Where is Sensitive Data Located in Microsoft Teams?

Note: The following is an excerpt from our ebook, “Right-Sizing Microsoft Teams Management and Security.” You can download it right here!
Permission reports are only part of the Microsoft Teams security and management equation. Microsoft 365 comes with some built-in classification and enforcement capabilities to help users identify and protect their collaboration data. By understanding where sensitive business information lives, we can determine what controls (if any) may be necessary.
Remember, we don’t want to do more than what’s needed — we want to do just enough. By “right-sizing” your approach, you can improve operational efficiency and avoid disrupting valuable collaboration within your organization.
Microsoft Insights
In the Microsoft 365 Security and Compliance Center, you can set up the following:
Sensitivity Labels
These labels can be given a specific scope, priority and policies. As Microsoft mentions in their documentation, “For example, apply a Confidential© label to a document or email, and that label encrypts the content and applies a Confidential© watermark. Content markings include headers and footers as well as watermarks, and encryption can also restrict what actions authorized people can take on the content.”

The downside to sensitivity labels? Unless your organization has an E5 or other advanced licensing, these settings must be manually applied by users, which is not a sustainable or comprehensive method for securing data in Microsoft Teams. Additionally, these labels really only focus on sensitive data, which leaves your general collaborative or sensitive BUSINESS information unmanaged.
Retention Policies
Retention policies ensure that data (documents, instant messages, etc.) can’t be deleted until the appropriate period of time has passed. These policies are applied to the container (email, SharePoint site, OneDrive account, etc.). Retention labels can be applied to content automatically if the content contains specific types of sensitive information. Retention labels can also be used as a condition of DLP policies.
However, continuously creating and keeping track of the labels, policies, and the interactions between them can be a tedious process. The policies are also applied tenant-wide, which may unintentionally impede productive collaboration.
eDiscovery
You can run an eDiscovery search to find your sensitive information. For example, you could run a guided search for a credit card number across your environment. You will likely notice that these scans take quite a while — and that’s for just ONE query against a SINGLE sensitive information type that runs ONCE and is targeted at ONE scope. You’re also now responsible for all the information you return, including next steps on securing that copy of the data.
Data Loss Prevention (DLP)
Microsoft 365’s DLP policy results can provide a better understanding of what documents contain sensitive information and where these documents are located. Policies can also help ensure that documents found by the DLP engine to contain sensitive information cannot be shared externally.
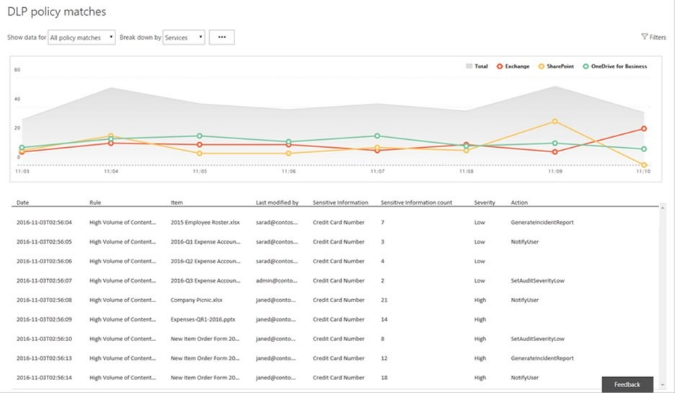
The DLP reports will highlight documents with multiple hits for definition types as more sensitive than documents that only have one hit. The more sensitive information found in one document, the more sensitive the document is considered to be. The challenge with DLP reports is that they identify where the sensitive data is located, but not who has access to the data.
In summary, these are all effective native tools for helping to classify and protect your sensitive data in Microsoft Teams and across Microsoft 365. However, these solutions do not tell a comprehensive story of who is able to access sensitive data. To add that essential context natively, you’ll have to spend hours combining and analyzing several unwieldly reports, only to ultimately gain insights into a single snapshot in time.
Given the rate of collaboration and data generation in the enterprise today, this report will essentially be outdated by the time you’ve completed your analysis.
Have other burning Microsoft Teams governance and security questions you need answered? Download the full ebook here and check out other excerpts below:
- Who Can Access Microsoft Teams and Its Content?
- How to Discover When a Microsoft Team Was Accessed & Why it Exists
For all your Teams security needs be sure to subscribe to our blog.
As the former Content Marketing Specialist for AvePoint, Brent led the strategy and direction of all AvePoint's blog properties.



