With the rise in ransomware and data breaches, security has never been more top of mind for business leaders and IT admins alike. Microsoft offers a plethora of security features to protect and secure your Microsoft 365 tenant, but it may be challenging to determine which features will deliver the security your organization needs.
In this post, we’ll discuss how to build a comprehensive security strategy for your team’s day-to-day use of M365 following AvePoint’s tried and true method: layering identity, data, and workspace security features to protect your team’s overall collaboration.
Looking for a walkthrough of setting up some of Microsoft’s top security features – including multi-factor authentication, information barriers, and sensitivity labels – in the admin center? Check out our free webinar: “Microsoft 365 Access Security: Which Security Tool When?“
Establish Identity with Conditional Access
Why Identity?
In our cloud-based workplace, identity has never been more important. It’s not as simple as “this device in this location is approved for access” because your employees are no longer centralized to one office or one employer-provided device. Instead, we need to verify that the person who’s accessing our information is who they say they are.
Microsoft’s Solution
Microsoft has a variety of tools that can help you both establish identity and control security attributes, but our recommendation is to leverage their conditional access feature. Conditional access functions on a two-phased approach to verify identity and approve access. First, it collects information about the person (their device, IP address, etc), and then it enforces any policies you have in place. This could mean if it detects a new device, it may enforce multi-factor authentication (MFA), request the user sign in again, or limit what the device has access to.
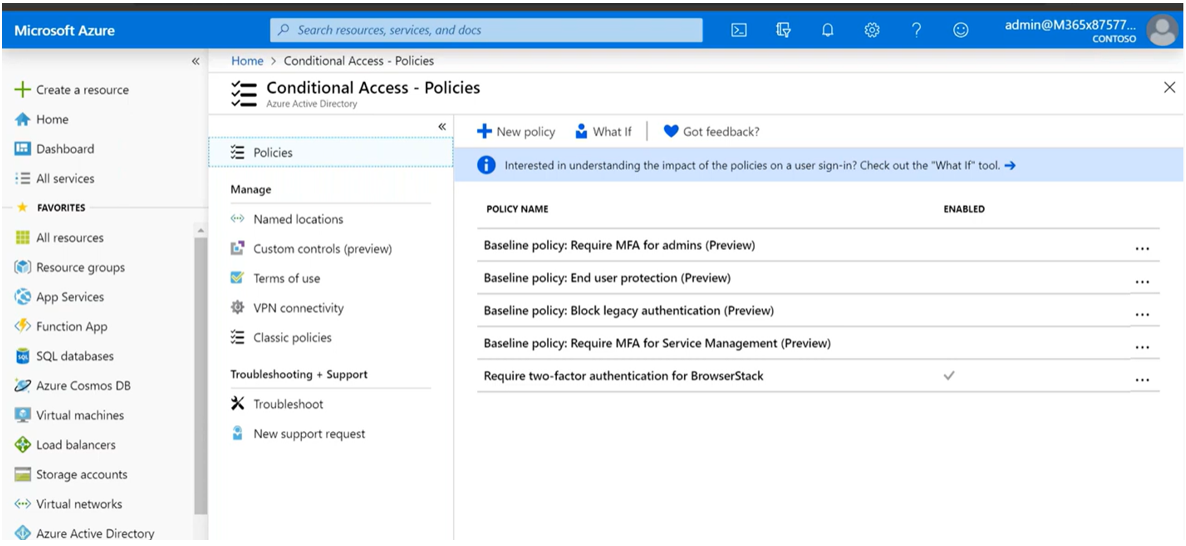
Admins control the conditions and the enforcements based on their specific needs and the information they need to protect. For example, you can prevent any mobile device from accessing your tenant if you’re worried about the vulnerability of devices in public networks.
With 20% of data breaches caused by compromised credentials, tools like conditional access are a great security foundation to protect your Microsoft 365 tenant. But what about when restrictions aren’t so rigid, such as certain external users who may need access from a mobile device? That’s where AvePoint comes in.
AvePoint Cloud Governance can help you right-size your policies for the “sometimes” scenarios. With the solution, you can create and enforce conditional policies that help secure your environment without overcontrolling it.
Classify Your Data with Sensitive Information Types
Why Data?
It’s no secret that we’re living in a rapidly expanding datasphere, where information is usually accessed on laptops instead of inside libraries. Today, businesses are digitally managing more than ten times the amount of data since 2016, including sensitive information. With the introduction of global privacy and security regulations like the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), it’s never been more important to ensure you know where your sensitive information is and who has access to it.
Microsoft’s Solution
If you didn’t have information about your users, conditional access wouldn’t work; if you don’t have information about your data, your policies won’t be as effective in protecting it. Microsoft’s sensitive information types can help.
Sensitive information types automatically classify your data by detecting sensitive information. They identify and label sensitive items like financial data or personally identifiable information (PPI) based on hundreds of different information types from different countries and industries. You can even create information types tailored to you, such as code words within documents or contract language specific to your industry or company.
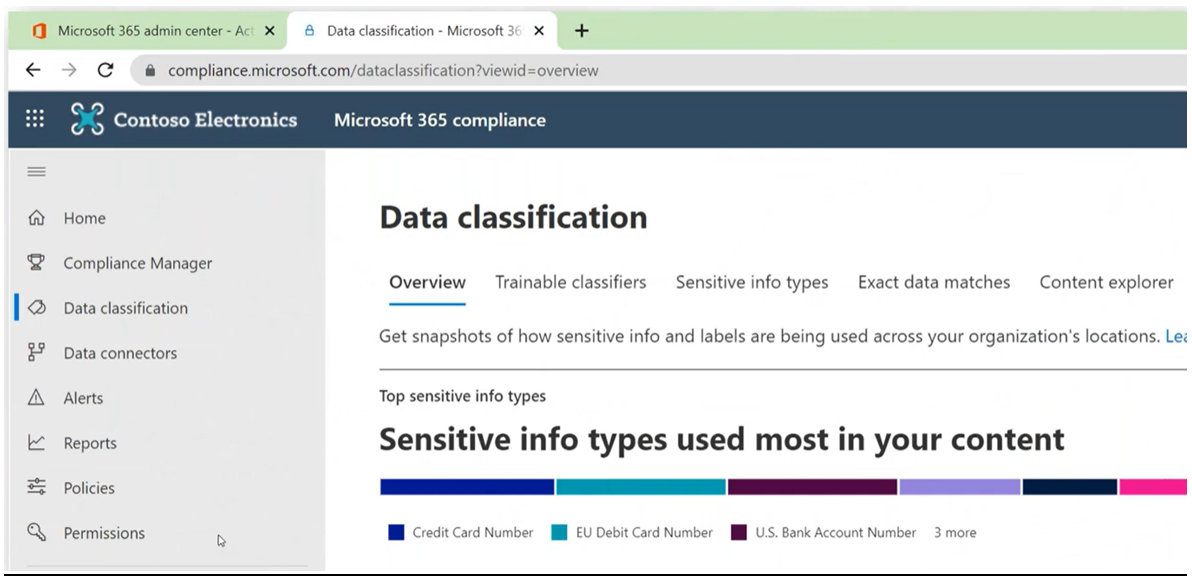
This has a lot of benefits. It improves data discovery and compliance with global regulations, but most of all, it enables the creation of policies right-sized to your environment. After all, you need context to tailor policies for certain audiences and purposes.
Ready to take this one step further? AvePoint Insights builds on Microsoft’s great controls and provides even more information. Through the solution, you have access to centralizing reporting to see where sensitive information is and who has access to what. For example, if you want to see which external users are accessing what, Insights can shine a light on the information in question, its sensitivity, and when a user last accessed it. If anything looks off, you can immediately revoke access from within the solution.
Label Your Workspaces with Sensitivity Labels
Why Workspace?
You can’t rely on every piece of sensitive information to be properly auto-classified. You also can’t chase every document to confirm if each is properly labeled by their sensitivity level. If you secure your environment at the workspace level (aka site, Group, Team), you don’t need to worry about each document individually. This helps you establish baseline internal and external rules around sharing and access, particularly when paired with conditional access, and saves your IT admins time and a huge headache.
Microsoft’s Solution
Microsoft’s sensitivity labels allow you to classify documents and Groups based on their sensitivity. The labels not only classify each piece of content, but also enforce the protection settings you create around each classification.
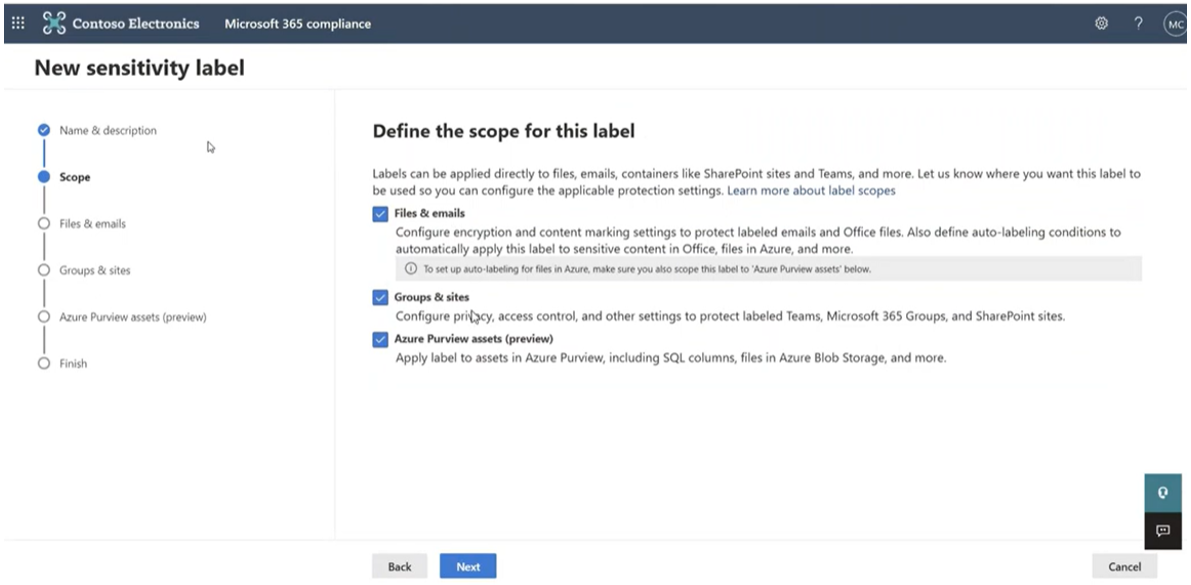
This protects sensitive content as well as any collaboration within the Group that may be sensitive – such as chats or posts that may include information about candidates for a potential merger or unreleased earnings. These labels and their automatic and persistent policies prevent inappropriate information flow and limit accidental oversharing, securing your environment.
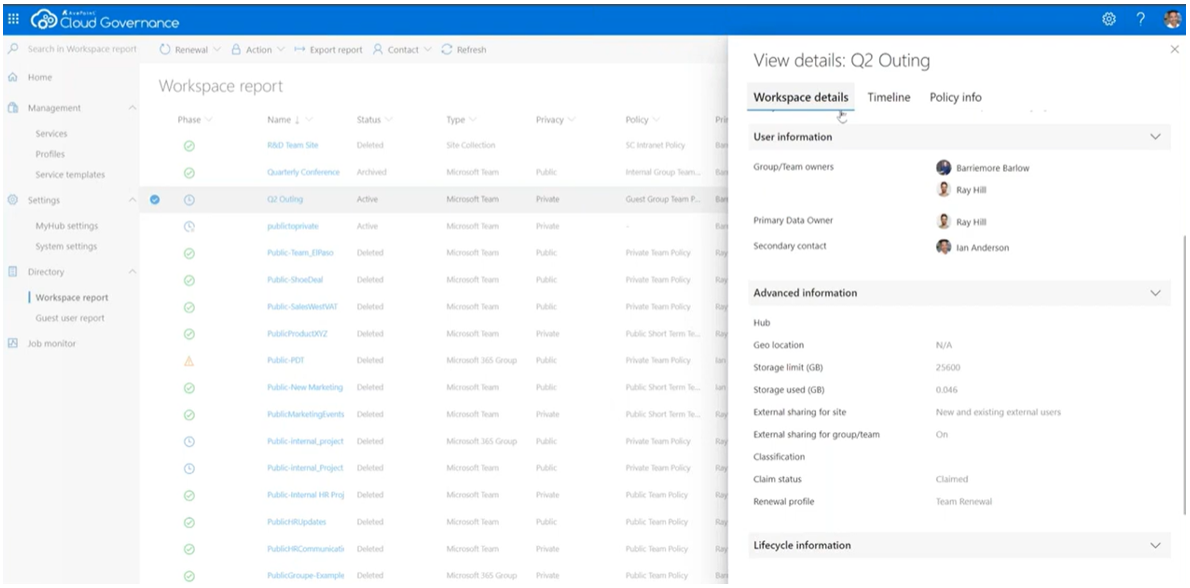
But how do you ensure each new workspace has the proper label or that all workspaces are still current? That’s where AvePoint can help. AvePoint Cloud Governance can automate conditions during provisioning that would require the Owner to specify the purpose of the Group, ensuring the proper label is applied. Then, you can use Cloud Governance to keep an inventory of your workspaces and periodically check in and confirm the Group still has an owner and that the proper policies are in place. This not only helps protect your M365 tenant but also prevents sprawl.
The Bottom Line
Microsoft offers robust security capabilities – but because they’re so comprehensive, it can be challenging to determine which strategy to pursue. With AvePoint’s method – governed workspaces, secured data, and managed identities – you can build a great security strategy to protect your team’s day-to-day Microsoft 365 collaboration.
Get a walkthrough on how to enable these features and more in our webinar “Microsoft 365 Access Security: Which Security Tool When?“

