To meet the federal mandate and fully implement the modern security framework Zero Trust Architecture (ZTA), you need to not only develop policies to protect your collaboration spaces but also strategies to enforce them. After all, leveraging modern collaboration solutions without rules or policies could quickly turn your agency’s collaboration environment into chaos.
That said, it’s just as disruptive to set and enforce unnecessary rules. This post will cover the value of right-sized policy enforcement when working to meet federal cybersecurity standards and how to leverage tools like AvePoint Policies to enforce, manage, and monitor policies to achieve ZTA security goals.
The Value of Right-sized Policy Enforcement
While policy enforcement is essential to ensuring your collaboration spaces stay protected and controlled in the ZTA framework, it also needs to be balanced with reaping the benefits of modern solutions.
You could lock down your entire tenant by establishing incredibly restrictive policies, mandating all security decisions and platform management go through a central IT department. However, while this may appear to safeguard your environment, it limits collaboration, overburdens your IT, and pushes your team toward shadow IT, which in turn increases your risk.
Thus, this approach is unrealistic in the long term. A more sustainable model is right-sizing your policy enforcement that makes sense for what you’re trying to protect.

For example, rather than establishing a policy that prohibits all guests access to your SharePoint Sites, create a rule that requires any guest access to Sites that include sensitive information to be verified before being approved. This way, Sites for interdepartmental projects or a joint bureau program can be created without a lengthy and unnecessary verification process while ensuring your collaboration spaces with confidential information have the correct security measures in place.
How AvePoint Enables Proper Policy Enforcement
Right-sizing your governance approach is an effective method for protecting your tenant without sacrificing collaboration or productivity. Unfortunately, native policies tend to be one-size-fits-all, limiting your ability for any special conditions or customizations necessary to right-size your policies.
To customize your security natively, you have two options: manually apply individual policies, or script the actions. The first option would require your IT admin to go into every workspace (i.e., Teams, Groups, Sites) in M365 and set policies, remove improper users from Groups, lock down sharing, and so on. In the case of scripting, while this may be able to apply changes in bulk, this relies on specific users executing the scripts with elevated permissions. Also, if the scripts were to break, you would need to divert IT admins to troubleshoot, adjust, and re-deploy. All of this adds to the administrative overhead.

Small agencies with only a few hundred employees might be able to handle the scenario, but large agencies quickly realize how tedious, manual, and error-prone it can be. It quickly becomes a daunting task to keep up with the pace of creation, let alone change. That means it would be far simpler and more likely for your IT team to revert to applying the same policy across all shared collaboration workspaces regardless of the information stored there or who needs access.
However, leveraging a third-party tool could streamline this process and enable right-sized controls. For example, AvePoint Cloud Governance can automate IT services while combating policy risks by requiring a questionnaire to be filled out for a new workspace. Now, IT can ensure users set up the correct type of Team or SharePoint site with the right level of access to internal and external members without manual intervention.
Using AvePoint Policies, you can automate rules for access, settings, or other configurations based on your groups – allowing for proactive, automated policy enforcement. Once established, you can apply these policies based on the type of workspace at the point of creation. See an example of different workspaces and the policies that apply.
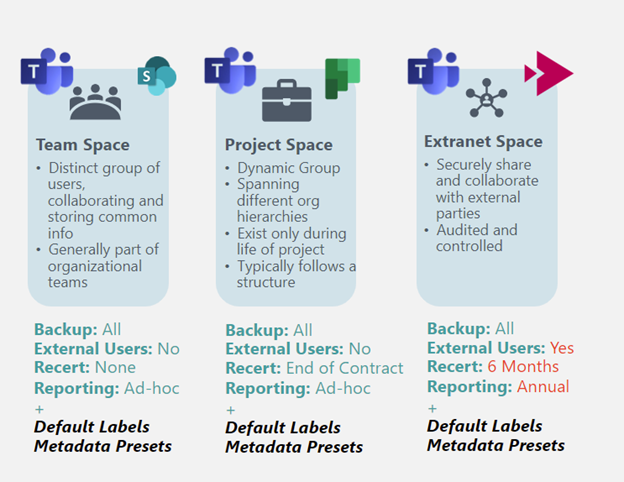
These two solutions work hand-in-hand to ensure you apply and enforce right-sized policies to your collaboration spaces, securing your environment while enabling collaboration and productivity.
Monitoring and Managing Your Policies
While enforcing policies is a good start, you must continuously monitor your policies across your workspaces to ensure the right policies are applied. Similar to issues we discussed in our previous post on cataloging workspaces, the purpose, organizational structure, or even applicable regulations of collaboration spaces often changes over time. The policies or categories you applied at provisioning might need updating.
AvePoint Policies allows you to perform ongoing monitoring with visibility into workspace inventory and act on data sensitivity alerts or re-certifying inactive users or workspaces. If you notice something off, you can either individually or bulk manage your policies, updating rules and propagating across necessary workspaces seamlessly.
For example, perhaps you have Teams workspaces that contain need-to-know content specific to your agency. You realize some of your internal team has been inappropriately sharing this information across agencies through the SharePoint site. Since the sharing is through SharePoint, the Teams owner would not have known about these “shadow users.”
With proper auditing insights and a few clicks of a button, you can update the policies on these Sites, remove shadow users, and track down the overshared sensitive information. Additionally, enforce the policy across these Sites and Teams until a time when you decide you’re ready to revert the workspaces to their original policy.

The Bottom Line
You can create and enforce policies natively. However, this will leave you with over-restricted workspaces, an overburdened IT team, and an environment left unsecured. Leveraging third-party solutions like AvePoint Cloud Governance and Policies will enable you to get ahead and apply right-sized policies and streamline updates as conditions change, protecting your environment with ease.
This post is part of AvePoint’s Zero Trust and Your Agency’s M365 Collaboration series. Stay tuned for additional posts addressing strategies and solutions to implement Zero Trust Architecture and combat gaps in your security over the next few months.


