Microsoft Power Platform adoption grew 72% in 2022 as the need for optimization skyrocketed demands for its process automation, analytics, and low-no code apps – and your organization is likely seeing an uptick in usage as users seek its innovative productivity tools. As your team’s usage matures, the complexity will grow, and you will likely be managing multiple environments.
This isn’t a bad thing – in fact, it’s a best practice to maintain control and prevent mistakes. However, as with anything, more complexity can mean more work or even security risks. The good news: these management complexities can be easily overcome with the right solutions in place.
Let’s discuss the pros, cons, and solutions of using multiple environments as part of your Power Platform DevOps strategy.
What is a Power Platform Environment?
Power Platform environments are the containers in which you create, manage, and share your Power Apps applications, Power Automate workflows, Power BI workspaces, and Virtual Agent chatbots.
When getting started with Power Platform, you will have a single environment in your tenant called the default environment. You may find that this single environment is all you need to control development and secure your data in Power Platform. However, most organizations find that having multiple environments (for example, a sandbox, test, and production or multiple regional environments) offers better management and security.
Getting Started: Power Platform Environment Strategy
Organizations utilizing multiple environments must establish a strategy to manage these environments, including the specific purpose each environment will have, to ensure appropriate security measures are in place to support productive development. How you build your environment strategy will depend on the different types of users you have, specific security requirements, or even the type of apps and workflows you are building.
For example, if you have offices in multiple regions in the world, your environment strategy may be built based on geographic locations, creating environments for each branch to keep data in the correct regional data center. However, if you’re an organization with only one office, but many eager developers, you may be more concerned about isolating applications in development, creating multiple developer environments or sandboxes for users to troubleshoot in. And, if you’re a huge enterprise that faces both issues, you may find yourself building a strategy that combines these requirements.
There is no one right way to build your environment strategy – each organization has different needs, and thus their strategy will look different. But that’s also why it’s so important to understand the potential risks or roadblocks of your strategy to prepare for and mitigate them.
The Pros and Cons of a Multiple Environment Strategy
PRO: Control access to sensitive data.
If you want to grant some developers access to sensitive data, it’s best to do that in an environment separate from your default so not everyone has access. Using DLP policies and multiple environments, you can establish environment-specific policies that allow certain connectors in some environments.
For example, you likely don’t want connectors that enable access to sensitive data, like Dynamics 365 or DocuSign, in your default environment. However, you could allow it in a sandbox or developer environment with access limited to a select few users. This empowers your power users and advanced developers to innovate without restraints but avoids putting your data at risk for overexposure or even alterations if a novice user accidentally publishes a buggy code.
CON: You must carefully manage security groups.
It’s not enough to simply create a new environment and label it “For Power Users.” That’s because, if you create a new environment and don’t have an associated security group, every user with an active Power Platform license will be added to the environment automatically. You must properly manage your security groups and tag all new environments with the appropriate group to avoid this risk.
While associating the appropriate security group is the first step to securing your environments, the risk doesn’t completely go away. One small mistake – like adding your new records management intern to the wrong security group – could grant them access to all sorts of environments they shouldn’t have access to.
Security groups also don’t limit the actions your users have within an environment. While you hope you can trust your power users and admins, mistakes happen, and you could expose or even lose data. When it comes to sensitive data, “oops” isn’t a good excuse and certainly won’t stand up to compliance. You need a way to manage your security groups that better control access and prevent mistakes.
SOLUTION: AvePoint EnPower helps you manage your security groups better with deeper security group settings. Once you have set up your security groups, you can enforce your settings with an AvePoint EnPower policy. Should a user be added to your environment who doesn’t meet the conditions you’ve set it, AvePoint EnPower will flag the violation, making it easy for you to find and fix a security issue before it becomes a problem.
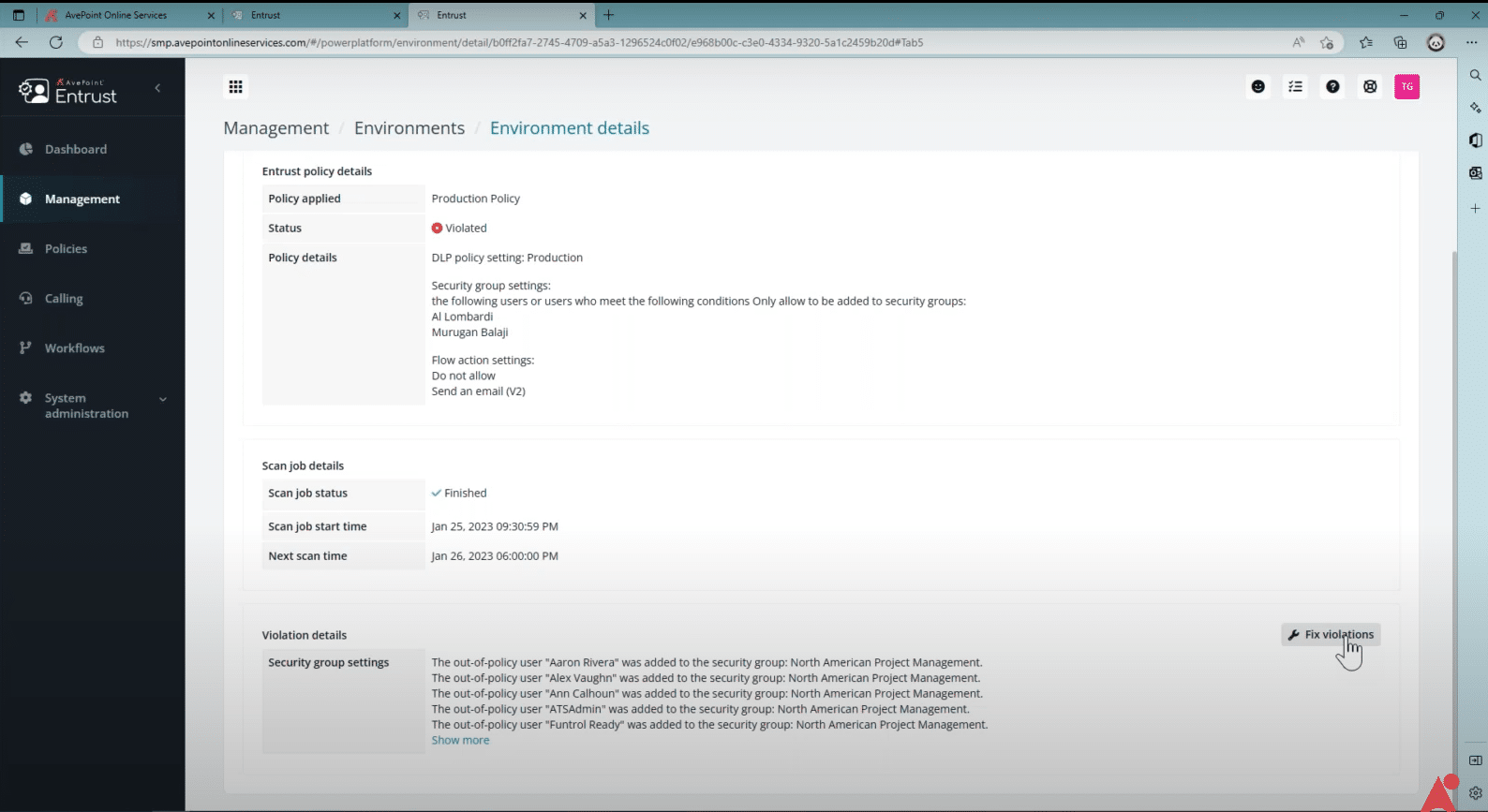
With AvePoint EnPower, you can also set granular data loss prevention (DLP) policies to prevent specific actions in an environment, adding another layer of protection. For example, you can set a policy that blocks actions like “delete file” or “copy data.” This not only prevents mistakes but should unapproved users accidentally gain access to these sensitive environments, it will limit what they are able to do there.
PRO: Isolate applications under development.
While some of your apps are likely fine to be built in your default environment – think, applications for personal or even team productivity – your most critical should be separated into their own environments. This allows you to control access to your important connectors and protect sensitive data.
It’s also far too easy for changes during development to impact users in production or even corrupt data. To avoid mistakes, it’s a best practice to isolate these applications until they’ve been tested and proven to work.
Isolating applications is also a great way to train new developers, allowing them to trial and error without the risk of damaging any applications in production. This becomes increasingly more important as your organization’s maturity grows and you are onboarding more and more developers, particularly those without application development experience, to the platform.
CON: You need to manage all these environments.
To create a business-critical application, it’s best practice to build a sandbox or developer, test, and production environment for it to live in. Multiple that by however many apps your team is creating in a month and that’s how many environments you may be managing, on top of standard environments like your default and production ones.
When you have dozens or even hundreds of environments, you will need to work double-time (or triple or quadruple, depending on how many environments you need) to make sure each environment has proper management. This will become increasingly more difficult, particularly as you start building out new sandbox, developer, and trial environments. Some, like trial environments, are meant to be temporary, but must still be properly configured and controlled to avoid mistakes or exposures. This means a lot of work for your IT team as they attempt to apply the proper controls to each new environment (where it is easy to misstep, as we already discussed in the above example).
Ultimately, your centralized IT can’t manage it all on its own, which will mean either limiting productivity for the sake of control or sacrificing security for the sake of innovation.
Find out how to scale and transform your Microsoft 365 and Power Platform administration:
Read More
With AvePoint EnPower, you can create permission groups, perhaps by department or region, delegating the administration of these environments to trusted resources. You can choose which environments each admin will control as well as specific actions they can perform within those environments, allowing you to keep a handle on environment management without overburdening your central admins.
Then, you can keep an eye on activity across your environments with centralized dashboards, which provide a single pane of glass visibility of creation, trends, and rankings across your Power Platform products. Should something look off, you can take individual or bulk action, right from the dashboard, or even bulk update permissions, making changes to your governance strategy easily.
PRO: Control which apps and flows are published.
One of the greatest aspects of Power Platform is that anyone can create anything. But that could quickly become its downfall as your users become more confident and comfortable creating new apps and flow. Soon, you could be managing hundreds or even thousands of new objects without quality control.
This is where additional environments come in. You can lock down environment creation, requiring any new environment requests to be filtered through your admins. Then, when you follow the recommended application lifecycle (sandbox/test/production), your developers will have to request a new environment at each stage (sandbox to test, test to production), giving your admins the opportunity to review objects throughout the process.
This keeps communication flowing between your admins and developers. It also gives you control over which you push to production, which may need some finetuning, or even which may be duplicative and unnecessary for your resources to manage.
CON: Sometimes, an object works in one environment and not the other.
There’s really nothing worse: you spend hours putting together the perfect solution to a business problem, testing it again and again to confirm it will work once it’s live, only to receive an error message when you try to transfer it to the new environment.
Whether because of permission configuration or connector limitations, there are many reasons an application may work in one environment and not another, and it’s not always easy to determine the culprit. If your team faces this regularly, they may stop building in your controlled environments and seek out other, unsanctioned options; after all, people will do what they need to do to get their job done.
While annoying for the individual, this can be detrimental for your business-critical objects. For example, there are times when an app or workflow that started as a resource for a specific team becomes useful for the entire organization and must be moved from that department’s production environment, where there may be less security controls and resources servicing it. However, moving to a more secure environment isn’t always without hiccups – you could spend hours ensuring it transfers correctly and the appropriate permissions carry through.
SOLUTION: With AvePoint EnPower and AvePoint Fly, maintaining an environment strategy is a breeze.
With AvePoint EnPower, you can replicate apps and flows across environments with ease. Before moving an app or flow from one environment to another, analyze its components and Connector(s) to ensure a successful move.
Then, move seamlessly from environment to environment (or even tenant-to-tenant) with Fly. You can map, filter, and schedule, or migrate in real-time, all while Fly maintains permissions, metadata, and associated flows or apps during the move, so you don’t lose data along the way.
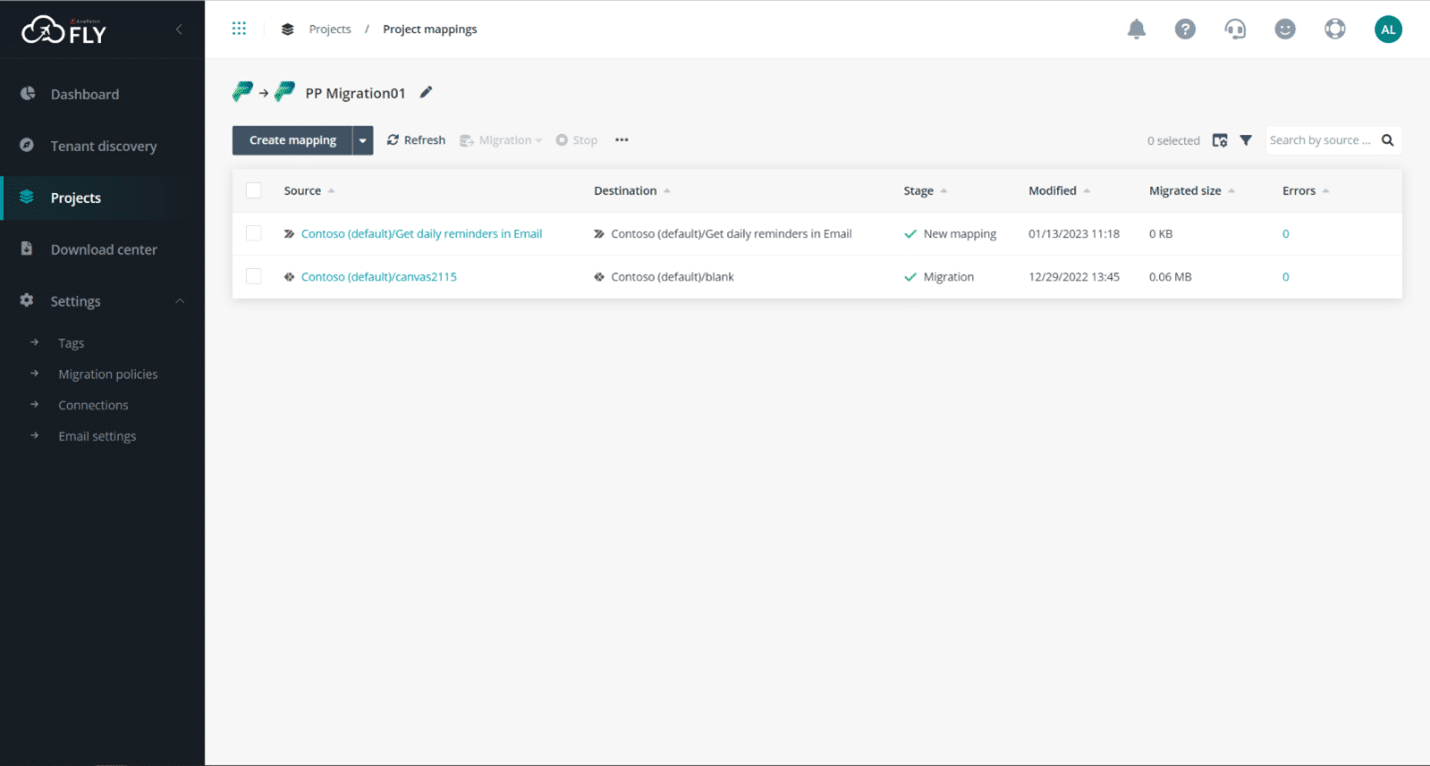
That means an application that worked in test will easily move (and work!) in production, saving you time and a headache while maintaining necessary security controls.
Verdict
Ultimately, a multi-environment DevOps strategy is key to controlling your Power Platform and staying agile as your team’s usage matures. However, this comes at the cost of added complexity, introducing new risks if not properly managed. While you can build a multiple-environment strategy without a solution like AvePoint EnPower, you may be sacrificing usability, scalability, or even security if you do.
AvePoint EnPower helps you balance both security and functionality, scaling your Power Platform to a large set of secured environments without losing control. This means your citizen developers and your pro developers can safely build all the apps they need to drive efficiencies and productivity while allowing your admins to sustainably manage the platform long-term.




