Office 365 Compliance Center and Beyond


Data protection is an ever-changing space. And with the continuous development in both technology and global regulations, we’ve been put into a position where we really need to evolve our approach to how we protect our data more than ever before.
The evolution of cloud technology means there are constantly new ways for us to create, collect, and share information across devices and around the world. At the same time, awareness of such an ease of access to information has driven new laws to come into place that aim to enhance the protection of individual’s rights to privacy amid growing digital global commerce.
Data is no longer local and confined to individual servers and buildings. Where files used to be sent to specific individuals only, they can now be shared as a link to be viewable or editable by “everyone” with just a click. So trying to detect what’s being sent and to whom is now a completely different game.
Data protection now has to go beyond encryptions and firewalls, because it’s not just a matter of data being sent to the wrong hands, it’s more a matter of the wrong information being in the wrong place, and the wrong people having access to it. So your protection strategy needs to start with the data itself:
- What is it?
- Where should it live?
- Who owns it?
- Who should see it? More importantly, who should NEVER see it?
Let’s take a look at the Office 365 Compliance Center, which houses the native compliance-related features for an Office 365 administrator. What can you do with it, and what are the limitations out-of-the-box?
Data Loss Prevention (DLP) Queries
Microsoft’s DLP features in Office 365 offer ways for you to understand the data you have. One of the key components is the ability to run DLP queries that target specific data types. This allows you to identify data for classification (such as International Traffic in Arms Regulation, or ITAR) so you can better plan a risk-based data governance strategy.
This also gives you a way to locate Personal Identifiable Information (PIIs) such as HIPAA or PCI to address violations from regulations such as the newly approved GDPR, set to be enforced starting May of 2018. For more information on the GDPR itself, check out our GDPR Response Guide.
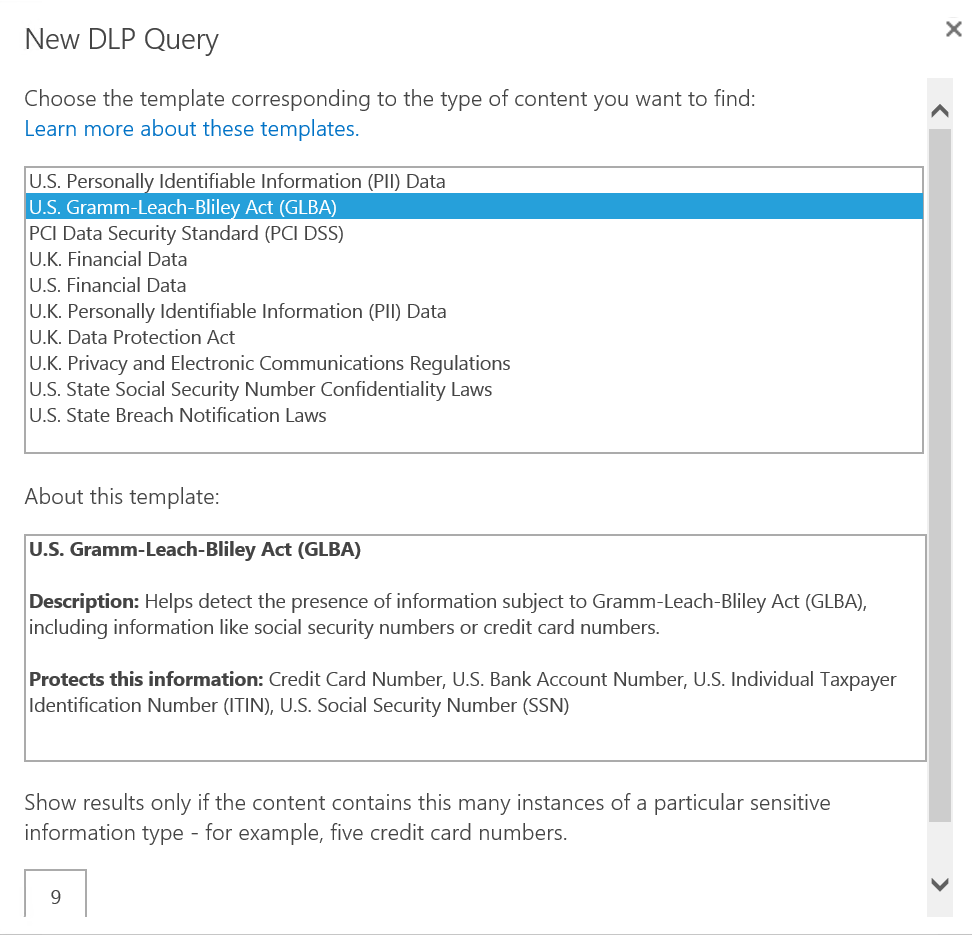
Office 365 sample DLP queries.
Spot trends over time to identify potential areas that needs adjustment. One thing to note is that while built-in queries are numerous and allows you to get started quickly, there are limitations to Microsoft’s out-of-the-box offerings when it comes to what you can configure, customize, and extend in these rules.
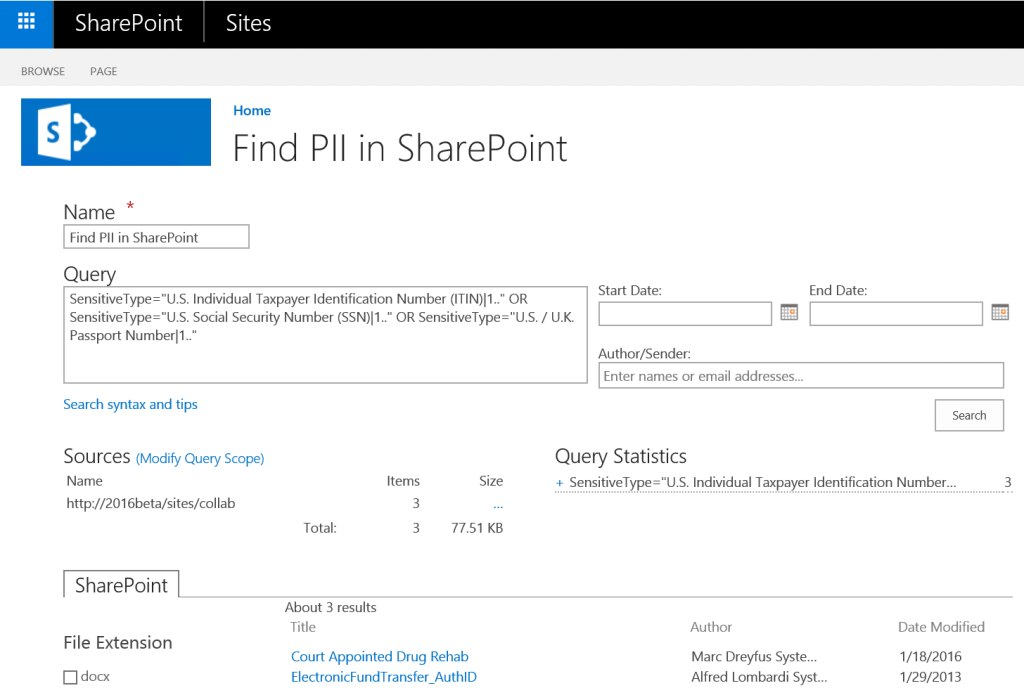
Running a search to find Personally Identifiable Information (PII) in Office 365.
Reporting and Alerts
Along with the DLP queries, you’re able to generate alerts and report to help detect and locate violations. These can be emailed or consumed through the Office 365 Management Activity API. You can specify who receives this information and the amount of details to include within the policies you create. This gives you the ability to route incidents and reports to specific incident management teams while the files are quarantined. However, note that there are no other built-in actions you can take as discussed in this blog post. So you’re essentially able to freeze it in action, but it’ll go into queue of incidents until someone is able to address it.
What More Can You Do?
Office 365’s Compliance Center has some great tools for understanding your data and identifying risk within your data. Being able to provide reports and alerts on violations to your incident management team has long been the standard solution. But depending on the amount of data your users generate and share, even a dedicated team may not be able to address each and every incident quickly enough to mitigate your exposure. That’s where automation comes in.
Think about how we can identify certain types of data based on patterns in information – similar to the DLP queries. We’re also able to append information data to help categorize and allow sorting. And now consider who actually knows the purpose and intent of each piece of data that is created – it’s the business owners. With all of this in mind, we’ve found ways to extend and complement Office 365’s native capabilities in data discovery and protection by providing ways to extensively customize our scans to allow greater coverage, and build in ways to automatically route and resolve incidents based on the type of data, violation, and level of threat.
Learn more about how AvePoint Compliance Guardian Online can protect your Office 365 data, or check out AvePoint Compliance Guardian for on-premises and hybrid protection.

Bettie is a Product Marketing Manager at AvePoint with a healthy obsession over data protection, privacy, and security. She is an addict of technology, gadgets, coffee, and her headphones.


