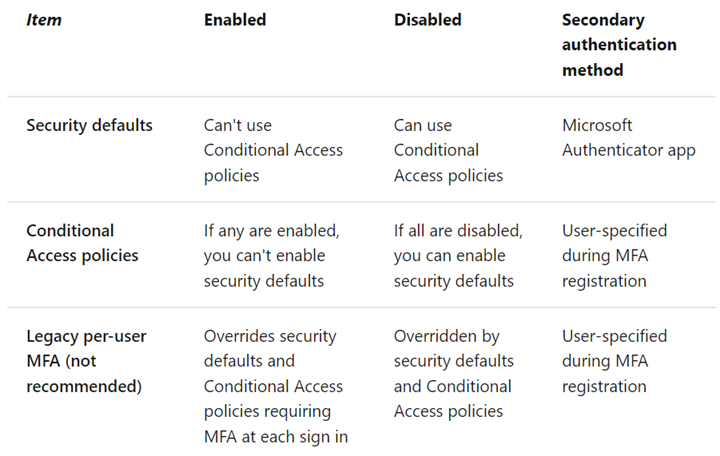
Before we wrap up, it’s important to note that sticking to one method is better than using the methods together. Here’s what happens if you do:
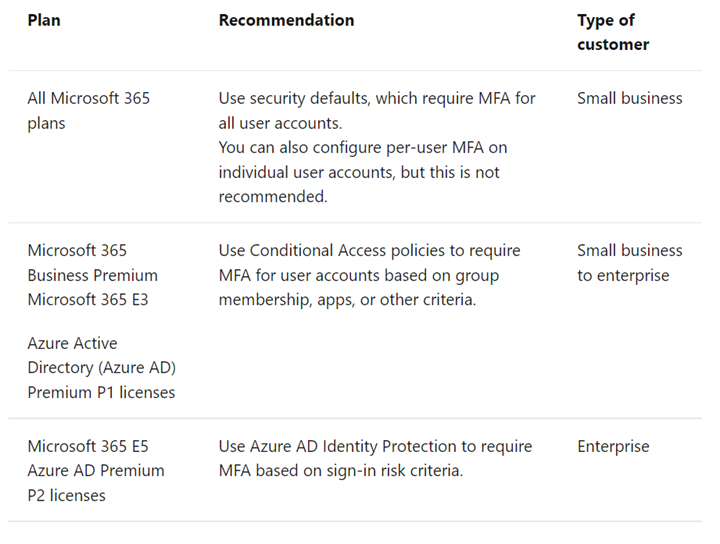
Lastly, here are the recommended methods depending on your Microsoft 365 plans:
For more on data protection be sure to subscribe to our blog.
Sherian Batallones is a Content Marketing Specialist at AvePoint, covering AvePoint and Microsoft solutions, including SaaS management, governance, backup, and data management. She believes organizations can scale their cloud management, collaboration, and security by finding the right digital transformation technology and partner.



