New to Microsoft Teams or Office 365 in general? Take our free All-Access Tour on Office 365 Security and Governance Features!
Note: This post is based on a recent webinar presented by Esad Ismailov and Melissa Hubbard. You can find the full presentation here.
Information is the new gold. Every organization has information so valuable that it could lead to crippling fines or worse if it found its way into the wrong hands. However, this post isn’t about repelling hackers; rather, it’s about how to protect against internal leaks from average users in your organization.
The root many data-related challenges come from not knowing what you have and where it is, which is ultimately an effect of improper data governance.
Why is Data Governance/Security Important?
The power of data in driving businesses today is well-recognized. Data is power, and business insights are data-driven. So, it follows that data governance is important as well.
The lack of effective data governance within a company guarantees one thing: the existence of poor data. This poor data manifests itself in inconsistent definitions, duplicates, missing fields, and other classic data faux pas. Some of the most important trends that are causing a greater need for data governance include:
- Increasing data volume from more and more sources, causing data inconsistencies that need to be identified and addressed before decisions are made using incorrect information
- More self-service reporting and analytics (data democratization), creating the need for a common understanding of data across the organization
- The continuing impact of regulatory requirements such as GDPR. This has made it even more important to have a strong handle on where certain types of data are and how it’s being used
- An increasing need for a common business language to enable cross-departmental analysis and decisions
Regardless of the type of data an organization is managing (data warehouse, data lakes, big data, etc.), having strong data governance is essential in enabling the proactive management of data. Data leaks can take any shape and be found in any system; the better the governance and security measures, the less likely a major leak is to occur.
Need advice on how to prevent data leaks in Teams? Check out this post: Click To TweetWhat to Govern
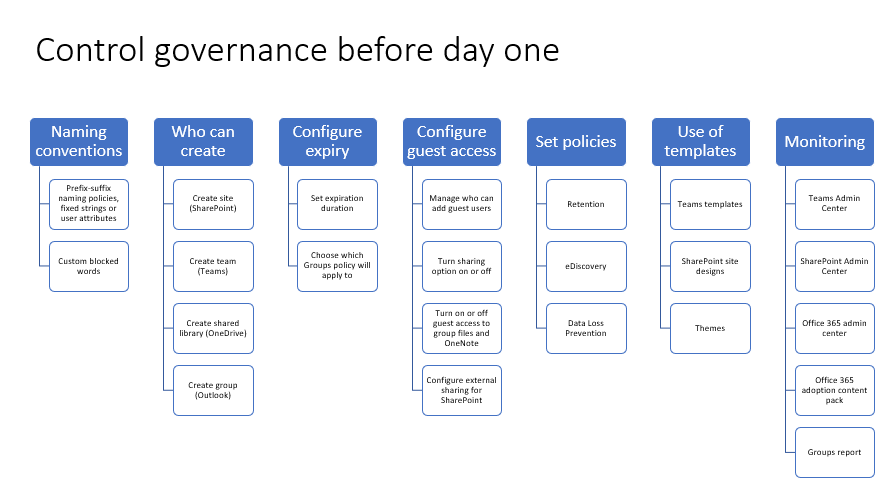
When you think about governance, there are three main things that you want to plan from the start:
1. Provisioning groups and memberships. Who’s going to get access to what, and how will they get into those permission groups? For instance, if an employee joins a company, they can get added to certain groups that contain the content they need based on an attribute that they have in an Active Directory.
2. Protecting group resources. Keeping content/data/group resources safe. How do you do that? By applying policies, thinking about labels, considering multi-factor authentication implementation, and so on.
3. Managing the group lifecycle. How are groups going to be created, and by who? And what’s going to be the lifecycle of that group? Do you want to have expiration policies? Do we want to have an automatic team archival? When does the group start and end, and which of those things can we automate?
Overview of Data Loss Prevention in Microsoft Teams
Recently, data loss prevention (DLP) capabilities were extended to include Microsoft Teams chat and channel messages. If your organization has DLP, you can now define policies that prevent people from sharing sensitive information in a Microsoft Teams channel or chat session. Here are some examples of how this protection works:
Example 1: Protecting sensitive information in messages. Suppose that someone attempts to share sensitive information in a Teams chat or channel with guests (external users). If you have a DLP policy defined to prevent this, messages with sensitive information that are sent to external users are deleted. This happens automatically and within seconds according to how your DLP policy is configured.
Example 2: Protecting sensitive information in documents. Suppose that someone attempts to share a document with guests in a Microsoft Teams channel or chat, and the document contains sensitive information. If you have a DLP policy defined to prevent this, the document won’t open for those users.
Note that in this case, your DLP policy must include SharePoint and OneDrive in order for protection to be in place. (This is an example of DLP for SharePoint that shows up in Microsoft Teams, and therefore requires that users are licensed for Office 365 DLP (included in Office 365 E3), but does not require users to be licensed for Office 365 Advanced Compliance.)

First 30 Days
When we’re talking about data loss in Microsoft Teams or any other collaboration system, you want to start with quick wins. This can entail:
- Searching for and finding sensitive data. This includes identifying your sources (Office 365, Box, Dropbox, Yammer, etc.), the type of sensitive data (CCPA, GDPR, PII, PCI, ITAR, PHI), and the risk and exposure involved.
- Architecting a classification schema for personal data. This requires you to decide if you want to use labels, system, or file data. You also need to build a labeling schema that incorporates personal data, as well as a taxonomy for each label.
Next 30 Days
The next 30 days should be focused on furthering your work in the above areas.
For search, this means:
- Modifying/updating your way of identifying sensitive data,
- Creating custom definitions to find additional data, and
- Automating awareness and delegating responsibility.
For architecting a classification schema, this means:
- Prioritizing auto-applied labels,
- Aggregating incidents and improving false-positives, and
- Enabling human review and re-classification

Final 30 Days and Beyond
Once you’re past the initial 60 days, you should understand what kind of content you have. By this stage, you’re ready to start fine-tuning the last requirements for security management and hone in on reporting.
On the security side, you’ll want to check for any sharing risks by reviewing built-in reports. You can use these to go back and see what was identified as a security violation and try to determine the root causes for said violation. Looking for duplicate files is also recommended, as people will often try to share and use the same file in different systems (SharePoint Online, Microsoft Teams, etc.).
Lastly, an emphasis on logging and retention is a must during these final days. Be on the lookout for integration with Security Information and Event Management systems (SIEM), and go beyond the 90 days of trend reporting to compare teams, locations, and systems. That way, you can utilize multiple signals for multiple systems.
To learn how to define a data loss prevention policy, leverage sensitivity labels and more, be sure to watch the full presentation here!

