Looking for steps you can take right away to make your environment more secure? Check out our webinar on-demand “All Access Tour: Office 365 Security and Governance Features.”
In 2013, the now infamous rogue system administrator Edward Snowden used his access to download and distribute thousands of highly classified documents to many media storage locations throughout the world. In other words, he made a backup of the files and stored them somewhere else.
Many organizations consistently struggle with operational security and understanding how much access is too much for a given individual. Unfortunately, this which can result in privilege abuse similar to what we saw with the Snowden situation.
With the constant needs of collaboration and information sharing being a critical part of running a business, many organizations have realized that they need to adopt different platforms like SharePoint, Box, Dropbox, and other cloud technologies. The challenge, however, is that the majority of these systems store unstructured data. With control being handed down to employees/users, enterprises have little-to-no visibility concerning what content is where and who has access to it.

Compliance Guardian helps organizations centrally define automated policies and make sure content is protected throughout its lifecycle.
During my time within the Information Security space, the top information security concerns IT professionals raise are often:
- Unauthorized or external sharing
- Permission management
- Privilege abuse or too much/uncontrolled access for an individual
In 2019 there are more file sharing options for your employees to use than ever before. These can be used (whether with malicious intent or not) to share content with their colleagues, external partners, or even media sources like Snowden did.
The next Snowden could be anyone. If you prevent people from externally sharing in one system, they will likely find a way to bypass your security controls and use another system. If there’s a possible workaround, employees might assume that it’s not a forbidden method.
This security management burden can be alleviated by continuous monitoring of how your data is being used, shared, and transferred across and outside of your organization. Monitoring your Office 365 tenant and separating the right from wrong actions can be a challenging task for IT, but it doesn’t have to be impossible.
We’ve previously covered how organizations can create alerts, detect what has been shared, and even block external sharing if a file violates the company policy. We’ve also discussed how AvePoint can help you secure external sharing in SharePoint Online, Box, Dropbox, and other cloud applications.

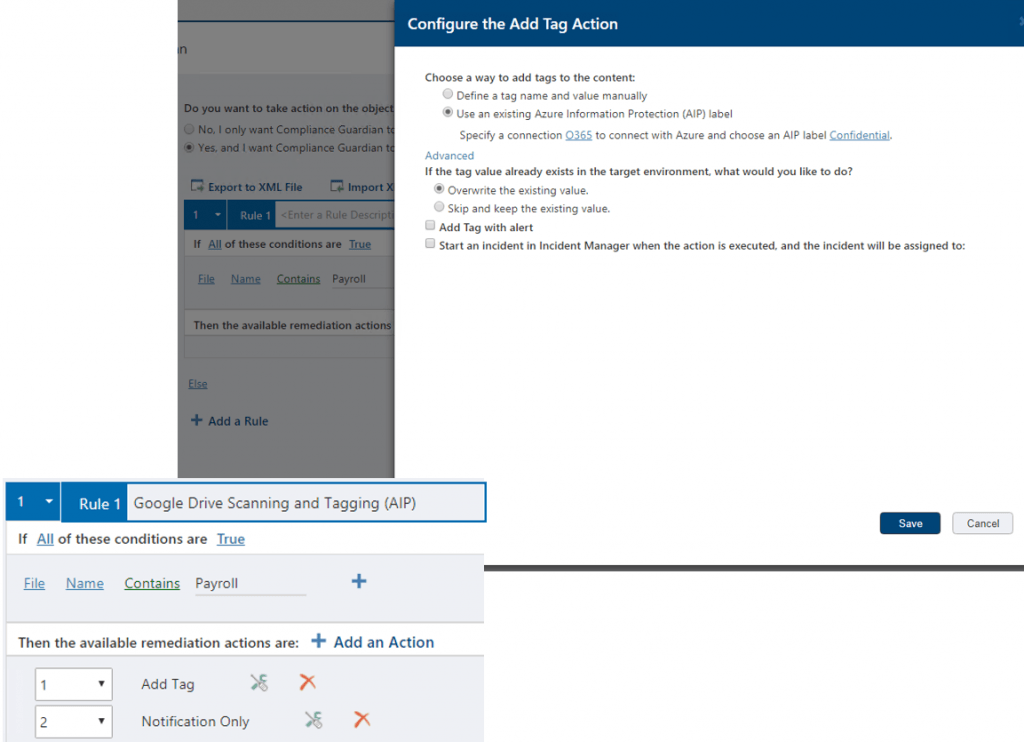
With the latest release of Compliance Guardian 4.4, we extended our cloud data validation classification and protection support for G Suite, specifically Gmail and Google Drive. This allows organizations to—at a minimum—monitor what goes into G Suite and be able to:
- Send an alert to IT/InfoSec teams and create an incident in case a violation occurs
- Classify the documents based on the information within
- Report on what has happened, when, by whom, and much more
Classifying documents allows organizations to easily understand the value of the information and enforce additional security controls. A lot of the external sharing and overexposure issues can be handled via Microsoft’s Azure Information Protection capabilities, but keep in mind that if employees can’t get their job done because an AIP policy prevents them from externally sharing a document from their OneDrive or SharePoint Online, why wouldn’t they try uploading and externally sharing the very same document to Google Drive?
Your Microsoft AIP policy won’t stop them, but Compliance Guardian’s data classification capability can help you maximize AIP’s usage and save the day for your organization.
Snowden wasn’t someone within the highest ranks and wasn’t famous until it was too late. People with too much access/authority are usually not at the same ladder as top management and the challenge comes from top management not having visibility into the existing and potentially risky exposure which brings us to the question ‘What do you do if you don’t have this visibility?” and the answer is simple – you must protect your data at rest and in transit.
For more details on how to prevent security concerns and to see a demonstration of how to address data management challenges in Office 365, click here for AvePoint’s ultimate data protection plan.

