3 Vital Data Leaks to Plug In Microsoft Teams

Now more than ever people want (and need) to collaborate, and Microsoft Teams makes it very easy to collaborate securely. As a whole, Microsoft 365 has significantly more security options than other collaboration platforms on the market.
However, with all the services offered, one can’t just look at the owners and members of Groups and Teams and know who has access. Between being able to share links directly from every Microsoft 365 application and being able to drop files right into private chats and channels in Microsoft Teams, the distribution of data has never been easier.
While we’re in no way warning against sharing in general (that goes against the entire point of Microsoft 365’s collaborative nature, after all), we are saying that it’s important to know exactly who has access, what they have access to, how they got that access, and so on.
With that in mind, Hunter Willis and Tom Gawczynski got together to discuss five common collaboration risks to mitigate when working in Microsoft Teams. Read on for a summary of the first three, and watch the full webinar for deep dives on all five.
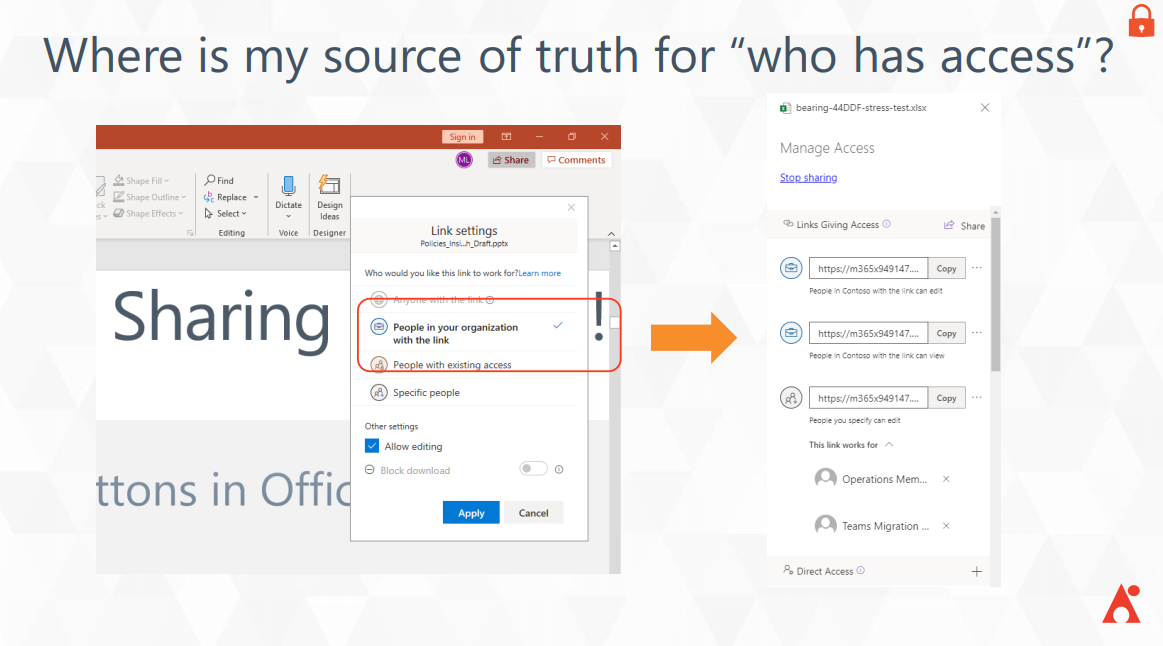
1. Anonymous & Org-Wide Sharing Links
While your first thought as a security-minded individual might be to turn off link sharing permissions altogether, that would significantly hamper your organization’s ability to collaborate as efficiently as possible. Being able to share information is central to the Microsoft 365 platform. That’s why as of February 8, 2021, Microsoft has enabled external sharing by default for organizations that have not yet configured the settings within their tenant.
Though you can go to the SharePoint admin center and turn those settings off, we instead recommend learning where your sharing links are, which ones have access to sensitive information, and who’s accessed those links. Going in and tracking every link can be a handful, but AvePoint’s Policies and Insights lets you set research priorities and have usage reports automatically surfaced to you.
2. Sensitive Data Needle in the Haystack
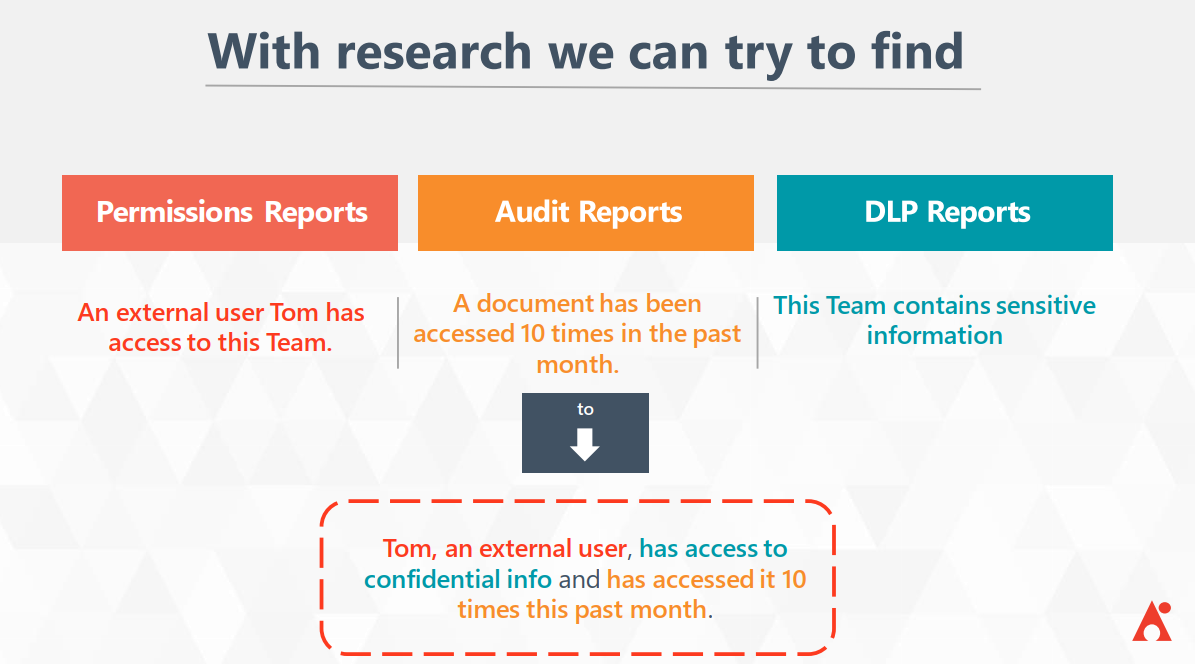
There are over 100 great native tools to help you find different types of sensitive information in Microsoft 365 and generate Data Loss Protection (DLP) reports. However, those reports don’t get into the weeds of who has access to sensitive files or who has accessed those files. Additionally, since the sensitivity levels are defined by how much sensitive content is in each individual biome, you have to do some extra research to find out where your exposure and risk exist.
For instance, if an external user, Tom, has access to sensitive data, how can you tell if he’s accessed it yet? Or how many times has he’s accessed it? And if he’s even supposed to be able to access it? This is where Policies and Insights comes in, as shown below:
Microsoft does provide the basis of what you need for this research with the aforementioned tools, and you can easily manage them via the Security and Compliance Center and set the appropriate retention labels. However, there are two major things we always hear about from our clients with E3 subscriptions:
- Setting those retention labels is something of an all-or-nothing action as the rules you can create are all tenant-wide.
- It’s difficult to manage this as a process because you have to cross-reference your policies and labels and keep track of how they’re affecting your environment and users. There isn’t a ton of context around that without generating more reports.
Whereas E3 sensitivity labels have to be added manually, those with an E5 subscription can automatically apply sensitivity labels within the environment. However, you’re still creating policies and rules that apply everywhere in the environment, and while you can whitelist and blacklist certain locations, that has to be done manually and tracked itself. If you’re trying to grow and want to let your users collaborate, it can all be a bit difficult to keep up with.
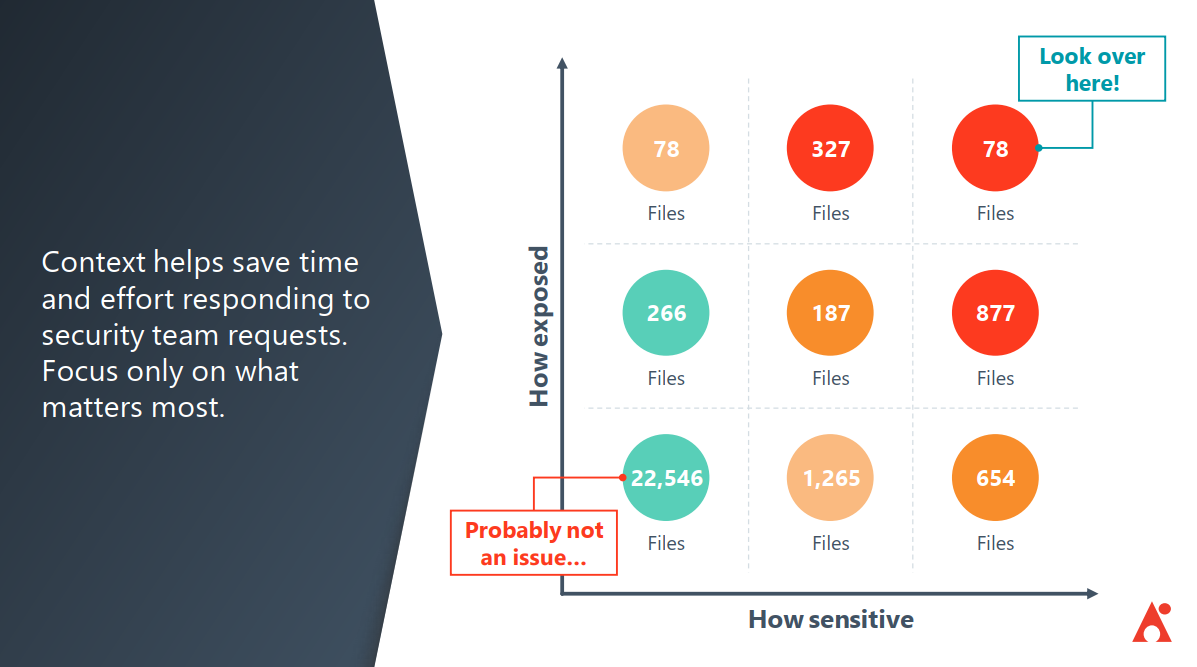
Policies and Insights takes this information and provides context to it. Again, it’s about prioritizing the sensitive documents that have a lot of exposure vs. the ones that can only be accessed by certain people. P&I shows you how many high- and medium-risk items you have and gives you ways to figure out where these items exist, why it’s there, the external users that have accessed those sensitive items in the past.
All of this works towards the ultimate goal of helping you understand the scenarios that create security issues so you can proactively prevent them.
3. Unmanaged External Users
The most common question we’ve heard when clients first approach us about Microsoft Teams security is “How can I make it so that external users and external sharing are enabled exactly where I want it to be?” To answer this, several other questions have to be answered first:
- Who can share access to external users?
- What can be shared externally?
- Which external users can be shared with?
- How can externally shareable links be used?
There are a ton of security settings related to external sharing and adding external users across the Microsoft Teams admin center, SharePoint admin center, Microsoft 365 admin center, and even Azure Active Directory. With so many options across admin centers, however, it can be tricky to determine where to go to resolve specific issues if a situation were to arise.
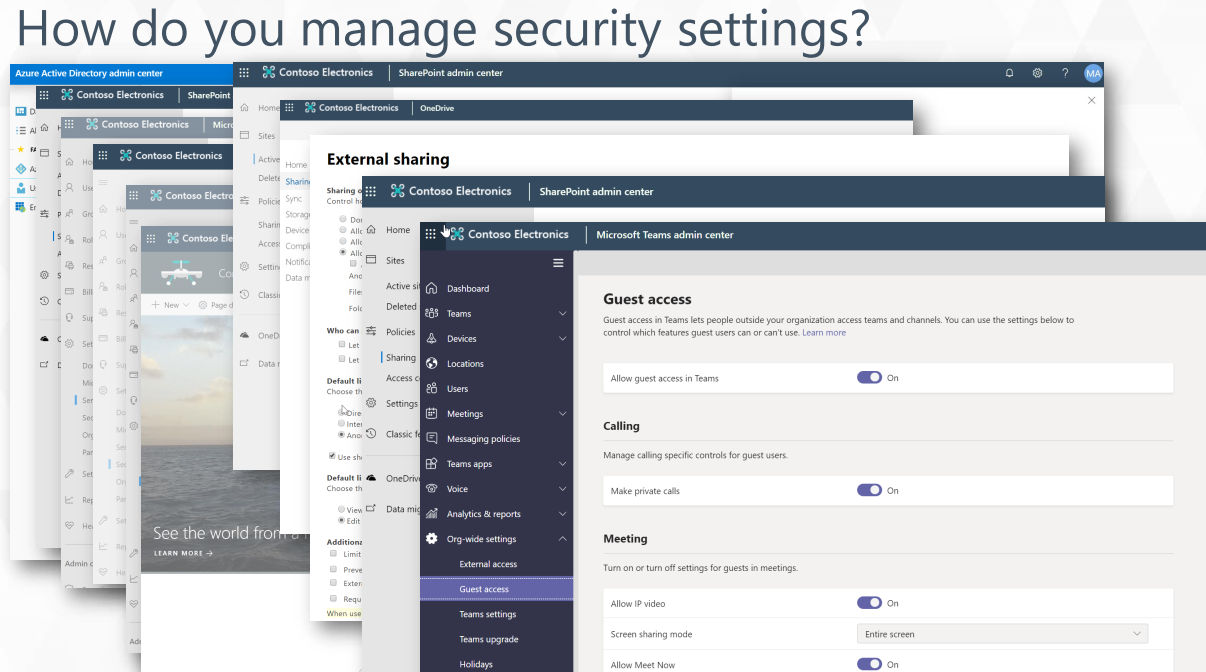
Though it’s easy enough to view which guest users you have in your environment via Active Directory or the Microsoft 365 admin center, you can’t as easily see why they’re in your tenant and what they have access to. Policies & Insights not only helps surface that information, but it prioritizes it so you can address the most pressing issues quickly.
What’s the intersection between the most external users and the most sensitive information in your Microsoft Teams tenant? What domain are those users coming from? Policies and Insights can help you answer these questions by letting you finely tune various access settings, such as which domains are allowed to access certain Teams or what kind of information can be allowed in Teams where certain domains have access.
For a deeper dive into each point here and to learn about two other areas that need to be addressed watch the full webinar here!
Be sure to subscribe to our blog for all the latest Microsoft Teams protection insights.
As the former Content Marketing Specialist for AvePoint, Brent led the strategy and direction of all AvePoint's blog properties.



