How to Catalog Your Workspaces to Meet the Zero Trust Mandate

The first step in any security exercise is to discover and take inventory of what you need to protect. While most agencies that adopt Zero Trust Architecture (ZTA) know this step is critical, many will fall short and not include data inventory. Typically seen as an impossible roadblock, there is a way to inventory data without diving into the containers: workspaces.
Ignoring workspaces like Microsoft Teams or Groups and SharePoint Sites when completing this exercise not only misses the opportunity to step into data inventory but can also be a dangerous pitfall to your security. These spaces are hubs of collaboration and information sharing for most organizations; left unchecked, you could end up with overprivileged users, unsecured collaboration spaces, exposed sensitive information, and a data spill (be it CUI, PII, or DOD Classifications).
Fortunately, you can avoid this pitfall if your admins have an inventory of all created workspaces and an ongoing process to check that the appropriate policies are applied. This post will discuss how cataloging your workspaces can help you meet ZTA standards within your collaboration environment and how to secure your entire inventory of workspaces.
How to Catalog Your Workspaces for Zero Trust
You can manually catalog and maintain your workspaces. Each time a new workspace – whether a SharePoint Site Collection, Group, or Team – is created, you can add it to a spreadsheet or M365 List. Be sure to include information such as Team owner(s), mission/business purpose, expected content sensitivity, internal stakeholders, external users and their affiliations, and any other information that could affect the policies that apply to the workspace.
Next, either set a reminder to check in on this workspace or set a specific date that you will review all workspaces at once to make any necessary changes (whether for ownership, access, permissions, etc). This should happen regularly and routinely to ensure your inventory is up-to-date and your workspaces are healthy and secured. And don’t forget, not every workspace has the same policy for lifecycle, renewal, and security!
After all, your workspaces are living, breathing spaces and often evolve over time, such as the purpose changing from short-term to operational, a new Team being created to manage a new project, or additional people, like vendors or contractors, needing access to a legacy workspace. You need a record of these changes to make necessary policy amendments and confirm the proper policies are applied.
Streamline Inventory of Workspaces
Sounds tedious, right? Fortunately, there is an easier way. Solutions like AvePoint Cloud Governance can streamline the inventory of your workspaces. Leveraging the solution, you can create a report that is an inventory of all the workspaces created in that tenant. This report gives your admins one view of your workspace inventory and the ability to add columns to monitor and act on certain things like “renewal” activity or how many members are in that workspace. You can even break this down to component/department admins with delegated views of their content without overexposing them to other content.
From within the solution, you can easily automate service requests and management of content ownership, policies, and lifecycle, according to evolving business needs. For example, the solution shows a user’s risk details during the renewal process, ensuring owners are aware of high-risk content in their workspaces as well as exposure level details, which allows them to make informed decisions as they review and promptly act.
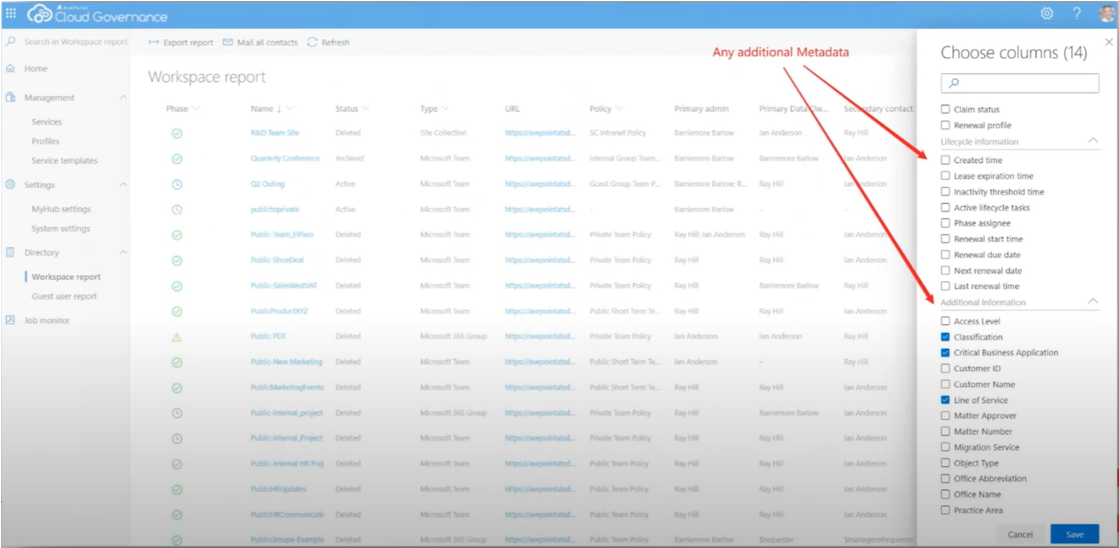 Features like this level up your security, simplifying and automating oversight of configuration settings, workspace membership, permissions and sharing links, and ownership change requests with the ability to delete, revert, or notify users about unauthorized changes. It will also provide a periodic attestation process for Sites, Groups, and Teams, ensuring ongoing compliance.
Features like this level up your security, simplifying and automating oversight of configuration settings, workspace membership, permissions and sharing links, and ownership change requests with the ability to delete, revert, or notify users about unauthorized changes. It will also provide a periodic attestation process for Sites, Groups, and Teams, ensuring ongoing compliance.
With this information on hand, you can properly and seamlessly enforce your new ZTA framework. In fact, when you know what you need to protect, you can create more sophisticated security rules to truly customize policies based on needs. Once you have your catalog, you can:
1. Establish Better Policies for Your Workspaces
After you catalog your workspaces, you have a guide – what workspace do I have, how are they being used, and expected sensitivity. Once you know what data is stored where and its sensitivity, you will be able to establish better policies that enable productivity and collaboration while protecting your most sensitive data.
2. Confirm Appropriate Rules Are Enforced
If the conditions of your workspaces change, you need to apply the appropriate policies to meet these changing needs. With a catalog of your workspaces, you can better track changes, such as an owner leaving the Team or inappropriate guest access, which allows you to remediate the issue before it becomes a bigger problem.
3. Create Interdepartmental Consistency
With a full list of workspaces, their data sensitivity, and applied policies, you can better create policy consistency between departments, ensuring appropriate use and utmost security. This consistency also streamlines interdepartmental collaboration, as there is no question whether a workspace will be secure enough for your sensitive data.
4. Reduce Central IT Burden
With an inventory in hand, your administrators can push the responsibility of renewal and recertification down to the workspace business owner, which reduces the burden on your administrative team. Equally as important, it also ensures the person who knows the use and expectations of the workspace are actually the ones making these important decisions.
No matter the security issue, whether your Team owner leaves, your workspace’s purpose changed, improper access is granted to your Site, or you are making practices changes to implement ZTA, among any other host of issues, attempting to solve them without knowledge of your workspaces will be near impossible. However, when you have an accurate record of your workspaces, including key details about them, you can streamline the implementation of right-sized policies and verify they are working.
The Bottom Line
At some point in time, all of us have lost a Tupperware of leftovers or an old vegetable in our fridge, only discovering it after it was already festering and molded. This universal experience can be a headache to clean up and a bit gross, and a version of it could happen in your Microsoft 365 if you have collaboration spaces in your tenant that you don’t know about.
Except, if you have a workspace you don’t know about, it won’t just mold – it could serve as an entry point for any sort of threat actor, from malicious insiders to cybercriminals, looking to take advantage of your vulnerabilities and gain access to sensitive information for the thrill, profit, or other nefarious motivations.
The solution is simple: maintain a catalog of your workspaces. With the right tools, inventorying your workspaces can be a simple, routine process that allows your admins to keep an eye on your workspaces without overburdening them, enabling them to keep your tenant secure and protected. Do this properly and you’ll meet the Zero Trust standards in no time.
Subscribe to our Microsoft 365 Government Community call for more tips and tricks on cataloging and request a demo of our Zero Trust solution to make aligning with the federal mandate simple and seamless.
You can also read more blog posts about Zero Trust and learn how to meet federal Zero Trust standards with Microsoft Sensitivity Labels in this webinar!
Subscribe to our Microsoft 365 Government Community call for more tips and tricks to utilizing M365 as a Federal agency.

Antoine Snow is a senior solutions manager at AvePoint, leading the Public Sector business unit. He has held various positions in IT over the past several years ranging from front-end web developer to Microsoft 365 Service Owner. In his current role, Antoine focuses on governance and adoption challenges plaguing the modern workplace and helping government organizations understand the components of a governance strategy and its implementation. Antoine's views on these topics can be found in various blog posts and has been the focus of one-to-one workshops.

I sell software, but my passion is to help translate the needs of the business into the capabilities of available technology. Over two decades in tech I have helped customers analyze collaboration solutions against actual mission needs in helping them select the best path based on their personal critical success factors. Per my training I’m a project manager (PMP), an engineer, an architect, and a designer; but ultimately, I’m a problem solver.





