The 3 Layers of Microsoft 365 Collaboration Security

With such a wide range of security features in the Microsoft 365 ecosystem, it can be tough knowing which tool to use when. Each security feature is designed to be used in specific use cases where it can be the most effective. In one of our recent webinars titled “Which Security Tool When? A Guide to Microsoft Collaboration Security,” John Peluso and John Hodges discussed these security tools and how to effectively deploy them at your company.
It takes multiple layers of protection to achieve a proper security posture in any organization. As discussed in the session, we’ll be focusing on the following three layers in the Microsoft 365 security environment since they’re the most relevant to a user’s day-to-day work: securing identity, securing data, and securing workspaces. Let’s look at how each layer works on its own and as part of a greater security structure.

Layer 1: Securing Identity
When we say identity in Microsoft 365, it always leads to Azure Active Directory (Azure AD) as it is the foundation of Office 365 security capabilities. For admins, this is where your users and groups reside and where you configure them according to business needs. There are many features in Active Directory that improve and contribute to the security posture of your organization; take conditional access as an example.
Conditional Access is used to control permission to a certain entry point. There are various types of conditional access features that you can use to ensure that content is only accessible by the appropriate users.
- Multi-factor authentication – This is a policy by which where users need to authenticate their identity through a different means, in this case via the Microsoft Authenticator App. This was launched specifically for the purpose of passwordless authentication and can be easily set up by admins for an additional layer of identity security.
- Device Management – This conditional access policy can also be configured from the SharePoint admin center. With users taking advantage of bring-your-own-device (BYOD) initiatives, admins can utilize this policy to set up how those unmanaged devices can access organizational resources. You can allow full access, limited access, or block access.
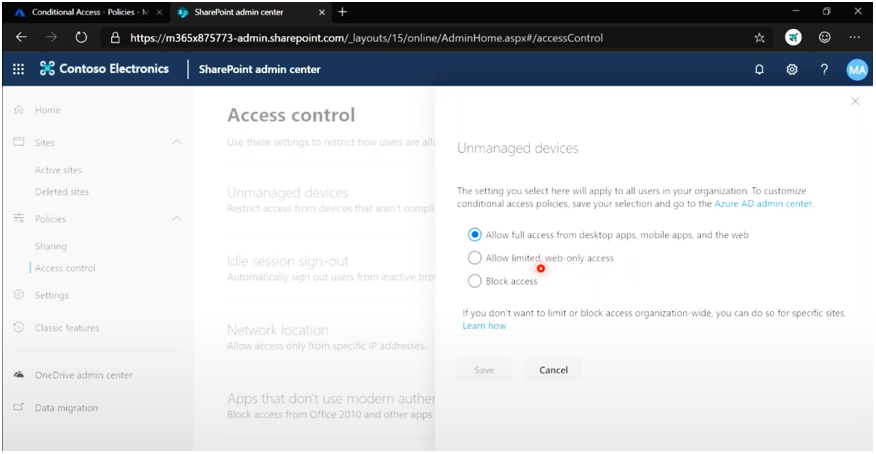
- Terms of use – This conditional access policy allows internal and external users to access your organization’s resources by first requiring them to agree to specified terms and conditions of use.
- External Identities – This policy allows users outside of the organization to access your services and applications such as SharePoint, Microsoft Teams, and more while keeping their own identity. In this case, you don’t need to keep and manage their credentials. This approach results in the centralized identity management of guests and centralized reporting of membership.
Having these policies can add up to secure identities in your organization. Moreover, it helps keep the organization compliant with global policies such as FINRA and ITAR regulations.
Though the above conditional access policies can help with identity security, it could be cumbersome to manage them layer after layer after layer. Moreover, as there are multiple global regulations, it can be tough to know what to use when to stay compliant. With Policies, you can have an easy glance at your in-place filter policies including those configured from Azure AD. You can also update and configure policies for them to work together to ensure secure identity and access in your organization.
Layer 2: Securing Data
Another key to a strong security posture in your organization is to understand how data works and why it should be protected. From Microsoft’s perspective, there are over 300 predefined sensitive information types to help you identify critical data without the need to be an expert on different global data security regulations.
These data classifications can be automatically activated and used. Microsoft does the heavy lifting when it comes to data classification, but higher license types get a better way of handling these identifiers.
“Microsoft’s information protection solutions help you protect sensitive data throughout the lifecycle – inside and outside of the organization.”
How do Microsoft native tools handle data security?
- Data-loss prevention (DLP) – This approach has been around for quite a while now. It detects sensitive information in your organization and blocks it right away in line with the regulations in place.
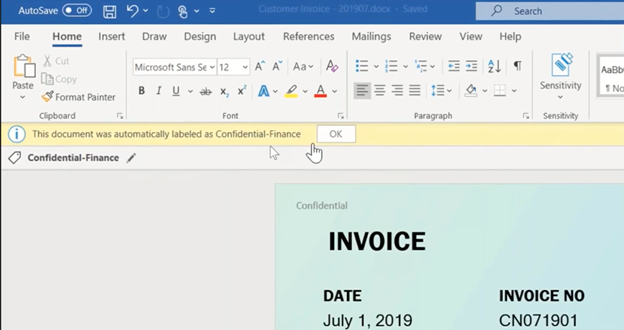
- Sensitivity labels – also known as document labeling, this is a security feature from Microsoft where metadata is written into a document and goes with it as it moves. This can be utilized to apply protection or data governance. They can be auto-applied to documents and emails, or you can allow your users to apply them manually. Take a look at the example in Word below:
While these features are great in ensuring data security, John reminded viewers not to over-rely on them as there is a bigger picture outside of document-level protection. In Office 365, permissions and sharing settings can be confusing and loose, such as the free and open sharing system and the decentralization at the site collection level in SharePoint. It always boils down to right-sizing control based on risk.
How can you move forward?
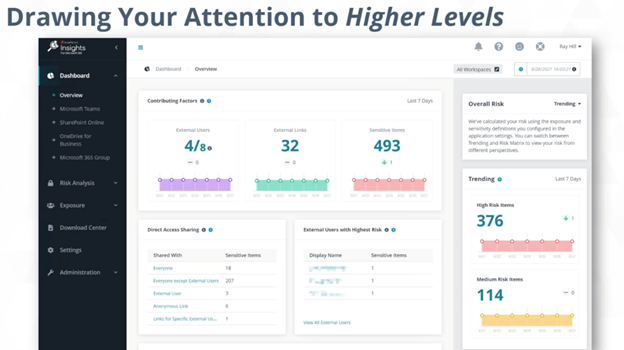
Let’s see a top-down view of how the sensitivity approach mentioned above looks. With the use of AvePoint’s Policies and Insights–which is fully dependent on and connected with Microsoft 365–you can have a more dynamic approach to data security.
With the Insights dashboard, you have a higher level view of your security measures such as DLP. In this comprehensive dashboard, you will have a quick interpretation of your external users, risks, sensitive items, and more.
Layer 3: Securing Workspace
Reality check: you cannot chase down every document just to ensure that it’s secure. After knowing your users and knowing your documents, it’s now time to check your collaborative workspaces. This third layer is as important as identity and data security and is the last piece to the puzzle of having a good security posture for your organization.
If you apply protections and control to your whole workspace, you can be sure that your documents are secure even if there is no configuration made on an item-level. This approach includes:
- Applying sensitivity labels to the whole site and group setting,
- Having a private Teams in Microsoft Teams and mandate external sharing settings, and more
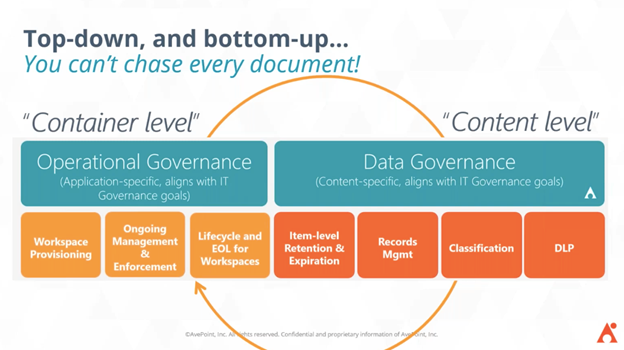
Advantages of a Container-Focused Approach
One of the problems that users often think about is sprawl as it is easy to create many items and objects. Sprawl means that you have more than you can effectively manage. So how can you properly have an inventory of your collaborative spaces?
Through Cloud Governance, you can have a view of all your workspaces, their types, their compliance status, data owners, metadata on a deep level, and more.
Moreover, with this comprehensive dashboard, you can observe ownership details, workspace activities, and policy information in a centralized view.
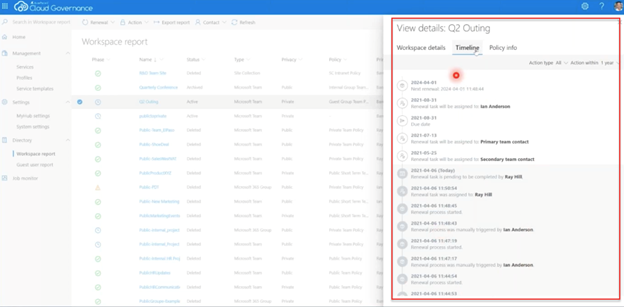
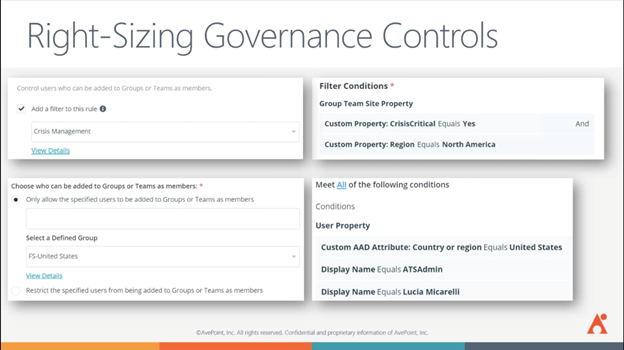
Right-Sizing Governance
Cloud Governance manages provisioning and allows workspace owners to import details. There are periodic reviews and confirmations of permissions, access, ownership, and key governance attributes to keep information current. With this approach, you have governed workspaces, secure data, and managed identities.
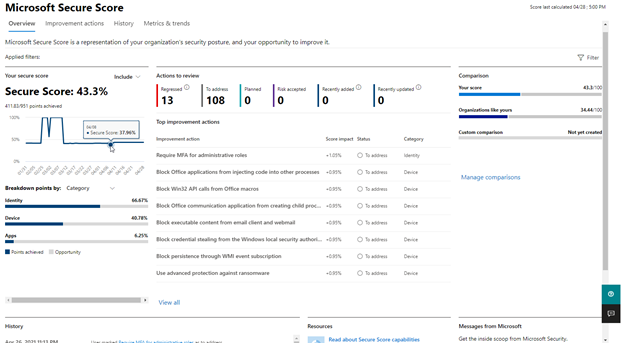
PRO TIP: Microsoft Secure Score allows you to see your security posture by analyzing your scores. You can assess your current settings and it will provide recommendations accordingly. Calculating a compliance score is also available to track your security and compliance standing in your organization.
There are multiple strategies to ensure that your organization is secure, and with this three-layer approach you can achieve strong security posture inside and outside your organization. Watch the full webinar here to understand more about how these security features work together.
Subscribe to our blog for more Microsoft 365 security and compliance updates!
Adrian is currently a member of AvePoint's project management team. In his previous role as a Content Marketing specialist at AvePoint, Adrian covered the latest trends and topics on what’s new in technology, SaaS Management & Governance, SaaS Backup and Data Management.



