For many platforms, external user access is all or nothing. But there is another way.
More organizations are starting to use cloud applications like Box, Dropbox, SharePoint Online, and OneDrive for collaboration.

Files on these platforms can be easily shared to both internal and external users. However, it’s also very easy for users to share sensitive files to external users by accident without realizing the security risk.
Most of these data sources only have on/off switches for external sharing. They don’t have granular and content-aware controls in place.
When it comes to external sharing and security, Microsoft leads the pack with a built-in data loss prevention (DLP) solution. But even their top-notch DLP does not provide deep content analysis, flexible classification and protection methods.
You may also be interested in our other blogs on compliance and external sharing:
- Guest access in Microsoft Teams, is it a big deal?
- How AvePoint’s Compliance Guardian Helps Automate GDPR Compliance
- Automated Data Classification with AvePoint Compliance Guardian
External User Access Best Practices with Compliance Guardian
AvePoint’s Compliance Guardian can help with content-aware secure SharePoint external sharing via:
- Deep content analysis;
- Flexible data classification;
- Numerous protection features; and
- Workflow based incident reporting and remediation.
Deep content analysis and flexible classification
Compliance Guardian has a wide range of deep content analysis technologies to help customers build flexible rules to inspect content.
On top of that, they can also define the data classification code to adjust the risk score according to risk exposure conditions like external sharing. For example:
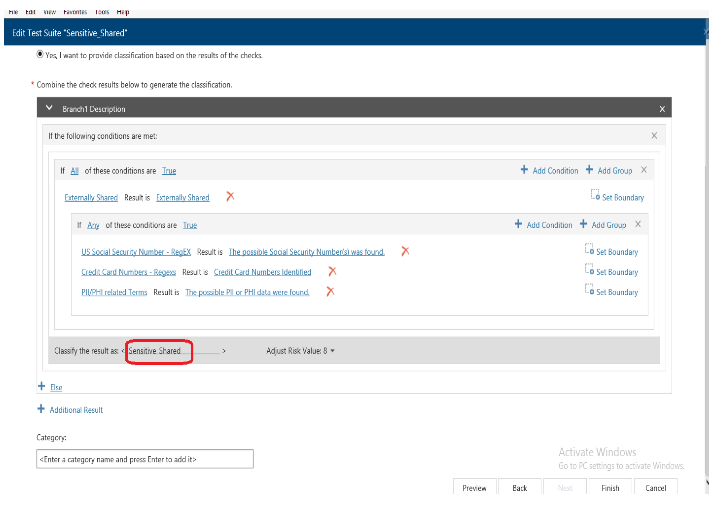
Classification Code Using External Sharing
Policy engine and actions
Compliance Guardian’s policy engine can be used to drive various actions as well as workflow based incidents based on the classification results.
Scans can be scheduled to inspect existing data and ongoing changes. For areas requiring more timely processing, real-time scans can also be used to monitor newly created and modified files.
For existing files, when end users perform “Share” operations on Box, SharePoint Online, or OneDrive, it will also trigger a real-time scan to check whether the shared file has sensitive information.
Various actions can be performed to mitigate the risk for externally shared content. Depending on the needs, one or more of following actions can be performed:
- Change permission: this type of action can be used to reduce the risk by changing the scope of sharing. There are a few different options:
- Make private (Only the Creator and Modifier can see the file, SharePoint Online only)
- Remove permissions of external users
- Remove shared links
- Inherit permissions from parent (SharePoint Online only)
- Restrict to collaborators only (Box only)
- Enable Azure RMS: for content has legit reason to share externally. Azure RMS can also be enabled to ensure security control can travel with the documents. (more on Azure RMS below)
- Send alerts and/or start incident: in addition to actions, alerts and incidents can also be created to track inappropriate sharing events.
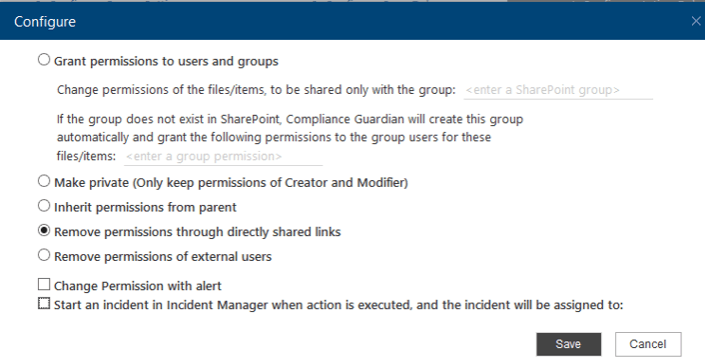
Change Permission Action for SharePoint Online
Incident management
For large environments, it’s challenging to manage the large number of SharePoint security incidents regularly generated. The Compliance Guardian Incident Management Center can help customers handle the challenge in a few ways:
- Workflow based and decentralized incident management to empower data owners.
- Flexible risk score and classification codes can be used to help prioritize and easily identify high risk incidents.
To see these features in action, be sure to request a demo of Compliance Guardian.
Going Further with Perimeter Integration
Compliance Guardian may be used in combination with AvePoint’s Perimeter solution to enhance external sharing with additional controls like:
- Watermarking;
- Web-view;
- Revoking access; and
- Detailed auditing.
Some of the controls are also native in Azure RMS, but Perimeter is easier to use, and doesn't require special clients.
By integrating with Compliance Guardian, Perimeter can perform more intelligent content-aware protection. Flexible conditions can be used to control the content access, based on user's identity and location, together with document metadata or classification.
In addition, Perimeter makes it possible to disable the data source's native insecure sharing and use the Perimeter's secure sharing function instead. This way you can have total control over sharing with content-aware and context-aware rules.
Perimeter and CG Integration
To see these features in action, be sure to request a demo of Perimeter.
Azure RMS Integration
Azure RMS is a powerful tool to protect data: With RMS, security travels with the content. It can help to enforce data protection after data leaves the source system to end-point and even external users.
Thinking of RMS as a control tool to protect files, Compliance Guardian’s RMS support can help in the following areas:
Policy driver
Compliance Guardian can be considered a policy driver to enable and update RMS setting based on various conditions, like flexible metadata, content and context aware rules.
Expand RMS protection scope
As Compliance Guardian already supports many different data sources, RMS can be enabled on these systems too, for example, Box and Dropbox.
As a result, a more complete end-to-end security control can be achieved, more than just Office 365.
Simplifies RMS permission management
Many RMS-aware applications rely on RMS templates. These RMS templates are pre-defined permission settings created by admins and published in Azure AD.
It’s more suitable for scenarios that the RMS audience are static (for example, quarterly reports to board members; internal-only documents). But it’s not convenient for more ad-hoc collaboration situations (requiring admin’s involvement is difficult, also the combination of permission settings could be endless).
Compliance Guardian can help simplify RMS permission management.
When configuring Azure RMS protection in Compliance Guardian, users can select from following options:
- Use existing Azure RMS templates: this option allows users to use RMS templates pre-created by administrators. It’s useful for fixed collaboration scenarios where users’ roles are fixed. For example, quarterly reports, board meetings, etc.
- Grant permissions directly to specific users: in this option, RMS permissions can be defined without using pre-created RMS templates.
- Use data source permission settings: native RMS permission management is not easy for ad-hoc collaboration, especially outside of Microsoft eco-system (normally users need to configure permission in both data source and RMS manually). This option (Box only) will help to simplify the RMS permission management.
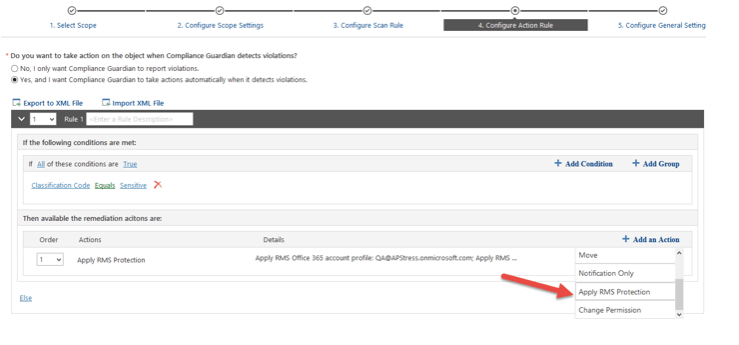
Apply RMS Protection Action
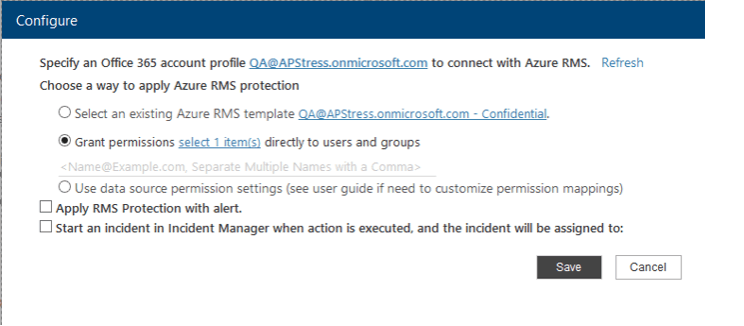
RMS Action Settings for Box
Access secure external sharing for your cloud environment
As you can see, enabling sharing for external users in SharePoint, Office 365, Box, Dropbox or other cloud environments doesn’t have to be an all or nothing proposition.
Talk to an expert about how your organization can increase its control over sharing with external users to ensure seamless compliance!

