Now more than ever, there’s a critical need to secure data and systems in the cloud. We’ve seen the Kaseya, Colonial Pipeline, and other major attacks disrupt thousands of organizations around the world—this can happen to your organization at any time.
Cybersecurity is more than just planning for better technology. We’re seeing the ever-evolving vulnerabilities often getting beyond what security teams alone can address themselves.
To build a stronger defense and solid ransomware protection, there’s a need to involve your business stakeholders in your security stance. Here are five key reasons why security awareness training matters.
1. The leading ransomware attack vector is phishing.
Today, ransomware remains one of the top nightmares for security leaders. The costs involved are a steep price to pay—not only in terms of money but also in the business disruptions, the harm to your brand image, and the consumers’ loss of trust it can bring.
What’s scarier is the fact that technology alone can’t prevent ransomware from happening. One wrong click from one of your users can start a chain of ransomware attacks in your system. Your users also have a role to play in keeping ransomware at bay.
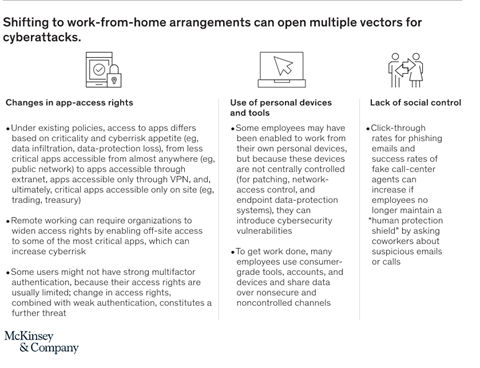
With the remote setup most organizations are now enabling, there’s a wider attack surface to defend. Identities have become the parameter by which you’re relying on your organization’s security, making ransomware attack prevention a much more complex practice.
To ensure a strong cybersecurity stance, you need solid cybersecurity hygiene. Some good practices include enabling:
- Strong passwords
- Multi-factor Authentication (MFA)
- Restricted access
Users may not always understand why there are various security measures to uphold, so security awareness training better helps them understand the value of their compliance due to the role they play in your overall security.

2. Attack vectors are evolving and will continue to evolve.
When we say training, it’s more than just a webinar or a catch-up call on what ransomware is and how phishing attacks happen.
Attack vectors will continue to evolve, and as your security team catches up on those with the best ransomware attack protection technological advancements, continuous security awareness training must also be enabled.
The changing nature of cyber risks means your users must also know how to adapt to your security practices.
Investing in a security awareness training program will empower your users to protect against ransomware—even in its new and evolved forms—as your organization continues to grow.
3. The value of a risk-based approach is critical.
It doesn’t end with user awareness, though. Helping users understand that some may have bigger responsibilities than others is also crucial.
An employee who has access to sensitive information needs to be more careful than the one who simply uses Microsoft Word to write drafts. The reality is that you can’t protect all of your data at once.
To adapt to this reality, a risk-based security stance is being adopted all over the world. This approach recognizes that not all data is created equal. And because you can’t protect all of your assets, ensuring that your security is at a maximum for your crown jewels is crucial.
Having extra measures to train your employees with access to those crown jewels will then be key to strengthening your security.

4. Cyber risks can be contained with visibility and swift action.
Despite all of your security measures, all organizations will always be vulnerable to cyber risks to some degree. And when it happens, the best thing to do is to address it swiftly and eliminate any chances of it becoming a bigger threat.
To do this, you need to plan your course of action. For that to be effective, you need to enlist the help of all business stakeholders, from your users to business leaders.
When a phishing attack or any user-centric ransomware attack happens, your users need to know who to report it to. Your security team then needs to know what course of action to take next and how to coordinate with the business leaders for critical decisions. This way, gaps can be recognized and easily addressed.
The timing and urgency of a cyber risk response are crucial. To avert any larger crisis from happening, a clear security approach needs to be communicated well and regularly.
5. Security awareness training is now a business necessity.
We’ve heard it enough: security is more than just an IT job. It’s a business necessity organizations must invest in.
A security-minded organization is posed for business growth, especially in the digital world, because they become proactive in finding solutions to mitigate risks and possible disruptions in advance.

For your security programs to thrive, they must resonate with your executive leaders. Quantifiable benefits should be presented, and real-life risks must be articulated, which is where effective security training comes in.
Security awareness training must go beyond your users. Get your executives, partners, vendors, and other third-party alliances involved to ensure a holistic cybersecurity stance.
The Best Ransomware Protection for Businesses
Building your security awareness training is only one phase of the whole cybersecurity design. Learn how to be protected from ransomware better by leveraging enterprise ransomware protection, such as what’s offered with Microsoft 365.
But while extremely helpful, Microsoft’s native ransomware protection tools can often be complex and still have certain limitations. To get more holistic ransomware protection, prevention, and recovery plan, you can utilize third-party ransomware protection solutions.
AvePoint’s Ransomware Protection Toolkit, for example, helps organizations build a resiliency plan by offering strategy tips, best practices, and solutions to not only protect your data and systems but even protect backups from ransomware.
Ready to build your solid line of defense? Dive into our toolkit now.

