Introduction
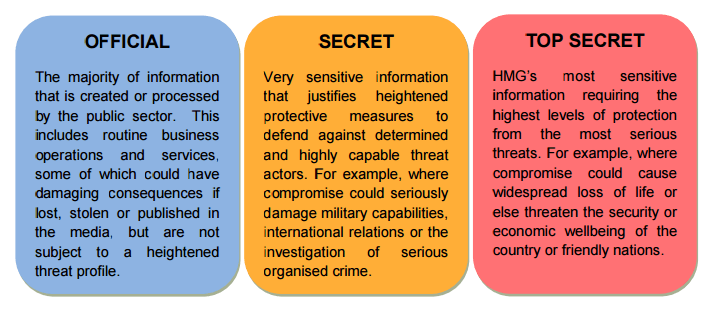
In October 2013, the UK government published the Government Security Classification (GSC) outline to ensure that all public sector organizations collect information appropriately. An important part of this outline is classifying information that is collected according to level of sensitivity. Under the GSC, there are three levels of classification:
These classifications replaced the original Government Protective Marking Scheme (GPMS), which had six levels: Secret and Top Secret (retained in the new GSC), plus Confidential, Restricted, Protect, and Unclassified. There were two big problems with the original scheme:
1) Unclassified was often the default classification in many organisations’ document management systems.
This meant that sensitive data could be marked Unclassified by default. It also meant that if you added sensitive information to an Unclassified document, its classification wouldn’t be updated automatically – making it incorrect. Labelling something as Unclassified was meant to show that a document had been checked and verified as not being sensitive.
2) The differences between Confidential, Protect, and Restricted were very slight and open to interpretation, which led to confusion as to what classification should be used in certain circumstances.
The new GSC has made two very important changes to correct these problems. All public sector documentation now has to be regarded as Official as a base layer of security. That content should then additionally be categorized as either Official or Official-Sensitive. Official-Sensitive is defined as a document containing information that, if lost, stolen, published in the media, or otherwise put into the wrong hands, would have damaging consequences.
Key Classification Principles
There are four key principles that govern classification:
1) All government information has intrinsic value and should be classified.
The onus should be on the document creator/owner to prove that the information is useful, required, and in regular use. Otherwise, it should be removed from the repository.
2) Everyone who has access to government information has a duty of confidentiality and should protect it regardless of classification.
Although the new GSC categorizes public sector documents as Official by default, your information will be more secure if you treat it as being at the highest level of security that your repository allows, unless specifically marked. For example, if the repository is selected as being suitable for Secret documents, then all documents should default to Secret unless specifically classified otherwise. I also recommend checking the classifications on a regular basis to ensure that they are still correct.
3) Access should only be granted on the basis of a genuine “need to know.”
When managing permissions, think about why each user needs access to the information. Permissions should only be granted when absolutely necessary, then revoked once the need is gone.
4) All information exchanged between internal and external partners should undergo the same protection and conform to the relevant legislative and regulatory requirements.
If you share information, you must take responsibility to ensure you are aware of and follow required rules, policies, and processes. Also, organisations should take steps to make it possible for parties to safely share information externally without breaking those rules. The organisation’s infrastructure should be flexible enough to allow you to do this without compromising the security of the environment.
How does this work in practical terms?
This is a relatively simple process to implement when creating new documents. Official documents do not technically need to be marked, but it’s a good practice to classify everything.
Within the Official-Sensitive classification, there are three additional descriptors which can be used:
1) Personal: The information relates to an individual or group, and inappropriate access to this documentation could have damaging consequences.
2) Commercial: The information is commercially sensitive and includes statutory or regulatory requirements.
3) Locally Sensitive: The information is sensitive to a specific region and shouldn’t be accessed by users in other geographic regions.
While these descriptors are not mandatory, it is best practice to apply them where necessary.
When working with Official-Sensitive, Secret, or Top Secret documents, classification needs to be clearly marked throughout. For digital copies, this means indicating classification in the header and footer. Printed documents should have the classification marked on exterior points, such as the outside of a binder containing the paperwork. When emailing these documents, make sure to include classification in the subject and body of the email.
In addition, there are established handling instructions for preventing specific documents from being distributed, printed, or emailed. These handling instructions should be clearly defined:
- On the front of any document
- In the first page of any letter
- Within the first paragraph of the email containing sensitive documents
- In the operational instructions for any given dataset
Classifications and the Cloud

Some public sector organisations have been hesitant to move to platforms such as Microsoft Office 365, as they are wary of storing sensitive information in the cloud. However, if you adhere to GSC, it’s easy to understand what data can live where.
- Official documents can be stored in the cloud as long as appropriate permissions are maintained.
- Official-Sensitive data can be stored in the cloud as long as you provide access strictly on a need-to-know basis and can prove that only the appropriate people have permissions. If there is ever a breach, then you can easily find the source of the breach by reporting who has access to the documents in question.
- Secret content should only be stored in secure locations. Typically, to store Secret information in a data centre, it must be located within the UK and have the appropriate security provisions and safeguards in place. Access to Secret content should only be given to people with Security Check (SC) clearance.
- Top Secret documents should only be stored in Top Secret-rated secure locations, such as locations with secured access for only personnel who have Developed Vetting Clearance.
Transitioning from the GPMS Classification Scheme
For new documents, applying GSC is relatively simple – you can create the appropriate classification schemes, repositories, and processes as you create new content. The difficulty lies in transferring from the old classification format. Unfortunately, there is no clear way to translate GPMS classifications to GSC.
You could argue that anything considered Unclassified under GPMS could be archived or disposed of, but this could negatively affect a large percentage of your existing content. You run the risk of accidentally deleting important content that you failed to classify correctly before. For example, you may have Unclassified documents that should now be marked Official.
Then, there are the Protect, Restricted, and Confidential classifications. These can typically be sorted as either Official or Official-Sensitive, but if the descriptors are not up to date or applied at all, then you’ll need to do some work to determine which classification is appropriate for each document.
Tip: When updating document classifications, be sure to avoid altering any metadata. Let’s say you have a retention policy that says documents should be deleted two years after the last modified date. Make sure changing or adding the new classification does not change that last modified date.
AvePoint and GSC
At AvePoint, we help customers determine the best way to reclassify existing content in unstructured locations without having to manually investigate each document. We work with customers to specify a set of parameters around the information which is held within the documents, and we can then classify the documents. We can also change the header and footer classifications within the documents based on these processes and add extra metadata (such as the descriptors) if it can be determined from the content. As each customer’s needs are different, we offer workshops to help identify the different requirements and work with them to develop the parameters. We have GSC parameters as an out of the box configuration, but there are instances where customers require some extra options in addition to these standards.
For customers with terabytes of information, this is a huge time-saving exercise. It is also much more accurate, as we use a number of algorithms and checks to ensure that the scans and classification of the documents are done correctly and quickly.
We also provide a secure migration service to the cloud and offer continuous monitoring of the cloud and on-premises storage to ensure that the security provisions, classifications, and descriptors can be automatically added to the document based its contents. We can also provide custom, department-specific tagging, and metadata rules to reduce the burden on your IT staff. This allows for the number of required metadata fields that the end users have to complete to be kept to a minimum.
In addition, we can also provide for the facility to securely share appropriate documents securely, based on the classification level of the document, prevent the unauthorised sharing of these documents and manage the permissions of the documents across hybrid, cloud and on-premises locations from a single interface.
For more information, watch our two-part webinar series on UK public sector data classification for cloud readiness.