In today’s digital age, cybersecurity is critical, especially for organizations in the defense sector. The recently published Cybersecurity Maturity Model Certification (CMMC) Final Rule establishes a framework to enhance cybersecurity across the United States Defense Industrial Base (DIB) as a response to the evolving threat landscape.
I had an opportunity to chat with John Federline, Senior Account Executive, Enterprise Sales at AvePoint, about the overlap between data security and compliance, the challenges customers face when building a compliant environment, and how data security can give organizations a unique advantage in the market.
TL;DR: A comprehensive data security approach can help organizations in the DIB mitigate risk and extra costs associated with addressing CMMC compliance. AvePoint’s Control Suite can help Department of Defense (DoD) contractors maintain confidence in protecting their sensitive data while ensuring their data security is top of mind for IT professionals and other key stakeholders.
High-Level Features of the CMMC Final Rule
1. Tiered framework. The type(s) of data organizations handle will determine which of the three maturity levels will apply, allowing them to tailor security measures based on their specific needs.
2. Third-party assessment. Certification now requires objective evaluations from accredited assessors, ensuring compliance with security standards. This is one step further than Defense Federal Acquisition Regulation Supplement (DFARS) 7012, which required self-attestation to the NIST 800-171 requirements.
3. Supply chain security. The focus extends to securing the entire supply chain, acknowledging that vulnerabilities can arise at any level.
Why Security Matters for CMMC
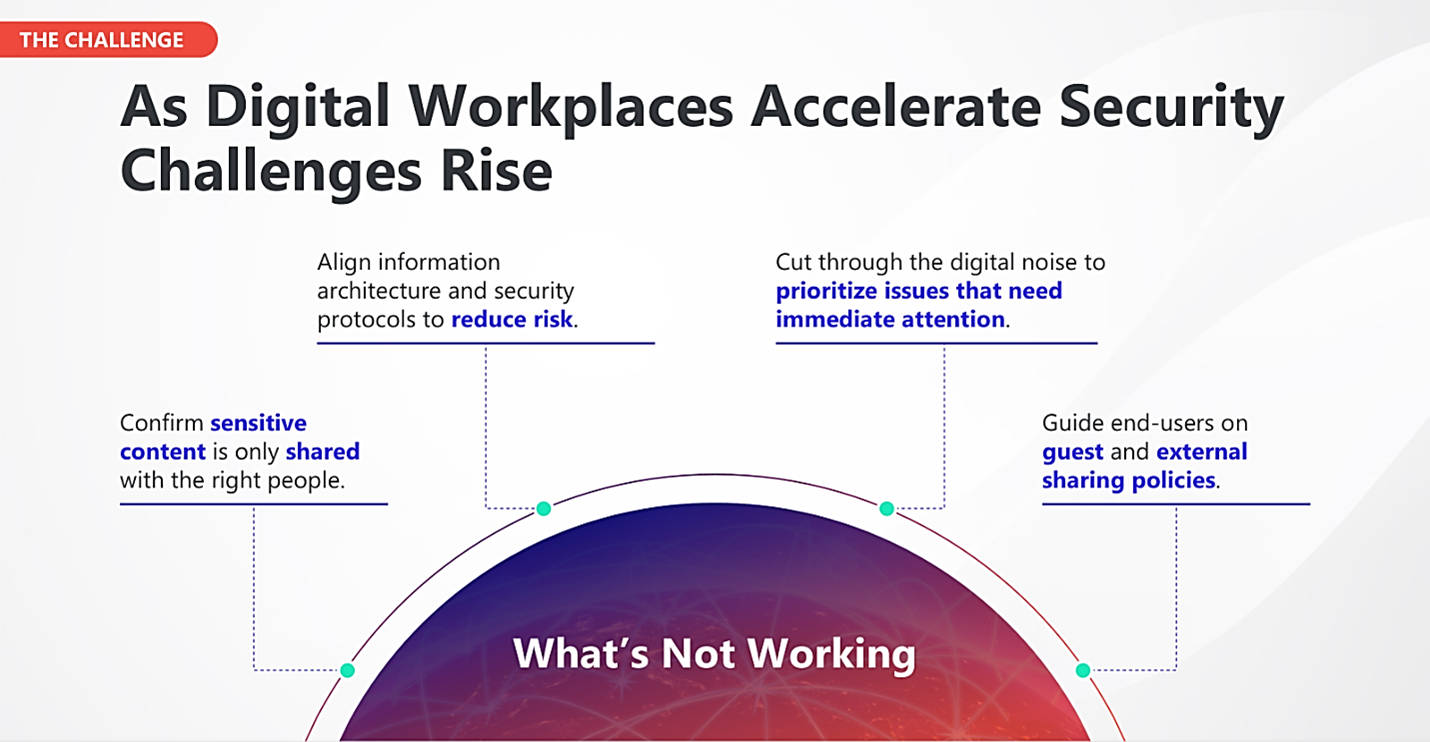
Because CMMC is not only about compliance, but overall improvement of your security posture, it is critical to understand a few reasons why security matters just as much as compliance for DoD contracts. Here’s a short list:
1. Protecting sensitive data. With vast amounts of sensitive information at stake, robust security measures prevent breaches that could compromise national security.
2. Mitigating risks. Proactive cybersecurity practices help organizations identify and address potential threats before they escalate.
3. Building trust. Demonstrating a commitment to cybersecurity fosters trust among clients and partners, which is essential for long-term relationships.
4. Enhancing resilience. Strong security practices not only protect against breaches but also ensure organizations can respond effectively to incidents.
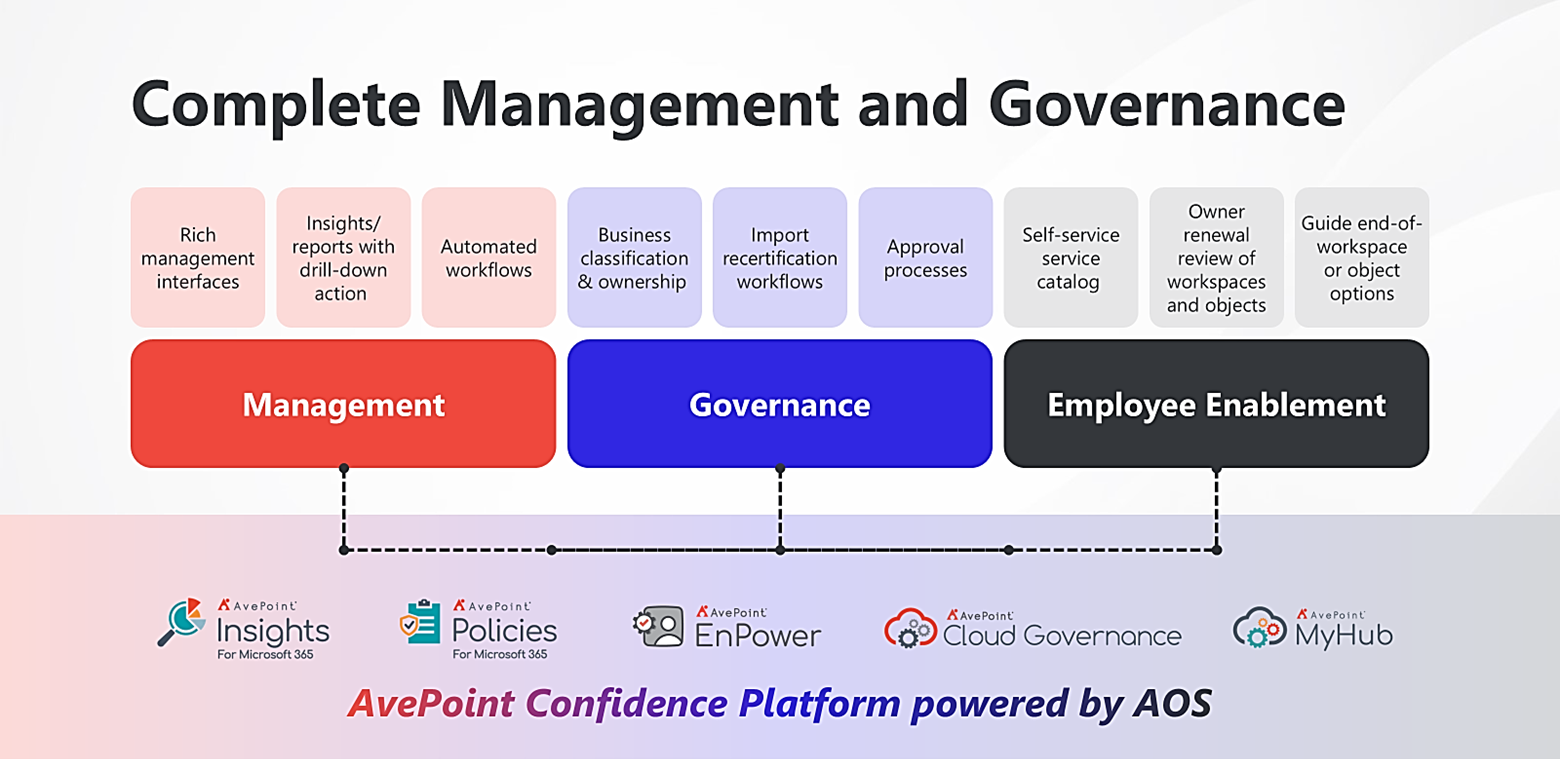
How AvePoint’s Control Suite Supports CMMC Compliance
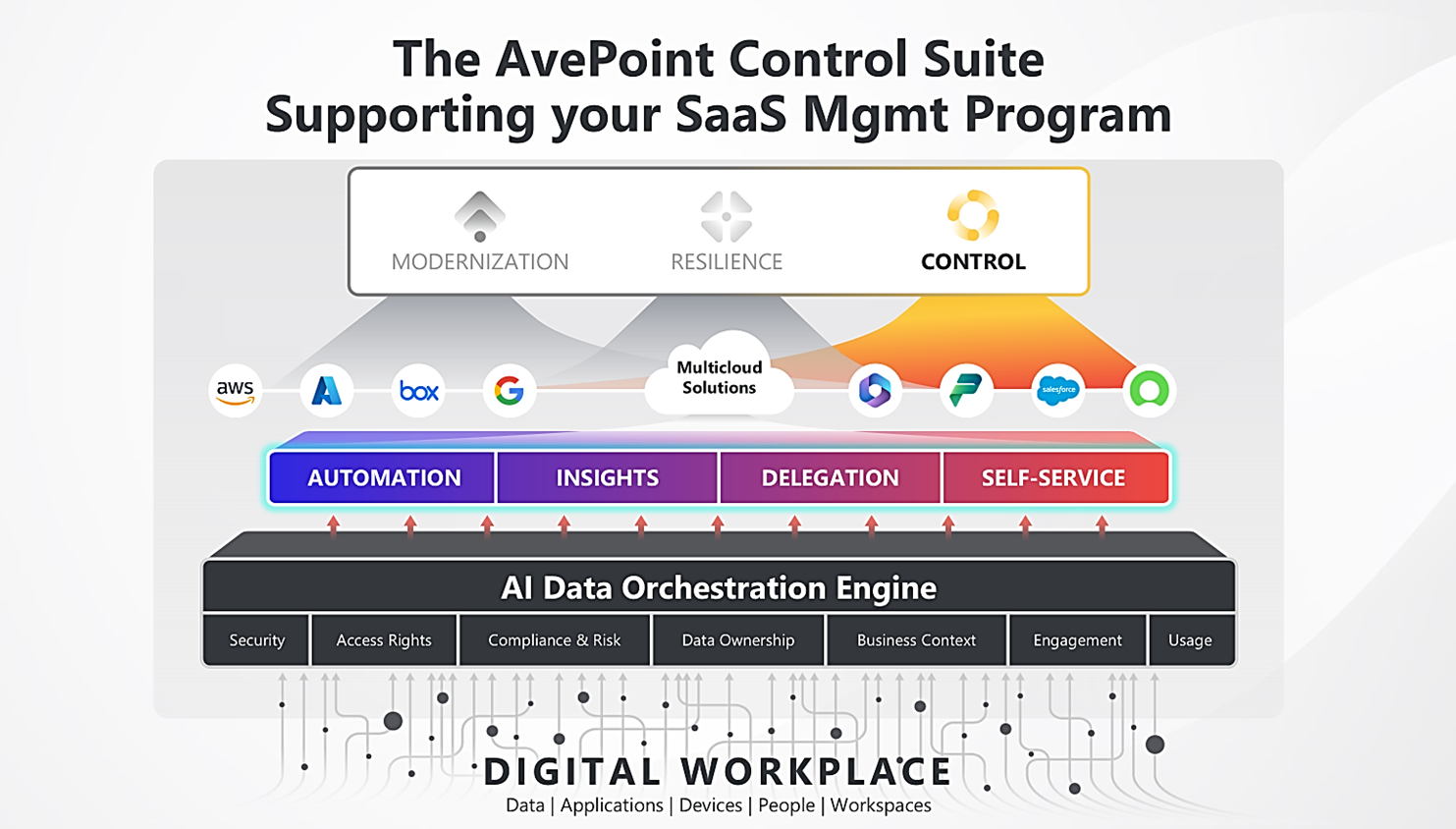
1. Comprehensive data governance. AvePoint’s Control Suite enables organizations to gain visibility into their data landscape. With robust data governance capabilities, it helps contractors identify, classify, and protect sensitive information according to CMMC requirements. This ensures that only authorized personnel have access to data such as CUI, significantly reducing the risk of data breaches.
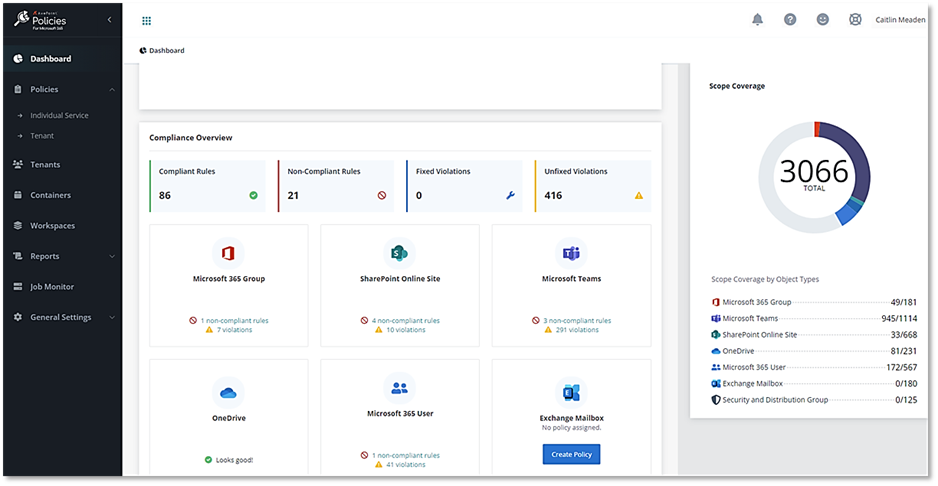
2. Automated compliance management. Compliance with CMMC involves ongoing monitoring and assessments. AvePoint’s Control Suite automates many of these processes, providing real-time insights into security posture and compliance status.
3. Risk assessment and mitigation. The Control Suite includes tools for conducting comprehensive risk assessments. Contractors can identify vulnerabilities and prioritize remediation efforts effectively, addressing potential risks before they escalate.
4. Incident response capabilities. In the event of a security incident, AvePoint’s Control Suite equips organizations with the tools needed for effective incident response. This includes automated workflows for managing incidents and ensuring that appropriate actions are taken promptly.
5. Documentation and reporting. Compliance with CMMC necessitates thorough documentation of security practices and policies. AvePoint’s Control Suite simplifies the documentation process, allowing contractors to easily generate reports that demonstrate compliance.
See how AvePoint helps organizations simplify compliance and reduce risk. Watch our AvePoint Innovates on-demand to explore the newest capabilities built for mission success.
Steps for DoD Contractors to Leverage AvePoint’s Control Suite
1. Conduct a self-assessment. Identify gaps and areas for improvement against your current cybersecurity posture; CMMC requirements contractors to meet NIST 800-171 standards — start with the 320 assessment objectives listed in NIST 800-171.
2. Implement data governance policies. Utilize the Control Suite to classify and manage sensitive data effectively, ensuring compliance with access control requirements.
3. Automate compliance monitoring. Set up automated compliance checks within the Control Suite to maintain ongoing visibility into your security posture.
4. Enhance risk management. Use risk assessment tools to identify vulnerabilities and develop a prioritized remediation plan.
5. Train your workforce. Leverage AvePoint’s training resources to educate employees about CMMC compliance and foster a culture of security.
6. Document and report. Streamline your documentation process with AvePoint’s reporting capabilities to ensure that you can easily provide evidence of compliance as you prepare for an assessment.

Be sure to follow AvePoint Public Sector on LinkedIn as well as the AvePoint YouTube channel for more content on reducing risk and costs associated with protecting sensitive data.
AvePoint Public Sector exists to empower organizations to maintain trust with their data — we do that by providing a comprehensive data security platform: the Confidence Platform.
You can learn more about the Confidence Platform here.


